AIR FORCE
AUDIT AGENCY
AUDIT REPORT
F2008-0003-FB4000
22 February 2008
AIR FORCE PORTAL
ACCESS AND RIGHTS
Executive Summary
ii
INTRODUCTION The Air Force Portal (AFP) provides authorized Air Force users with essential online access to timely, accurate, and trusted information and information technology services over a secured network. The AFP serves as the entry point to the Air Force’s worldwide “Intranet” using a standard web browser. It is avail-able to users anytime and anywhere an Internet connection is available from “.com” or “.mil” connections. Access, based on duty status, allows entry into the AFP while rights, based on assigned duties and responsibilities, define the nature and extent of access. Therefore, AFP administrators may grant elevated rights to personnel with information
management responsibilities in the AFP. As of 1 June 2007, the AFP had over 906,000 registered users.
OBJECTIVES We audited AFP access and rights because their
effective management is essential to the security of Global Combat Support System-Air Force (GCSS-AF) and Air Force information. Our objective was to deter-mine whether the Air Force effectively controlled user access and rights to the AFP. Specifically, we
determined whether AFP access and rights were restricted to appropriate personnel.
CONCLUSIONS The Air Force could improve management and control
of AFP user access and rights. Specifically:
• Major command (MAJCOM) and installation
administrators did not effectively maintain access control over the AFP. Access must be controlled to protect the confidentiality, integrity, and availability of sensitive and critical
information. (Tab A, page 1)
• The AFP Designated Approving Authority (DAA) did not develop a role-based access scheme for assigning rights to the AFP. Our limited assessment of users with elevated rights did not identify any individuals with rights incompatible with their assigned roles and responsibilities; however, a documented role-based access scheme helps to ensure appropriate security measures are in place to limit AFP user
access to only the information and information technology resources they need to accomplish their assigned duties. (Tab B, page 5)
RECOMMENDATIONS We made five recommendations to improve controls over, and management of, AFP user access and rights. (Reference the individual Tabs for specific
recommendations.)
MANAGEMENT’S RESPONSE
Management concurred with the audit results, and actions taken corrected the issues identified.
FEDERAL INFORMATION SECURITY MANAGEMENT ACT
The Federal Information Security Management Act (FISMA), as codified in Title III of the E-Government Act of 2002, Public Law 107-347, requires each Chief Information Officer to report material weaknesses in policies, procedures, or practices annually to the Office of Management and Budget. Recommendations A.1, A.2, A.3, and B.1 in this report address corrective actions needed to improve the effectiveness of information security controls. In our opinion, the material weaknesses identified meet the requirement for establishing an Air Force Plan of Action and Milestone. In addition, we will consider these
weaknesses for inclusion in our annual FISMA input to the Secretary of the Air Force and to the DoD Inspector General.
DERRICK D. H. WONG Associate Director
(Information Systems Security and Communications Division)
JUDITH L. SIMON Assistant Auditor General (Financial and Systems Audits)
Table of Contents
Page
EXECUTIVE SUMMARY
iTAB
A Access Controls 1 B Rights Management 5
APPENDIX
I Background Information 7 II Audit Scope and Prior Audit Coverage 9
III Locations Audited/Reports Issued 11
IV Points of Contact 15
Tab A
Access Controls
1
BACKGROUND
Access controls help ensure information is accessed and changed by only authorized personnel. Information in the AFP must be restricted to authorized users who have an official need. Therefore, policies and procedures must be established to manage user accounts in Air Force information systems.
The DAA,1 along with functional system owners and system developers, must ensure
systems comply with access control requirements in Air Force Manual (AFMAN)
33-223, Identification and Authentication, 29 July 2005. AFMAN 33-223 requires DAAs to:
• Disable and delete all user accounts from an information system whenever the user is permanently transferred to another location or terminates employment.
• Ensure procedures are in place to notify Network Control Center, workgroup manager, and system administrator when an employee (military, civilian, or contractor) transfers, retires, separates, or is terminated.
• Disable all accounts, excluding web applications and single sign on accounts, inactive over 45 days. DAAs must delete all disabled accounts 90 days from the date they were disabled.
The GCSS-AF Integration Framework System Security Authorization Agreement (SSAA), Appendix E, Information System Security Policy (Final), April 2005, requires explicitly authorized user access by an official or implicit authorization derived from either official duty assignments or responsibilities. Therefore, MAJCOM and/or installation AFP administrators should monitor changes in user status (retirement, separation, or termination) and deactivate accounts when appropriate.
AUDIT RESULTS 1 – ACCESS CONTROLS
Condition. MAJCOM and installation administrators did not effectively maintain access control over the AFP. Specifically, administrators did not deactivate AFP user and administrator accounts of personnel who retired, separated, or were terminated.
• Reconciling all active user accounts as of 20 November 2006 against personnel data retrievals2 of retired, separated, or terminated Air Force military and civilian
1 The Deputy Director, Warfighter Systems Integration and Deployment (SAF/XCD-2), serves as the AFP
DAA.
2We retrieved data for retired, separated, and terminated civilian and military employees, including
National Guard and Reserves, from the Military Personnel Data System (MILPDS) and Defense Civilian Personnel Data System (DCPDS) databases.
Tab A
Access Controls
2
personnel identified accounts remained active for:
85,863 (57 percent) of 150,626 retired or separated active duty personnel.
21,921 (31 percent) of 70,745 retired, separated, or terminated civilian personnel.
13, 635 (18 percent) of 76,872 retired or separated National Guard and Reserve personnel.
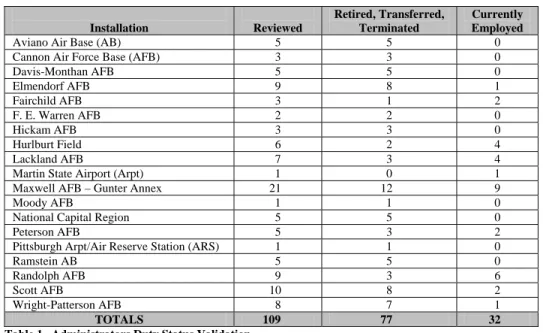
• Validating3 the duty status of individuals for all 109 administrator accounts at
19 judgmentally selected installations identified 77 (71 percent) administrator accounts were no longer valid. The individuals had retired, transferred, separated, or were terminated and no longer associated with the Air Force, or performing duties requiring privileged access to the system (Table 1).
Installation Reviewed
Retired, Transferred, Terminated
Currently Employed
Aviano Air Base (AB) 5 5 0
Cannon Air Force Base (AFB) 3 3 0
Davis-Monthan AFB 5 5 0
Elmendorf AFB 9 8 1
Fairchild AFB 3 1 2
F. E. Warren AFB 2 2 0
Hickam AFB 3 3 0
Hurlburt Field 6 2 4
Lackland AFB 7 3 4
Martin State Airport (Arpt) 1 0 1
Maxwell AFB – Gunter Annex 21 12 9
Moody AFB 1 1 0
National Capital Region 5 5 0
Peterson AFB 5 3 2
Pittsburgh Arpt/Air Reserve Station (ARS) 1 1 0
Ramstein AB 5 5 0
Randolph AFB 9 3 6
Scott AFB 10 8 2
Wright-Patterson AFB 8 7 1
TOTALS 109 77 32
Table 1. Administrators Duty Status Validation
Cause. This condition occurred because the AFP system program office (SPO) did not provide MAJCOM and installation administrators with procedures or effective tools to monitor and deactivate AFP accounts. Consequently, administrators were not aware they were responsible for monitoring and deactivating accounts. Specifically:
• The AFP Tiered Administration User’s Guide did not provide specific procedures
3 There were 135 administrator accounts at the 19 judgmentally selected installations. We confirmed duty status by interviewing assigned personnel at the former administrator’s unit of record. However, we were able to validate the status of only 109 administrator accounts because, in certain instances, assigned personnel could not confirm the administrator’s duty status.
Tab A
Access Controls
3
to monitor changes in user status (retirement, separation, or termination) and deactivate accounts when needed. For example, unit out-processing checklists at 17 (89 percent) of 19 installations did not include instructions to deactivate AFP user accounts when duty status changes.
• The Web Portal Manager tool provided to administrators was not capable of extracting user account data to monitor and ensure inactive accounts were disabled after 45 days and deleted 90 days thereafter.
Impact. As a result, 49 (64 percent) of 77 administrators continued to log onto the system using their administrator accounts even after they separated or retired. Access must be controlled to protect the confidentiality, integrity, and availability of sensitive and critical information.
Recommendation A.1. The Chief, Warfighting Integration and Chief Information Officer (SAF/XC) should direct the AFP SPO to immediately deactivate the accounts of the retired, separated, and terminated users (121,419) and administrators (77) cited in this report.
Management Comments A.1. SAF/XC concurred and stated: “The AFP SPO has deactivated the accounts of retired, separated, and terminated users (121,419) and administrators (77) cited in this report. CLOSED.”
Recommendation A.2. SAF/XC should direct the AFP SPO to revise the AFP Tiered Administration User’s Guide to include procedures for monitoring changes in AFP user status and deactivating or deleting user accounts as required by AFM 33-223. The procedures should require MAJCOM and installation AFP administrators to:
a. Periodically monitor changes in user status (retired, separated, or terminated) to identify dormant accounts. We suggest developing an automated process to periodically reconcile user accounts with the Air Force Personnel Center (AFPC) or other personnel database.
b. Deactivate or delete accounts after specific periods of inactivity.
c. Include a requirement to deactivate or delete user accounts in unit out processing checklists.
Management Comments A.2. SAF/XC concurred and stated: “The AFP SPO has revised the AFP Tiered Administration User’s Guide to include procedures for monitoring changes in AFP user status and deactivating or deleting user accounts required by AFMAN 33-223. CLOSED.”
Recommendation A.3. SAF/XC should direct the AFP SPO provide MAJCOM and installation administrators a tool to monitor and identify inactive user accounts.
Tab A
Access Controls
4
Management Comments A.3. SAF/XC concurred and stated: “The AFP SPO has provided MAJCOM and installation administrators a tool to monitor and identify inactive used accounts. CLOSED.”
Evaluation of Management Comments. Management comments addressed the issues raised in the findings, and management actions taken should correct the problems identified.
Tab B
Rights Management
5
FOR OFFICIAL USE ONLY
BACKGROUND
National Institute of Standards and Technology Draft Special Publication 800-53A,
Guide for Assessing the Security Controls in Federal Information Systems, June 2007, requires system administrators to enforce the most restrictive set of rights4 or access users
need to perform specific tasks. The DAA (or the Information Assurance Manager [IAM], if delegated) must develop and implement a role-based access scheme to account for all privileged access rights, and implement the principles of least privilege and separation of duties. Under the least privilege principle, users with elevated rights are only granted access to (a) data; (b) control information, software, hardware, and firmware for which they are authorized and have a need-to-know; and (c) those roles and privileges they are authorized based on their functional duties. The DAA must also maintain visibility over all individuals assigned privileged user rights to ensure they comply with separation of duties and personnel security requirements.
Privileged users are individuals with rights and capabilities beyond “read”5 in an
information system. For example, a privileged user assigned content publisher rights can typically read, write, add, modify, or delete files, while those assigned content manager
rights can also grant publishing and management rights to other users.
AUDIT RESULTS 2 – RIGHTS MANAGEMENT
Condition. The AFP DAA did not develop a role-based access scheme for assigning rights to the AFP. Specifically, although AFP security policy6 requires explicitly
authorizing and assigning rights (no “access by default”), the DAA did not define the specific access rights and roles authorized or identify the responsible approval authority.7
For example, AFP SPO personnel were provided elevated rights such as database and system administrators, and MAJCOM personnel were provided content publisher and manager rights. However, the security policy did not explicitly authorize these rights, or define the corresponding duties and responsibilities. Further, rights were provided by default since approval authority was not officially designated. To illustrate, MAJCOMs
4 The privileges a user or role has on an information system.
5 In computer terminology, “read” means transferring information from one storage medium or device to
another. For example, data is read from disk to a computer screen.
6 GCSS-AF Integration Framework System Security Authorization Agreement (SSAA), Appendix E,
Information System Security Policy (Final), April 2005.
7 The recently released draft AFI 33-394, Web and Air Force Portal Management and Internet Use, did not
Tab B
Rights Management
6
FOR OFFICIAL USE ONLY
assigned content manager and publisher rights by simply notifying the AFP SPO project manager through SAF/XC Exploitation Branch contractor personnel.
Cause. This condition occurred because neither the AFP IAM8 nor the SPO project
manager, who were delegated to prepare and maintain the security policy, were aware the policy needed to include a role-based access scheme.
Impact. A limited review of users with elevated rights did not reveal any individuals with rights incompatible with their assigned role and responsibilities. However, a documented role-based access scheme helps to ensure appropriate security measures are in place limiting AFP user access to only the information and information technology resources they need to accomplish their assigned duties.
Recommendation B.1. SAF/XC should direct the AFP DAA to document a role-based access scheme for the AFP in the AFP security policy. As a minimum, the scheme should identify the types and levels of user access authorized in relation to the user’s roles, tasks, duties and responsibilities, and the approval authority for granting each type of access.
Management Comments B.1. SAF/XC concurred and stated: “The AFP DAA has revised AFP security policy to document a role-based access scheme. The role-based access scheme in the policy identifies types and levels of user access authorized in relation to the user’s roles, tasks, duties and responsibilities, and approval authority for granting each type of access. CLOSED.”
Recommendation B.2. SAF/XC should require the IAM and/or the SPO project
manager to re-validate rights currently granted users against the role-based access scheme and adjust rights accordingly.
Management Comments B.2. SAF/XC concurred and stated: “The IAM and the SPO project manager have re-validated and adjusted privileged access rights granted users against the role-based access scheme. CLOSED.”
Evaluation of Management Comments. Management comments addressed the issues raised in the findings, and management actions taken should correct the problems identified.
8 The IAM is a contractor assigned to the 643d Electronic Systems Squadron based at Gunter Annex,
Background Information
7 Appendix I
FOR OFFICIAL USE ONLY
THE AIR FORCE PORTAL
A portal is an Internet website that acts as a starting point with links to many other websites. In December 2002, the Air Force launched the AFP to provide the primary means for accessing and presenting timely, accurate, and trusted information and information technology services to all personnel supporting the Air Force mission. The AFP provides self-service information access to any Air Force user through a standard web browser. The AFP is the GCSS-AF presentation layer9 that provides core enterprise
services to all applications, thus reducing the cost of developing and integrating
applications, while promoting security and interoperability standards. Access to sensitive data residing on the AFP should be restricted to authorized users who have an official need for the information. SAF/XC oversees the AFP and establishes policy and guidance for website content, publications, and forms.
INFORMATION ASSURANCE
The DoD defines information assurance as information operations protecting information and information systems by ensuring their confidentiality, integrity, authentication, availability, and nonrepudiation.
• Confidentiality. Information is seen and accessed only by intended recipients. Confidentiality is created primarily by using protocols that use encryption.
• Integrity. Information received is the same information transmitted by the originator.
• Authentication. Identifying an individual or computer to ensure access to
information is authorized. Authentication goes hand-in-hand with confidentiality and integrity.
• Availability. Information (voice, video, and data) and supporting service
resources (server, local networking infrastructures and transport medium) are up and running when needed.
• Nonrepudiation. Individual cannot deny sending or receiving information.
9The presentation layer is the sixth of the 7-layer open systems interconnect (OSI) reference model. The
8
Audit Scope and
Prior Audit Coverage
9 Appendix II
AUDIT SCOPE
Audit Coverage. We performed audit work at 19 judgmentally selected installations. We accomplished the work from July 2006 to June 2007 using documents (AFP user listing, AFPC database, security policy, system printouts, and outprocessing checklists) dated from 1 November 1991 through 4 April 2007. We provided a draft report to management in November 2007. To accomplish the audit objectives we performed the following tests:
• Access Control. We reconciled all 882,592 AFP user accounts as of 20
November 2006 by comparing accounts in the AFP database against the user’s duty status in the MILPDS and DCPDS databases. In addition, at the
judgmentally
selected installations, we validated the duty status of all system administrators through interviews and reviewing the functional duties they performed. Finally, we reviewed procedures and guidance administrators used to manage user accounts.
• Rights Management. We reviewed AFP security policy and other documentation to determine the specific rights and permissions authorized. Further, we
interviewed SAF/XC, SPO, and Defense Information Systems Agency personnel concerning roles and privileges granted. Finally, we compared elevated rights authorized for the AFP against those assigned to administrators.
Sampling Methodology. We used the following sampling concepts and Computer-Assisted Auditing Tools and Techniques (CAATTs) to complete this audit:
• Sampling. We judgmentally selected for review Headquarters Air Force and two installations from each of the eight MAJCOMs and Air National Guard with the highest number of administrators.
• CAATTS. We used Microsoft ACCESS to convert text files from the AFP active user account database (as of 20 November 2006), and personnel retirement, separation, and termination data from the MILPDS and DCPDS databases. We used the ACCESS merge, sort, query, and filter functions to compare and analyze the active user account data against the personnel data.
Data Reliability. We relied on computer-processed data to perform this audit. Specifically, we used computer-generated data obtained from Tivoli Access Manager, MILPDS, and DCPDS personnel systems. To establish data reliability, we validated the duty status of a judgmentalsample of administrators with personnel from the
administrators’ unit of record. Based on these tests, we determined the data were sufficiently reliable to support audit conclusions.
Audit Scope and
Prior Audit Coverage
Appendix II 10
Auditing Standards. We conducted audit work in accordance with generally accepted government auditing standards, and, accordingly, included tests of key internal controls associated with maintaining, deactivating, and deleting AFP accounts; approving administrator and privileged access rights; and granting roles in the AFP.
PRIOR AUDIT COVERAGE
We did not identify any Air Force Audit Agency, DoD Inspector General, or Government Accountability Office reports issued within the past 5 years that addressed the same or similar objectives as this audit.
Locations Audited/
Reports Issued
Installation-Level Organization/Location Reports Issued
FREEDOM OF INFORMATION ACT
The disclosure/denial authority prescribed in AFPD 65-3 will make all decisions relative to the release of this report to the public.
11 Appendix III
Headquarters Air Force (HAF)
AF/A4 NONE Washington DC
SAF/FM NONE Washington DC
Air Force Financial Systems Operations F2007-0041-FDD000
Maxwell AFB – Gunter Annex AL 10 May 2007
844th Communications Group NONE
Bolling AFB DC
Air Combat Command
27th Fighter Wing NONE
Cannon AFB NM
355th Wing NONE
Davis-Monthan AFB AZ
Air Education and Training Command (AETC)
HQ AETC NONE
Randolph AFB TX
Air Force Personnel Center NONE
Randolph AFB TX
12th Flying Training Wing NONE
Locations Audited/
Reports Issued
Installation-Level Organization/Location Reports Issued
Appendix III 12
Air Education and Training Command (AETC) (Cont’d)
37th Training Wing NONE
Lackland AFB TX
42d Air Base Wing NONE
Maxwell AFB AL - Gunter Annex
Air Force Materiel Command (AFMC)
HQ AFMC NONE
Wright-Patterson AFB OH
Aeronautical Systems Center NONE
Wright-Patterson AFB OH
643d Electronic Systems Squadron F2007-0052-FDD000
Maxwell AFB - Gunter Annex AL 13 June 2007
754th Electronic Systems Group F2007-0055-FDD000
Maxwell AFB - Gunter Annex AL 18 June 2007
Air Force Space Command
21st Space Wing NONE
Peterson AFB CO
90th Space Wing NONE
F. E. Warren AFB WY
Air Force Special Operations Command (AFSOC)
HQ AFSOC F2007-0068-FDD000
Hurlburt Field FL 24 July 2007
1st Special Operations Wing NONE
Hurlburt Field FL
23dWing F2007-0023-FCR000
Locations Audited/
Reports Issued
Installation-Level Organization/Location Reports Issued
FREEDOM OF INFORMATION ACT
The disclosure/denial authority prescribed in AFPD 65-3 will make all decisions relative to the release of this report to the public.
13 Appendix III
Air Mobility Command (AMC)
HQ AMC NONE
Scott AFB IL
92d Air Refueling Wing NONE
Fairchild AFB WA
375th Airlift Wing NONE
Scott AFB IL
Air National Guard
171st Air Refueling Wing NONE
Pittsburgh Airport PA
175th Wing NONE
Martin State Airport MD
Field Operating Agencies
Air Force Communications Agency NONE
Scott AFB IL
Pacific Air Forces
3d Wing NONE
Elmendorf AFB AK
15th Air Wing NONE
Hickam AFB HI
611th Air Operations Wing NONE
Locations Audited/
Reports Issued
Installation-Level Organization/Location Reports Issued
Appendix III 14
United States Air Forces in Europe
31st Fighter Wing NONE
Aviano AB, Italy
86th Airlift Wing NONE
Points of Contact
15 Appendix IV
Information Systems Security and Communications Division (AFAA/FSS) Financial and Systems Audits Directorate
5023 4th Street
March ARB CA 92518-1852
Derrick D. H. Wong, Associate Director DSN 447-4929
Commercial (951) 655-4929
Ronald P. Saclolo, Program Manager Ramesh Bharania, Audit Manager
16
Final Report Distribution
FREEDOM OF INFORMATION ACT
The disclosure/denial authority prescribed in AFPD 65-3 will make all decisions relative to the release of this report to the public.
17 Appendix V
SAF/AA SAF/OS SAF/US SAF/FM SAF/IG SAF/LL SAF/PA SAF/XC, AF/A6 AF/CC AF/CV AF/CVA AF/A3/5 AF/A8 AF/RE AF/XP NGB/CF AU Library DoD Comptroller OMB ACC AETC AFMC AFMIA AFNETOPS AFRC AFSOC AFSPC AIA AMC ANG PACAF USAFA USAFE Units/Orgs Audited
18