Public Auditing Using Proxy Resignatures on Efficient User Revocation in the Cloud
Full text
Figure
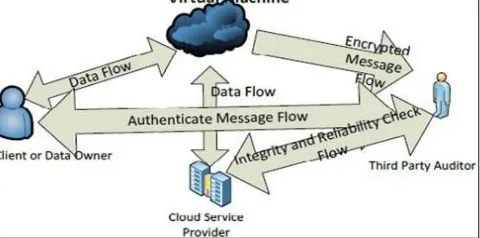
Related documents
Generally, studying class groups of real quadratic elds is much more dicult than studying class groups of imaginary quadratic elds, primarily because real quadratic domains have
Conclusions: In this study, patients with isolated shaft fractures of the upper extremity tend to have a more favorable outcome in comparison with combined to isolated
Low energy particle experiments?electron analyzer (LEPe) onboard the Arase spacecraft Kazama et al Earth, Planets and Space (2017) 69 165 https //doi org/10 1186/s40623 017 0748 6 F U L
DAVIDE TRAPANI – A MONITORING METHOD FOR AFTER- EARTHQUAKE DAMAGE EVAUATION OF BUILDINGS ACCURACY DEMAND. DEFINITION ACCURACY DEMAND
Many metabolic disease risk factors, including insulin re- sistance begin to accumulate in young adulthood [15]. Consequently, there is an acute need to establish a sensi-
Although both districts are accessible only by concessionaire ferry services or private boat, most visitors access the island via concessionaire ferry services (up to
A global finite element model is used for investigation of the seismic response of the whole building structure.. This model describes all main parts of the reactor
As such, what ends up happening is that one of the later age ranges (suppose the 50 target for this example) already has a model output above the desired target. 3) The