2016 Joint International Conference on Artificial Intelligence and Computer Engineering (AICE 2016) and International Conference on Network and Communication Security (NCS 2016)
ISBN: 978-1-60595-362-5
A Security Audit Module for HBase
Rui YANG
1,a, Xin LIU
2,b, Hai-Tao WANG
3,c, Lin DAI
1,d1Beijing Institute of Technology, Beijing, China
2Beijing Electronic Science and Technology Institute, Beijing, China
3Power Construction Corporation of China, Ltd., Beijing, China
a2120131081@bit.edu.cn, b1810119456@189.cn, cwanght@powerchina.cn, ddailiu@bit.edu.cn
Keywords: NoSQL, Security Audit, HBase.
Abstract. NoSQL databases provide us with highly available and highly scalable data storage
solutions. During the operation on huge amounts of data, security issues have become more and more important. Security audit is an important feature for NoSQL database security. An audit module will monitor and record users’ accessing activity on the database. Thus we can identify risks such as illegal operations, right violation, etc. We designed a security audit module to enhance security for HBase. We get accessing information by defining hook function in coprocessor. Then we implement a flexible set of rules to filter logs. The evaluation shows that the system can record required accessing information thus improves security of HBase.
Introduction
A traditional database system is based on relational model. However, with the rapid development of Internet, the size of data grows every day, which makes relational database unable to process this kind of big data. On the other hand, non-relational databases dramatically grew to meet the requirement from big data. These databases are commonly known as NoSQL (Not Only SQL), clearly marking them different from the traditional SQL databases[1]. Processing a vast amount of data requires speed, flexible schemas and distributed storage. This data is typically non-structured, complex and does not fit well to relational model. NoSQL databases became the preferred choice for operating big data. They claim to satisfy these requirements[1, 2].
The main promoters of NoSQL databases are Web 2.0 companies with huge, growing data and infrastructure needs, such as Amazon and Google. The Dynamo technology developed at Amazon[3] and the BigTable distributed storage system developed at Google[4] have inspired many of today’s NoSQL applications. Compared with traditional relational databases, NoSQL database provides us with highly available and highly scalable data storage solutions. Apart from scalability and performance, data security is probably one of the most difficult challenges faced by the NoSQL databases now-a-days. These databases are not initially designed with considering security as an important feature. Therefore, consumers have to protect these databases themselves by using third party tools and services[5].
Database Auditing refers to the monitoring and recording of actions performed by database users[6]. Auditing could be helpful in the identification of attacking trace or password cracking attempts[7]. Database administrators (DBAs) should use regular auditing or fine grained auditing techniques for detection and monitoring of unauthorized access to data[8].
In this paper, we firstly analyze the security mechanism of one of the most popular NoSQL databases, HBase. According to the mechanism, a security audit module based on coprocessor is implemented. This module will help HBase database to enhance its security. Meanwhile, similar module could be extended to other NoSQL databases.
The rest of this paper is organized as follows. Section 2 briefly introduces related works about NoSQL security. Section 3 analyzes the security mechanism of HBase. The security audit module is designed in Section 4. Section 5 is evaluation. Section 6 concludes this paper.
Related Work
HBase is a NoSQL database developed on top of Hadoop Distributed File System (HDFS). It is a distributed fault-tolerant and highly scalable, column-oriented NoSQL database. HBase uses distributed configuration, replication and write-ahead-logging (WAL) mechanisms to recover from automatic failovers. Authorizations in HBase are managed by ACL (Access Control Lists) or coprocessors. HBase also provides logging support up to data node level. However, auditing and monitoring security features are absent in HBase[5].
MongoDB [9] is an agile database built for scalability, performance and high availability. When MongoDB was initially designed, security was not a primary concern. As a result, auditing did not receive adequate attention. Several audit techniques are available internally in MongoDB such as oplog, diaglog and profiler.
Cassandra is a database management system designed to handle very large amounts of data spread out across many servers while providing a highly available service with no single point of failure[10]. It doesn’t support inline auditing and needs an audit feature if it stores valuable data.
Beside above NoSQL databases, there are other ones such as Redis[5], CouchDB[5] and so on. These NoSQL databases do not support audit at all or just support limited audit function. As a conclusion, security audit module is an important and urgent feature for NoSQL databases.
Security Mechanism of HBase
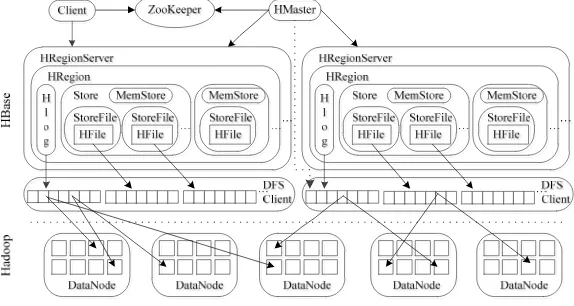
[image:2.612.161.448.489.642.2]For coherence, we introduce the framework and security mechanism of HBase briefly. Figure 1 shows the general architecture of HBase. It is composed by many parts, including HMaster, HRegionServer, Regions, Zookeeper and so on.
Figure 1. Architecture of Hbase.
serving and managing regions. In a distributed cluster, a RegionServer runs on a DataNode. Regions are the basic element of availability and distribution for tables[11].
Coprocessor[11] is an important mechanism in HBase, which allows developers to insert custom code in servers. It contains two modules. One is observer and the other is endpoint.
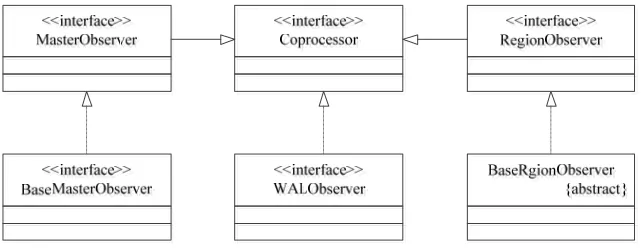
[image:3.612.146.467.176.301.2]Observer is similar to the trigger of SQL database. It defines a number of callback functions, also known as the hook function. These functions will be executed when a specific event occurs. And these events including events generated by users and events generated from server. Hierarchy of Observer is shown in Figure 2.
Figure 2. Class Hierarchy of Coprocessor.
MasterObserver provides hooks for DDL operation, such as deletion and modification on table. RegionObserver provides the facility to execute your code when the events on region are triggered. Most common examples include 'preGet' and 'postGet' for 'Get' operation and 'prePut' and 'postPut' for 'Put' operation. WALObserver provides hooks for WAL related operation.
Through the coprocessor mechanism, HBase implements access control. In HBase, class
AccessController extends BaseRegionObserver and implements MasterObserver,
RegionServerObserver and CoprocessorService. Every operation is checked by corresponding 'pre' methods. In this way, the access control of HMaster and HRegion based on ACL is realized.
Beside access control, according to the working location of coprocessor, we can use hook functions to do many things, including security audit. Thus we argue that MasterObserver and RegionObserver are good option to implement security audit module for HBase.
Implementation
Audit Rules
In order to implement an applicable security audit system, we need a set of flexible audit rules. It should allow administrator to select the appropriate security level according to the safety requirements.
In our security audit module, audit rules are divided into two parts, namely audit level and audit condition. Audit level contains coarse-grained audit and fine-grained audit. Coarse-grained audit concentrates on table level operations. Fine-grained audit concentrates on CURD (create, update, read and delete) operations. Audit condition contains table condition and CURD condition. Table condition means that the system can audit operation on specific table. Through CURD condition, we can choose which kind of CURD operation to audit. By setting the audit conditions, the system can meet different audit requirements.
Storage
Evaluation
To evaluate the proposed method, we implemented the whole set of hook functions. Figure 3 shows the sequence of 'Get' method. We can define 'auditGet' in the stage of 'preGet'. Others audit methods are similar to 'auditGet'.
Figure 3. Data Stream of 'Get'.
Table 1. Coarse-grained Audit.
IP Level Table Operation RowKey Column Time
192.168.3.21 Table student Create Table Null Null 2015-11-12 14:56:40
192.168.3.21 Table student Null Null Null 2015-11-12 14:57:12
192.168.3.21 Table student Disable Table Null Null 2015-11-12 14:58:30
192.168.3.21 Table student Delete Table Null Null 2015-11-12 14:58:40
192.168.3.21 Table teacher Create Table Null Null 2015-11-12 14:59:04
We deploy the module to HBase v0.96. We run a large set of operations on HBase, including 'create', 'put', 'get', 'delete', 'drop' and so on. Table 1~4 show a faction result of coarse-grained audit, fine-grained audit, table condition with fine-grained audit and CURD condition with fine-grained audit respectively.
Table 2. Fine-grained Audit.
IP Level Table Operation Row Key Column Time
192.168.3.21 Table student Create Table Null Null 2015-11-12 14:56:40
192.168.3.21 CURD student Put 21001 info: grade 2015-11-12 14:57:12
192.168.3.21 CURD student Delete 21001 info: class 2015-11-12 14:57:55
192.168.3.21 Table teacher Create Table Null Null 2015-11-12 14:59:04
Table 3. 'Teacher' as Target Table in Table Condition with Fine-grained Audit.
IP Level Table Operation Row Key Column Time
192.168.3.21 Table teacher Create Table Null Null 2015-11-12 14:59:04 192.168.3.21 CURD teacher Put 11001 info: name 2015-11-12 14:59:18 192.168.3.21 CURD teacher Put 11001 info: course 2015-11-12 14:59:28
192.168.3.21 CURD teacher Get 11001 info: name info: course 2015-11-12 14:59:50
As can be seen from above audit results, we know that the security audit module works well. The module also support combination of audit level and audit condition, which reflects the flexibility of the audit policy.
Table 4. Insert Operation as Target Operation in CURD Condition with Fine-grained Audit.
IP Level Table Operation RowKey Column Time
192.168.3.21 CURD student Put 21001 info:name 2015-11-12 14:57:01 192.168.3.21 CURD student Put 21001 info:grade 2015-11-12 14:57:12 192.168.3.21 CURD student Put 21001 info:class 2015-11-12 14:57:24 192.168.3.21 CURD teacher Put 11001 info:name 2015-11-12 14:59:18
192.168.3.21 CURD teacher Put 11001 info:course 2015-11-12 14:59:28
Conclusion
We implemented a security audit module to enhance security for HBase based on coprocessor framework. The system has a set of flexible audit rules. It supports coarse-grained audit, fine-grained audit and conditional audit. The results show that the system can meet different audit requirements. In the future, we will try to apply our audit module to other NoSQL databases.
Acknowledgement
This paper is partially supported by NSFC: 61201351, 60803050.
References
[1]Yishan Li and Manoharan S., A performance comparison of SQL and NoSQL databases, 2013 IEEE Pacific Rim Conference on Communications, Computers and Signal Processing (PACRIM). (2013).
[2]Parker Zachary, Poe Scott, Vrbsky Susan V., Comparing NoSQL MongoDB to an SQL DB, 51st ACM Southeast Conference. (2013)
[3]DeCandia Giuseppe, Hastorun Deniz, Jampani Madan, et al., Dynamo: Amazon's highly available key-value store, Proceedings of the 21st ACM Symposium on Operating Systems Principles. (2007). [4]Fay Chang, Dean, J., et al., Bigtable: A Distributed Storage System for Structured Data, ACM Transactions on Computer Systems. 26 (2008).
[5]Zahid A., Masood R., Shibli M.A., Security of sharded NoSQL databases: a comparative analysis, 2014 Conference on Information Assurance and Cyber Security (CIACS). (2014).
[6]Oracle Security Guide 11g Release on http://docs.oracle.com /en/.
[8]Oracle Security Guide 10g Release on http://docs.oracle.com /en/.
[9]Murugesan P., Ray I., Audit Log Management in MongoDB, 2014 IEEE World Congress on Services (SERVICES). (2014).
[10]Okman L., Gal-O N., Gonen Y., et al., Security Issues in NoSQL Databases, 2011 International Joint Conference of IEEE TrustCom-11/IEEE ICESS-11/FCST-11. (2011).