Intrusion Detection System using Log Files and Reinforcement Learning
Full text
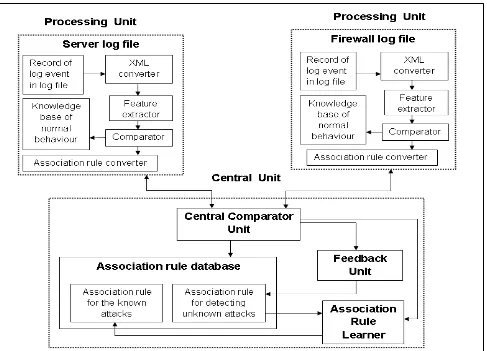
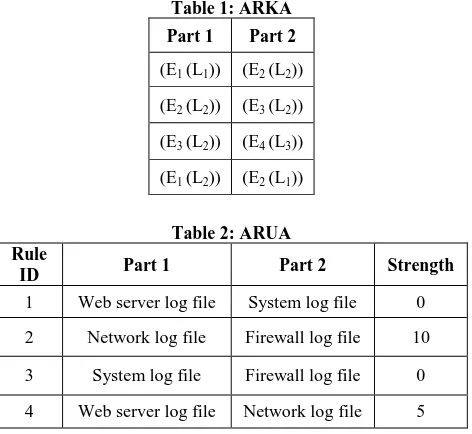
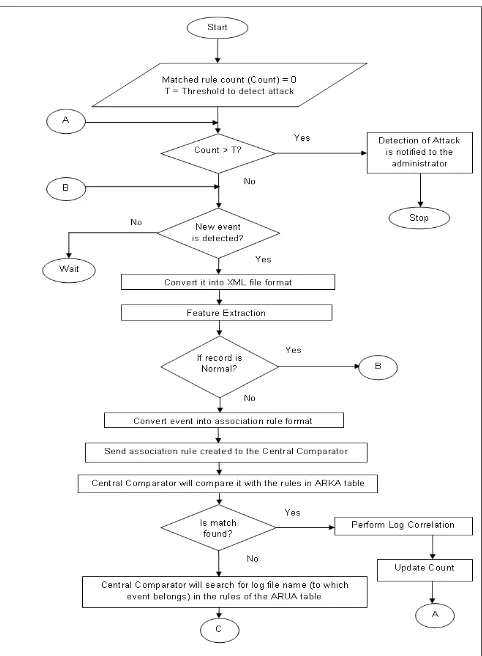
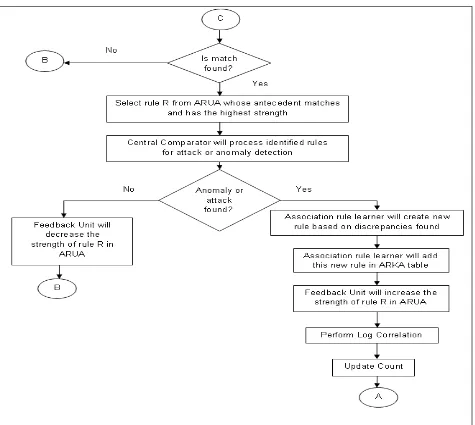
Figure
Related documents
Furthermore, most AtNHX1 -expressing cotton plants displayed higher rates of CO 2 assimilation (A) that were associated with higher stomatal conductance than wild-type plant
Study of relation between coping ways with individual’s characters and mental health in infertile couples who refer to Yazd infertility center.. Tehran, Tarbiat
With the paucity of PBM programmes tailored for neonates, this project aims to ensure best practice in neonatal transfusion based on PBM Module 6 and NSQHS Blood Management
• Fare clic per modificare gli stili del testo dello schema " – Secondo livello" • Terzo livello " – Quarto livello " » Quinto livello
Using multiple regression analysis, it was established that improved transport infrastruc- ture, communication infrastructure, water and waste infrastructure, exchange rate,
Learning from the examples of successful blogs by elementary teachers, four common types of classroom blogs with accompanying examples are shared: Classroom News Blogs, Mirror Blogs,
The interparticipant means of these are shown in Table 1, where ``cued'' versus ``uncued'' visual targets refer to those on the same side of external space as the tactile cue (thus
Somatic tissues of some kangaroo species also express a PGK isozyme that stains more faintly after electrophoresis than PGK-A and exhibits the same electrophoretic mobility