Asymmetric key encryption based on pseudorandom number generators Alhussain Amanie Hasn
Full text
Figure

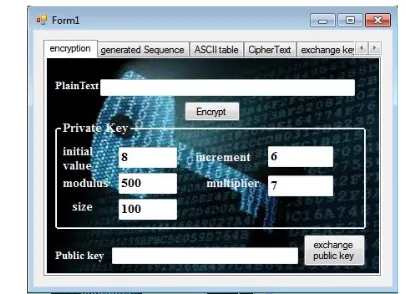

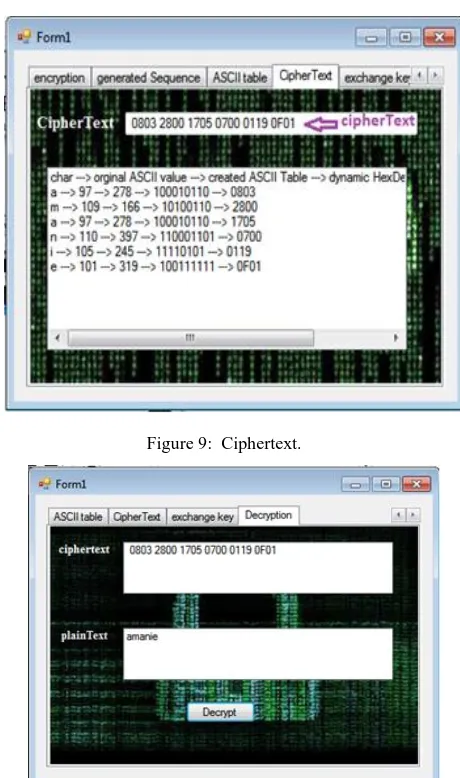
Related documents
Cyprus Property For Sale provides FREE property listing to all Cyprus Property Developers, Cyprus Real Estate Agents as well as in.. Out of these, the cookies that are categorized
In urban areas, the state focuses mainly on the network of monuments and on the homogeneous treatment of public spaces (Alphand, 1867). In the face of state interventionism, the
WIMAX is one of the fastest emerging technologies which is considered as cheaper alternative to mobile technology protocols such as 3G, 4G or 5G. WiMAX promises high speed
Bana uzun süre sarıldı, beni sevdiğini söyledi ve daha önce gö-çenler gibi burada benim için olduğunu söyledi.. Ardından Jim Smith'i
employment status at registration, exit quarter, preprogram employment and earnings, summary variables, industry of most recent employment, and labor market area. Standard errors
Las cuestiones de investigación se abordaron desde la perspectiva cualitativa, centrando la atención en el contexto y atendiendo a la experiencia de las personas de
The New Therapies Subgroup of the GMMMG considered the use alprostadil (Vitaros®) cream for the treatment of erectile dysfunction in adult men. The group recommends alprostadil
The criteria contains a quantity limit of 8 tablets total for any combination of the 3 oral products (sildenafil, tadalafil, or vardenafil) or a quantity limit of 8 units total for