A User Identity Management Protocol for Cloud Computing Paradigm
Full text
Figure


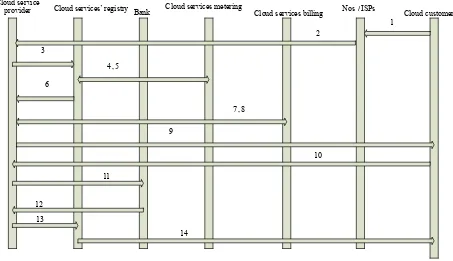

Related documents
In order to clarify the complexity of Yashka, we need to look into the historical, political, social, and cultural contexts in which Russian women soldiers, like
Through the analysis of the deformation status after data processing, this paper con- cludes that GPS technology is a good monitoring tool for the sedimentation of railway
greatly simplifies the analysis, and rules out the strange effect that a higher reward for a good fit from principal 1 can motivate agent 2 to pay higher effort through a
(Jbosila, 2013) defines study habits as the attitude of one person towards their academic year in life. It has been also studied by many researchers. In fact, according to
The reason of why enterprises cannot adopt lean manufacturing techniques is that ineffective inventory management, lack of supplier participation, lack of quality
generally require additional testing in accordance with accepted standards for such product characteristics. Bending resis- tance / stiffness * Technical Report, clause
In our mid-age cohort we see significant structural differences in these same regions: the parahippocampal cortical thickness and left anterior cingulate white matter volumes were
corallo/grigio, corallo/acquamarina, girasole/marron, girasole/viola, pisello/arancio, pisello/ pervinca, celeste/bleu, celeste/verde acido, bleu/pesco, bleu/giallo,