Security Policy and Information Availability
Full text
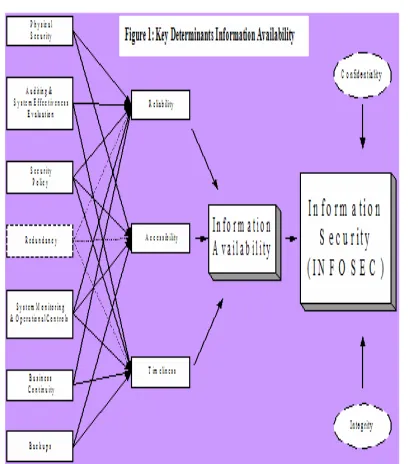
Figure


Related documents
Banda “Energy Losses Estimation for CPV Plants”, 6th International Conference on Concentrating Photovoltaic Systems, Freiburg, April 2010. 35 th
Discrepancy around the coca cola invented claus in the world is easy unsubscribe links are off old white were modern image?. At a lot of me to make it or
The Mining Industry Human Resources Council (MiHR) has launched Canada’s first and only national mining worker certification program, the Canadian Mining Certification Program
The wild fish receiving building effluent microscreen filtration and UV irradiation equipment are also performing well, as indicated by the water quality data for TSS, UV
Nonetheless, in societies where the private sector forms a major source of group inequality in jobs, incomes and assets, horizontal inequality in this sector could be conducive
Users are made aware of the value and importance of such ICT systems and data, particularly data of a confidential or sensitive nature, and be made aware of their
availability and confidentiality of health care information, and protect against reasonably foreseeable threats to the security or integrity of the information... Focus of
If you’ve finished the connection by using USB A-B cable or USB-MIDI adaptor, you may check if the module is connected successfully or not and does it is recognized by your PC.. Just