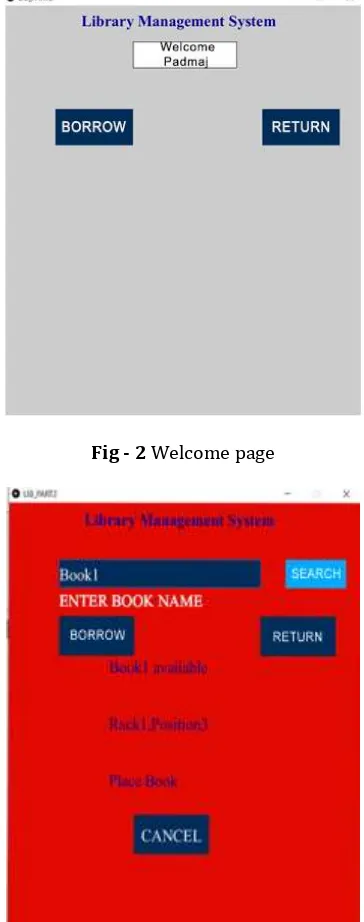
Library Management using RFID
Full text
Figure



Related documents
TIG cold wire welding was developed firstly with the aim of making TIG welding easier and more convenient to use and secondly to increase the welding speed. In this process, the
requirements for using the spectrum are very stringent. Our XG approach is applicable to both centralized and distributed architectures. Indeed, policy may decide whether or not
( 2017 ) 80 Countries, 2001–2011 OSIRIS (Bureau van Dijk Electronic Publishing), International Country Risk Guide, Global Competitiveness Report, and the World Bank’s Doing
If we implement the priority queue P with a heap, then, during the first phase, each of the n insert operations takes time O(log k), where k is the number of elements in the heap at
We plotted these interactions in Figures 2, 3 and 4, which suggest that ability, benevolence and integrity as three facets of perceived manager trustworthiness are more
This framework incorporates the knowledge that is extracted by data mining techniques from EHRs with knowledge from do- main experts into health care information systems for
The following diagnostic procedures were compared for sensitivity and specificity with cytology alone: TRAP assay alone; cytology and TRAP assay in parallel, with
Variables and Count erproduct ive Work Behaviours ... 196 Table 25: Uncorrect ed and Correct ed Correlat ions am ong Personalit y Variables and Organisat ional Cit