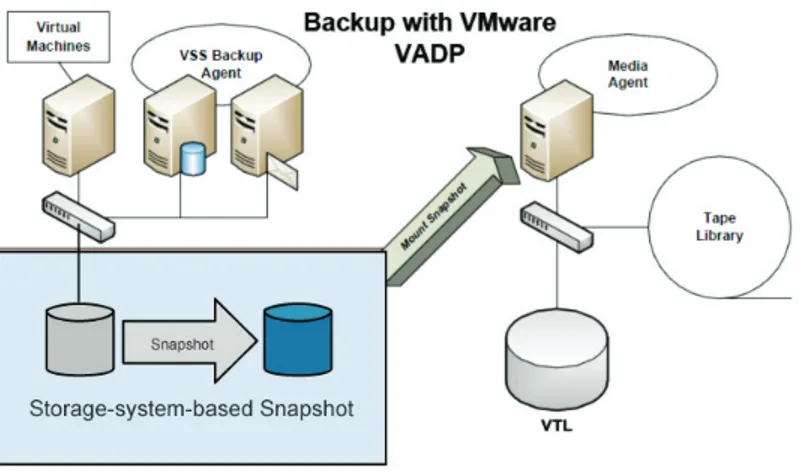
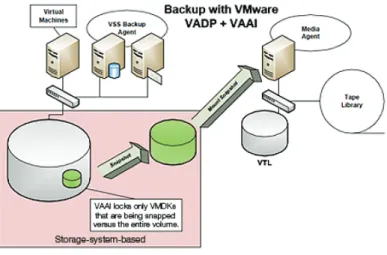
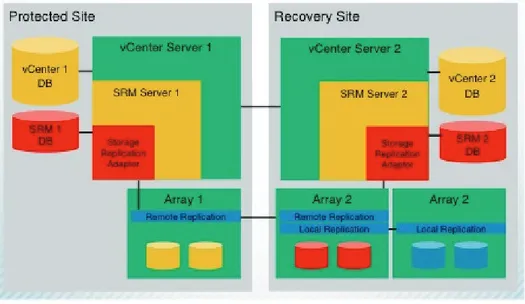
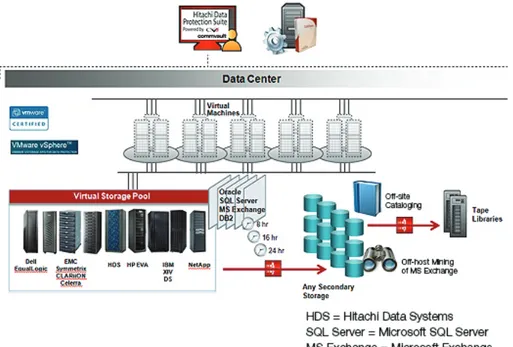
How to Effectively Protect Data in Virtualized Environments. By Hitachi Data Systems
Full text
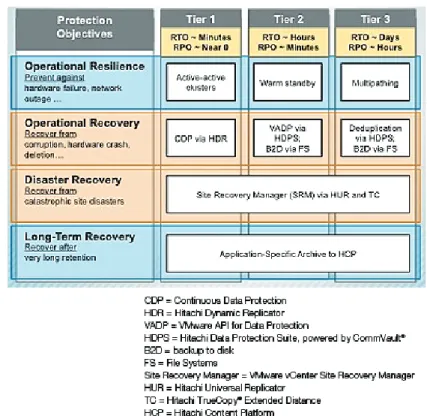
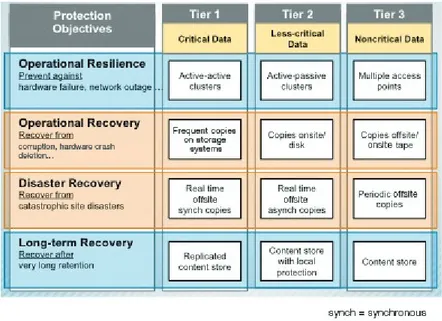
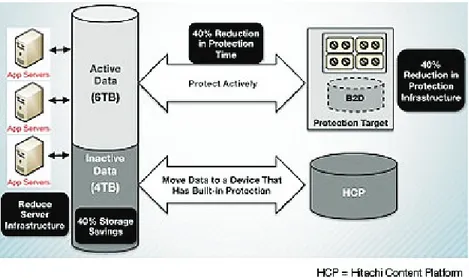
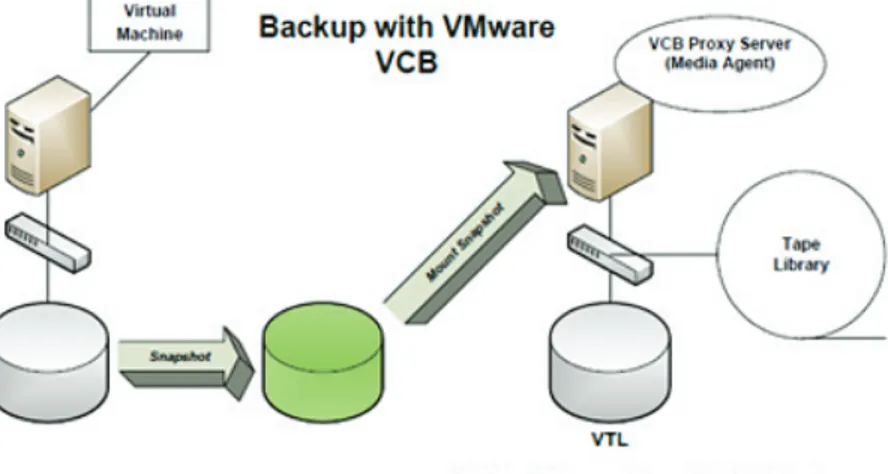
Figure

Related documents
Traditionalist Salafi bypassing of centuries of Muslim legal scholarship leads Late Sunni Traditionalists to level accusations of arrogance against Traditionalist Salafis... In
– What triggers can be used for starting, boosting, or stopping a contingency or mitigation activity!. – What is the best way to gum up the risk
Social Security and National Insurance Management Programme - Page 37 of 44 Postgraduate Certificate, Postgraduate Diploma, and Diploma –. Postgraduate
Figure 1 illustrates the proposed hybrid adaptive flight control. The control architecture com- prises: 1) a reference model that translates a rate command into a desired
● From the Start/Finish at the River House Barn, head south and cross Fig Ave into the River Campground and head EAST and connect with Main Loop trail.. ● The main loop trail will
A prospective study of thirty myofascial trigger points in upper trapezius were considered to determine the effectiveness of transcutaneous electrical nerve stimulation and
A uthor (year) Summ ary Te chniques Projects Data required Mohant y, A garwal, Choudhury, and Tiwari (2005) The proposed ap proach sim ultaneously addresses th e issue of combining
Pressing the Function Button five times displays the output current to the grid.... Press the Function Button six times displays the current