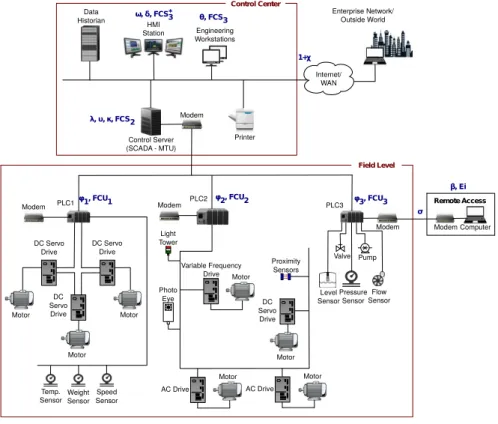
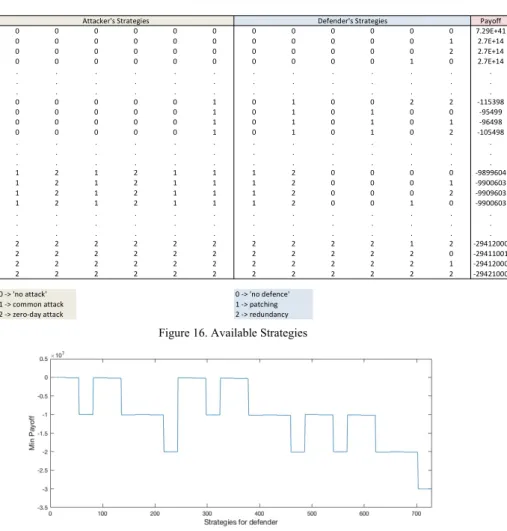
Critical infrastructure cyber security risk management
Full text
Figure
![Figure 1. Beer’s Viable System Model [9].](https://thumb-us.123doks.com/thumbv2/123dok_us/599692.560023/3.892.269.624.545.877/figure-beer-s-viable-system-model.webp)



Related documents
We spoke with the doctor who said, “I really like working in this hospital, it’s like a family.” The comment cards we collected mainly had positive responses about staff and the
Instead of actively trying to shape identity norms or capture social capital for their fellow group members, people also simply assess laws, and their interactions with legal
Purpose – The purpose of this paper is to explore barriers and benefits of establishing relationships between humanitarian organizations (HOs) and logistics service providers (LSPs)
With respect to entry, the general rule is the following: alien workers from outside the EU must be hired in their countries of origin when they are hired for the first time,
These values can be determined by measuring the input impedance of the driver, near the resonance frequency, at small input levels for which the mechanical behavior of the driver
Brady and Wu (2010) extend this result to two-person groups by testing different patterns of communication and showing that small changes in decision-making procedures
With respect to interactions involving the promotion of Pfizer products, Sales Colleagues must adhere to the policies set forth in the Orange Guide Chapter 2: Detailing to HCPs,
To this end, we compared normal hearing older adults to a middle-aged control group during spectral speech processing in a repeated measurement design that allowed for the evaluation