Virtual Private Network Security
Full text
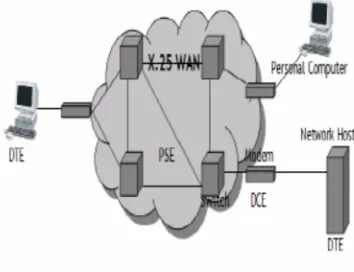
Figure
Related documents
Vegetable garden not and bell and howell solar animal repeller instructions said to exterminate a powerful ultrasonic waves so do not hear the pest control and not!.
In this task, you need to create a tunnel between a computer and a gateway, allowing the computer to access the private network that is connected to the gateway.. To demonstrate
Interface VoIP Voice over Internet Protocol EoC Ethernet over Copper VPLS Virtual Private LAN Service EPL Ethernet Private Line VPN Virtual Private Network EVPL Ethernet Virtual
Handleiding een Virtual Private Network (VPN) verbinding opzetten Versie 1.3 – 18-11-2009.. 1 Setting up a Virtual Private Network (VPN) connection
Virtual Private Network (VPN) technology are used to attend to the security over the external network to make sure that the Customer can communicate with Telenors mobile network in
IPTV is a service that provides television programming services (sports, news, movies, etc.) and other interactive entertainment content (music, games, advertising)
If you are using VPN with your Windows computer and have difficulty accessing certain applications, or are being prompted to provide a password for applications you don’t
Each router provides optimal network security via features such as Virtual Private Network (VPN) tunnels, IP Security (IPSec), Point-to-Point Tunneling Protocol