3 Dimensional Sterling Conception for System Security
Full text
Figure
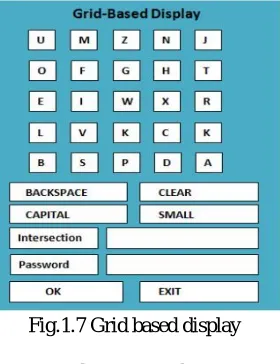
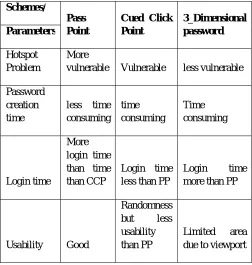
Related documents
Since most of the existing feature selection methods need data to be discrete, the first proposed approach consists of a combination of a discretizer, a filter method and a
Murray River Project – Canadian Kailuan Dehua Mines / HD Mining International Corp. Gething Project - Canadian Kailuan
This study’s central thesis is based upon a qualitative research project which captured and analysed the focus group conversations of fifty-two Black British Pentecostal women of
Having different solvers like buoyantSimpleFoam that is used for steady-state buoyant, turbulent flow of compressible fluids for ventilation and heat transfer, and
Nonetheless, use of both approaches in the ASU survey is motivated by the attempt to solve a common problem: the possibility of mis-representation of data by accepting
In contrast, if the family background variables are unimportant, then social mobility is considered high, because teenagers from different backgrounds have similar
Customized chess engine is used to implement chess rules, to evaluate the board position during the game and to compute the next move of the robot using the alpha-beta
Verizon customers may want to consider canceling their service with Verizon before Allied Telesis turns on your service to prevent getting double billed.. If I have to cancel