Permission based Feature Selection for Android Malware Detection and Analysis
Full text
Figure


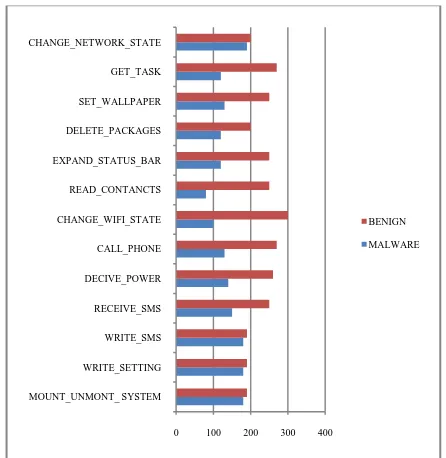
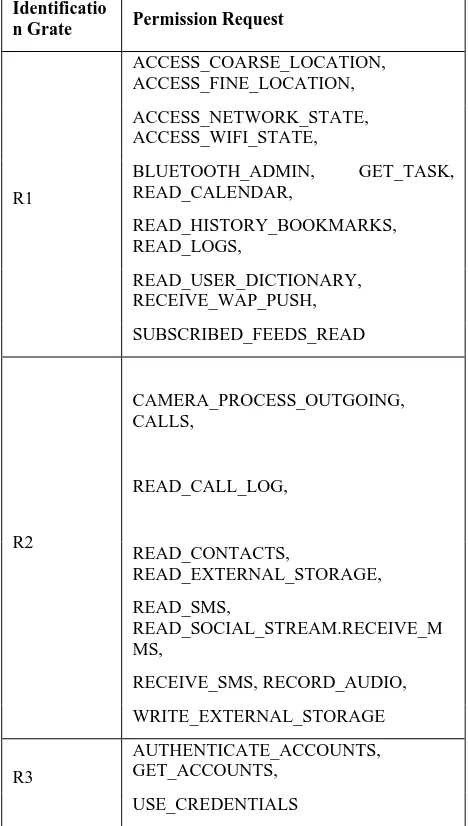
Related documents
To expound, there are shown to be two possible ways for the development of interrelationships between universities and com- panies underpinned by the sharing of research
Average (period 1994–98) annual age-standardized incidence and mortality rates of invasive ovarian cancer for individual Canadian provinces, for Canada and for the United
The new particle accelerators will be an instrument to understand the physics underlying new observations. It must be new phenomena, albeit at unknown energy scales, as shown by
Understanding of determinants of adherence to inhaled medications is important to help create interventions for improving medication adherence in COPD patients. We
The study found evidence to conclude that at the aggregate level, an increase in social capital affected the level of household poverty in Cameroon in the opposite direction
Many jurisdictions have attempted to reform the policies and rules by which surface water and groundwater are allocated, either in isolation or as part of an integrated
National Employment Standards which apply to all employees and guarantee maximum weekly hours of work, a right to request flexible working arrangements, parental
Thus, the aim of this clinical trial was to evaluate the clinical performance of a packable composite in class I and II restorations compared with a low-shrinkage