Stop DDoS Before They Stop You!
CNNIC Conference
09/2013
09/2013
INTERNET
ATTACK(DDOS & WEB)
ANALYSIS
AND
SOLUTIONS
SOLUTIONS
“The endless war”
•
2013
– Mar. 2013, Izz ad‐din Al‐Qassam initiated 3rd round attack that
target to U.S. Banks, including Bank of America, Citigroup, Wells
Fargo, US Bancorp, PNC Financial Services Group Inc, Capital
One, Fifth Third Bank, BB&T and HSBC.
– Mar. JP Morgan Chase website offline due to DDoS;
– Mar. DDoS attack targed to Czech telecom, banks website;
– Feb. Anonymous OpEgypt targeted to Egypt government websites;
– …
•
2012
– Jul. Anonymous “Operation Japan” attacks to Japanese
government websites;
– Mar. DDoS attacks to Hong Kong – The Chinese Gold & Silver
Exchange Society; Exchange Society;
– Mar. DDoS attacks to NASDAQ;
– Feb. DDoS attacks to U.S. Department of Justice, U.S. Copyright
office, Mexico government websites;
– Brazil‘s top financial institutions, including Banco Bradesco and
Banco do Brasil; Banco do Brasil;
– local and global websites of U.K.'s HSBC Holdings PLC
– …
•
2011
– Malaysia Action, over 50 Malaysia government and financial
b i d k websites under attack;
– Sony lost over 2 billion USD because of Anonymous attack;
– Visa, Paypal Amazon also underwent attacks and paralysed in
revenge for terminating donation account for wikileaks.
– Korea 40 Government Websites and corporate institutions under
tt k hi h i l di P id ti l Offi N ti l I t lli attack, which including Presidential Office, National Intelligence
We are Anonymous
Anonymous:
h
i i
DDoS Trends in 2013 H1
35000 40000
33807 36266
DDoS
Attack
Frequency
21% 5% 1% 1% Bank 15000 20000 25000 30000 35000 19812 29962 25016 23596 43% 21% Bank Government Enterprise NPO 0 5000 10000 15000
Jan Feb Mar Apr May Jun
29% ISP
Other
Jan Feb Mar Apr May Jun
Figure 2 DDoS Attacks Monitored by NSFOCUS Figure 5 Targets of Major DDoS Attacks
TCP_FLOOD 38.7%
The
combination
of
Hybrid
DDoS
Attacks
HYBRID_FLOOD DNS_FLOOD HTTP_FLOOD 4.1% 13.1% 37.2% 9.8% 10.8%
y
ICMP_FLOOD OTHER UDP_FLOOD 0.3% 3.0% 3.5% 50.6% 18.5% 10.2% ICMP+TCP+UDPICMP+TCP+UDP+DNS ICMP+TCP TCP HYBRID Other 0.0% 5.0% 10.0% 15.0% 20.0% 25.0% 30.0% 35.0% 40.0% _Figure 8 Methods of DDOS Attacks
Findings of DDoS Trends
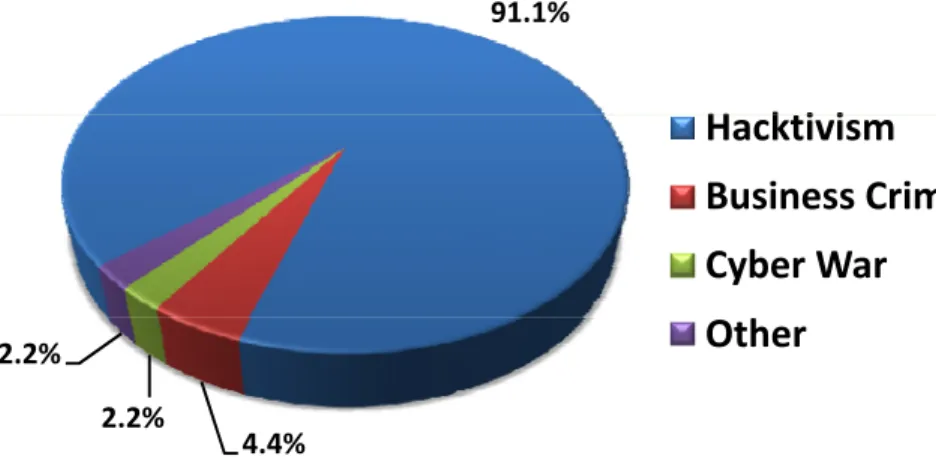
91.1%
H k i i
Findings
from
“NSFOCUS
Mid
‐
year
DDoS
Threat
Report
2013”:
Hacktivism
Business
Crime
Cyber
War
h
One
major
DDoS
news
event
happened
every
two
days
and
one
common
DDoS
attack
happened
every
two
minutes;
4.4% 2.2%
2.2%
Other
Figure 3 Causes for Major DDoS Attacks
DDoS
motives
‐
Hacktivism tops
the
list;
DDoS
victims
– Most
likely
targets
were
banks,
governments
and
enterprises;
Figure
3
Causes
for
Major
DDoS
Attacks
More
than
68
percent
of
victims
are
suffering
multiple
attacks;
TCP
Flood
and
HTTP
Flood
remain
the
most
popular
attack
methods;
Most
DDoS
attacks
are
short,
over
90%
less
than
30mins
Most
attacks
are
not
very
big,
over
90%
less
than
2Gbps
and
69%
less
than
0.2
Mpps
Hybrid
attacks
are
becoming
more
prevailing
The Scope of the Damage by DDoS Attacks
Motivations:
Organized
Crime,
Political
Protest,
Hactivism,
etc
State & Country
Damage on
Infrastructur
e
Telecom Carriers
IDC & ISP
IDC & ISP
Government &
Financial
Reputation
loss
Financial
E
i l
Enterprises
Economic
loss
Operation Malaysia(2)
Why Anonymous always win the game?
Attack
Tools
Type
Methodology
HTTP GET
Simulates HTTP requests by
i i h d
1
HOIC
HTTP
GET
Flood
setting connection threads,
editing scripts for random headers
or random URLs
HTTP
GET
Fl
d
Simulates requests via selecting2
LOIC
Flood
TCP
Flood
UDP
Flood
Simulates requests via selecting
different protocols and setting
attack connection threads, ports,
and etc.
3
R
‐
U
‐
Dead
‐
Yet?
HTTP
POST
Flood
A type of connection exhaustion
attacks that consume all the
resources on the target servers Simulates several zombie hosts
4
DDoSim
HTTP
GET
Flood
(having random IP addresses)
which create full TCP connections
to the target server, and then
starts conversations with the
listening applications (e g HTTP listening applications (e.g. HTTP
servers)
5
Slowloris
HTTP
GET
Flood
Sends partial HTTP requests to
hold connection open to exhaust
web server resources
Attackers
will
employ
more
diversified
and
varying
attack
methods
instead
of
simply
sending
attack
packets
in
a
6
Pyloris
HTTP
GET
Flood
PyLoris is a scriptable tool for
testing connection exhaustion
attacks. It is a Python
implementation of Slowloris
<Operation Ababil>
Background/Phase
Protest
2012.7 Disaster cased by a film clipAttack
2012.9.18Cyber Fighters set up DDoS attack to Banks of the U.S. Named as “Operation Ababil”2 Phases
Phase 1, 5 weeks (9.18-10.23)Phase 2, 7 weeks (12.10-1.28)Characteristics
Big Traffic Volume
Big Traffic Volume
Multiple Attack Methods
Multiple Attack Methods
1. Web Servers as Zombie
1. Network Layer:
TCP/UDP/ICMP Flood
2. Dozens of G
3. Numerous Zombies
TCP/UDP/ICMP Flood
2. Application Layer:
HTTP/DNS Flood
DDoS
DDoS
Last Long Time
Last Long Time
Multiple targets
Multiple targets
DDoS
DDoS
1. Several months
2. APT alike
1. Dozens of finance institute
Operation Steps
•Vulnerable admin passwords •Software Vulnerabilities Known:
Zombies are Web Server!!
1. TimThumb of WordPress2. Joomla
Penetrate Web
Servers
Use
multi-layer attack
mode
Launch DDoS
attack
Use some Web servers
Penetrate numerous
high-bandwidth Web
Servers
Zombies launch DDoS
attack to targets
Use some Web servers
as C&C servers, the
others as zombies;
Upload PHP DDoS
Servers
Attack Tools
Attack Tools
Name
Type
Name
Type
Itsoknoproblembro
TCP Flood
UDP Flood
HTTP Get Flood
HTTP Post Flood
Kamikaze
HTTP Get Flood
A
HTTP P
t Fl
d
<Spamhaus VS. Cyberbunker>
ICP VS DC, 2013.3.18
Cyberbunker has
relationship
with
criminals
from
East
Europe
and
Russia,
is
behind
recent
network
attacks
1
Spamhaus abused
p
its
position,
it
has
no
right
to
decide
what
content
can
2
appear
on
the
Internet
and
what
MSSP step out, VS DC
5
Just 75G,
got it done
We
have
been
attacked
4
Help!
got it done,
you can do some marketing
continuously
for
1
week,
but
we
kept
standing,
never
down.
You
cannot
imagine
how
much
3
I got attacked
DDoS!!
efforts
our
engineers
made.
Such
attack
can
swallow
MSSP became Target
6
You dare to help him!
I will strike you
instead.
5
Just 75G,
got it done
Attacked from Mar 23,
300-600G, targets are not ordinary
equipments but CloudFlare BGP direct
4
Help!
got it done,
you can say something about it
equipments, but CloudFlare BGP direct
peering and IX, attacks are totally
out of control. Attacks to IX include
London LINK, Amsterdam AMS-IX,
HK-I got attacked
DDoS!!
London LINK, Amsterdam AMS IX, HK
IX, Frankfurt DE-CIX, etc. Among
them, London IX got influenced most
significantly, caused direct effects
g
y,
to Internet Business within.
ISP got effected
6
You dare to help him!
I will strike you
instead.
5
Just 75G,
got it done
If this goes on, the entire
4
Help!
got it done,
you can say something about it
If this goes on, the entire
network of Europe will down, you
have to stop, CloudFlare, we need
to talk about how to solve the
problem.
7
I got attacked
DDoS!!
Words after Event
We
will
continue
our
righteous
career,
we
will
not
be
stroked
down,
we
are
the
best!
There
is
no
evidence
saying
that
we
are
responsible
of
the
action.
We
will
persist
p
in
our
belief,
“Freedom
Internet”!
We should keep low
‐
profile thanks for the
We
should
keep
low profile,
thanks
for
the
collaboration
of
everyone,
we
need
to
improve.
You
made
so
much
trouble
to
us,
and
we
did
not
earn
any
money
from
these
work.
Last
year,
we
have
warned
that
we
need
to
pay
attention
to
the
right
configuration
of
DNS
What we got from the event?
►
DDoS and Web attack devastate Data Center Web
Hosting business.
►
Both of the 2 attacks are complicated, but in
different ways.
►
Data Centers need to mitigate DDoS and Web
attack simultaneously
accurately and
cost-attack simultaneously, accurately and cost
effectively.
►
How to transfer from DDoS attack mitigation to
g
Web attack mitigation smoothly as the attack
changes? For instance, DDoS attack from 1G to
d
h
40G to 100G to 400G, and change from DDoS
attack to Web attack.
Internet Infrastructure and Web Security Solutions
Understanding DDoS/BOTNET
Router
overloaded
Bandwidth
consumption
consumption
DNS EmailDDoS Protection Over Time
Stone
Age
Medieval
Age
Current
Age
g
Age
Age
•
Block
Ips;
•
Black hole;
Black
hole;
•
Load
balance;
•
Dedicated
DDoS
•
System
enhancement;
•
High
performance
router
and
switch;
;
•
IPS/NGFW;
Mitigation
System;
•
Multi
‐
layer
cleaning;
•
Traffic
Diversion;
;
DDoS Mitigation - Multilayer Traffic Cleaning Algorithm
Traffic Cleaning Center Traffic Cleaning Center Att kInternet
L Attacker 1 1 22 33 44 55 Rate Limit Protoc o Analys i Access Control L Reputa t List L ayer 4 Fl o Mitigati o Layer 7 Fl o Mitigati o 6 6 o l is List tion on ood on ood2. Access Control List 2. Access Control List
L 4 ACL 1. Protocol 1. Protocol Analysis Analysis 3. Reputation List 3. Reputation List White/Black List 4. Layer 4 Flood 4. Layer 4 Flood Mitigation Mitigation 5. Layer 7 Flood 5. Layer 7 Flood Mitigation Mitigation
66: : Rate LimitRate Limit
Restricts traffic and
Layer 4 ACL Conn-Exhaustion ACL URL ACL y y Protocol Validation by RFC Check White/Black List Dynamic Prioritizing g g Source/destination IP address check/verification Various mitigation algorithms g g Various mitigation algorithms Pattern Matching
Restricts traffic and ensures the critical business.
Out-of-path full-Diversion Solution
Traffic Cleaning
NTA
EBGP
Router
•Attack Detection
-
NTA
T ffi Di
i
Att k Miti ti
T ffi R
ADS
Attack Logs
Advertisement
Switch
•Traffic Diversion, Attack Mitigation, Traffic
Re-injection
-
ADS
ADS-M
• Applicable for Telecom Carriers, IDC, and MSSP
• Benefits:
• Only the traffic to target server are diverted;
• Automatic attack detection and cleaning
Automatic attack detection and cleaning
process will simplify operator’s work during
attack prevention process;
• High reliability, the out-of-path deployment
will not affect other traffic. And the traffic
direction will recovered itself if the ADS
product out of work
The thought of DDoS mitigation
–
from box mitigation to value-added service
Internet
Multi
‐
layered
collaboration
Mgt. & Operation Mgt. & Operation
ISP1
100G
ADSAnti
‐
DDOS
Solution
Anti
‐
DDOS
Solution
Traffic
Monitoring
Traffic
Monitoring
Data Center
/MSSP
10G
to
40G
ADS ADS ADSAttack
Mitigation
Attack
Mitigation
1
‐
10G
Hosting
ADS/WAF•
Traffic
monitoring
+
DDoS
mitigation;
•
Out
‐
of
‐
path
traffic
diversion;
•
CPE Web security (WAF) + Cloud cleaning service;
•
CPE
Web
security
(WAF)
+
Cloud
cleaning
service;
DDoS Attack Mitigation
Internet
1. IP address Verification
•Source/destination IP address check/verification
2 Access Control List
ISP1
2. Access Control List
• Layer 4 ACL • Conn-Exhaustion ACL • URL ACL 3. Reputation List • White/Black List • Dynamic Prioritizing 4. Protocol Analysis
100G
IDC2
4. Protocol Analysis•Protocol Validation by RFC check
10G to
40G
5. Layer 4 Flood Mitigation
•Source/destination IP address check/verification •Various mitigation algorithms
6. Layer 7 Flood Mitigation
• Various mitigation algorithms •Pattern Matching
7: Rate Limit
Web
Hosting
7: Rate Limit
•Restricts traffic and ensures the critical business.
It has been consensus in Data Center industry that the best place
to stop DDoS attack e g SYN flood is in backbone network since
1G
to stop DDoS attack, e.g. SYN flood, is in backbone network, since the attack traffic volume can be large, e.g. 10Gbps. Data Center
usually provides DDoS attack mitigation as a part of its infrastructure service.
Web Attack Mitigation
On the other hand, Web attack, e.g. SQL Injection, is not large in volume, but its payload goes up to data level. Data Center usually provides Web attack mitigation as a dedicated service to Web
Hosting customer
Internet
1. Network Access Control 1. Network Access Control 2. TCP FloodProtection 3. HTTP Termination3. HTTP Termination 4 SSL Decryption 5. Data 5. Data 6. HTTP Flood Hosting customer.
ISP1
100G
4. SSL Decryption Normalization Normalization Protection 7. HTTP Validation 7. HTTP Validation 8. HTTP Access Control 8. HTTP Access Control9. Web Server and Plug-in Protection
9. Web Server and Plug-in Protection 10 Rule-Based 10 Rule-Based
IDC2
10G to
40G
10. Rule-Based Protection •Crawler •XSS •SQL Injection 10. Rule-Based Protection •Crawler •XSS •SQL Injection 11. Behavior-Based Protection •Illegal File Upload 11. Behavior-Based Protection •Illegal File Upload 12. Customized Protection Mechanism 12. Customized Protection Mechanism •SQL Injection •LDAP Injection •SSI Command Injection •XPath Injection •Command Line •SQL Injection •LDAP Injection •SSI Command Injection •XPath Injection •Command Line Upload •Illegal Download •Information Disclosure •Leech •CSRF Upload •Illegal Download •Information Disclosure •Leech •CSRF •White List •Smart Patch •Custom Security •Exception Policy •White List •Smart Patch •Custom Security •Exception PolicyWeb
Hosting
1G
Command Line Injection •Path Traverse •Remote File Inclusion Command Line Injection •Path Traverse •Remote File Inclusion CSRF •Scanning •Cookie Hijacking CSRF •Scanning •Cookie HijackingNext step - Cloud Pipe End Security Ecosystem
Automatic
collaboration
between
DDoS
mitigation
center,
WAF(CPE)
and Cloud MSS center.
24 x 7 MonitoringCloud
④
and
Cloud
MSS
center.
①
Assessment:
Remote
web
scanning
and
collaborates
with
WAF to provide smart patches
Managed Security Service PlatformSecurity Experts
Attackers Application layer attacks
④
WAF
to
provide
smart
patches
to
web
servers;
②
On
‐
premises
protection:
NSFOCUS
WAF
(CPE)
takes
care
of application layer web
Cleaning CenterScanning Smart patches Volumetric attacks 24x7 Monitoring
①
③
of
application
layer
web
attacks;
③
Traffic
Cleaning:
WAF
collaborates
with
ADS
traffic
cleaning
center
when
attack
Internet ADS ADS ADS Cleaning Center Smart patches
③
c ea
g ce e
e a ac
scale
exceeds
its
capacity;
④
MSS
Platform:
All
components
are
able
to
work
with
NSFOCUS
7
×
24
MSS
platform
and
expert
WAF Escalation
Pipe
②
SS p a o
a d e pe
team.
IDC Server farmEnd
Scenario 1:Remote Correlation
Attack Traffic< CPE WAF ThresholdAttack Traffic ≧ CPE WAF Threshold
Correlation Clean Traffic
Internet
Cleaning Center
Anti-DDoS
Anti-DDoS
Botnet
GRE T
l
DDoS DDoSIDC
GRE
Tunnel
IDC
ADS
WAF WAF
Scenario 2:Data Center Internal Correlation
Attack Traffic< CPE WAF ThresholdAttack Traffic ≧ CPE WAF Threshold
Correlation Clean Traffic
Internet
Botnet
IDC
Anti-DDoS Anti-DDoSIDC
Cleaning Center
ADS WAF WAF WAF WAFAn Living DDoS Mitigation Example
Micron21 DDoS Mitigation Scenario USA
Cogent
IP
Transit
Direct
Peering
nLayer IP
Transit
DDoS
Attack
Traffic
Cleaned Traffic
HE
IP
Transit
Direct
Peering
Cleaned
Traffic
DDoS Portal
ADS
6020
DDoS Portal
ADS
‐
M
Mgt.
Southern
Cross To
M21 DC
DNS ATTACKS ANALYSIS AND SOLUTIONS
Recommended Solutions
1. Split
the
authoritative
Name
Server
and
recursive
Name
Server
2. DNS
redundancyy
3. Update
the
OS
and
DNS
Application
4. Firewall
Policy
‐
Access
Control
List
5. Hide
the
OS
or
DNS
Application
Version
6. Change
and
restrict
the
DNS
Root(Chroot)
7. Use
random
message
IDs
in
queries(use
‐
id
‐
pool)
8. Running
BIND
with
Least
Privilege
9. TSIG
(Transaction
SIGnature)
10. DNSSEC(DNS
Security
Extension)
Recommended Solutions
Limiting
Recursion
to
Authorized
Clients
Source
IP
Verification:
spoofed
IP
Disabling
Recursion
on
Authoritative
Name
Servers
Restricting
name
server
to
answer
certain
queries:
Rate
Limiting
Response
of
Recursive
Name
Servers
DNS Query Flood
DNS Query Flood
•
Pattern Match is the main cause of CPU
load
•
DNS server could handle 9,000 dynamic
Domain name requests per second.
•
A normal PC can send more than 10,000
A normal PC can send more than 10,000
requests per second.
•
The Random domain name queries cause
DNS server to generate recursive queries
DNS server to generate recursive queries
to parent DNS and overloaded.
•
DNS server denies normal services, which
ff t b i
di
tl
affects business directly.
NSFOCUS
Solution
‐
1
UDP Limitation
TC Bit Algorithm
DNS Query
Force the client to use TCP
Algorithm Instruction
–
Truncate Bit
–
UDP
TCP
DNS Response with TC BitDNS policy setting
SYN (53) Verify the client during
the TCP process
SYN+ACK ACK FIN+ACK
DNS Query