Privacy Aware using Temporal Role Based Access Control Model
Full text
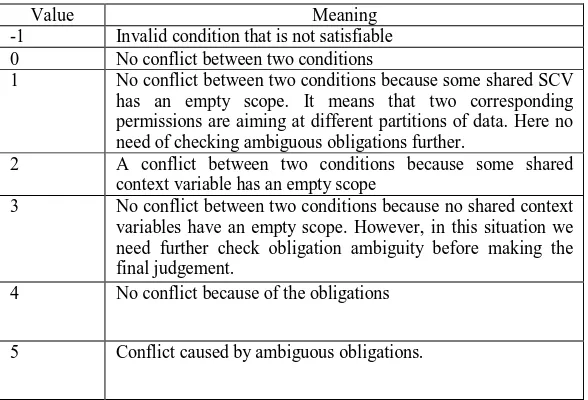
Figure


Related documents
The Untold Costs of Subprime Lending: Examining the Links among Higher-Priced Lending, Foreclosures and Race in California. Carolina Reid and
Cumin, in India popularly called as Jeera is the dried fruit of small herbaceous plants belongs to the Apiaceae family.. It was popular even during the Biblical times as an
Diamond Jubilee 3R 5L Diamond Line Frenzy Diamond Safari 3R 27 Way Diamond Solitaire Deluxe 3R 5L Diamond Spinner 5R 25L Diamonds And Devils 5R 25L Diamonds In The Rough
If there are information manage- ment programs at local colleges or universities, ask program officials to write to the transition board mem- bers, emphasizing the essential nature
In this study, enzymatic dehydrogenative polymerization of dilignols, guaiacylglycerol-β-coniferyl ether ( I ), dehyd- rodiconiferyl alcohol ( II ), and pinoresinol ( III ),
Trafficking in Human Beings Conference 12-14 November 2014) tasks are directed to contrast all kind of transnational organized crimes (drugs - related crime, people
In order to create all information needed in the distribution network the setup of activities is based upon that the parts are entering the distribution network at the
CA No hold conference - autodial Combined feature, not supported -- CCOS Controlled class of service Change COR Access Code FAC CFW Call forward all calls