On Secure Digital Image Watermarking Techniques
Full text
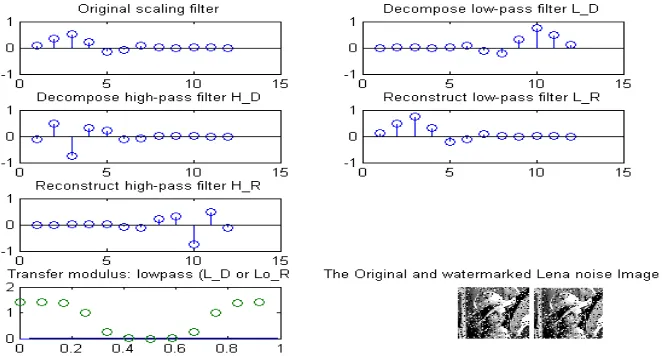
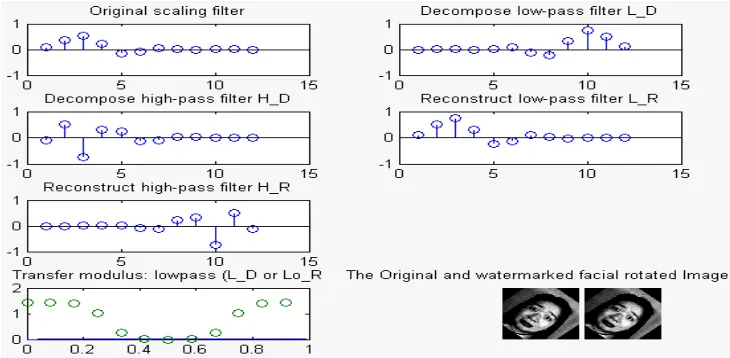
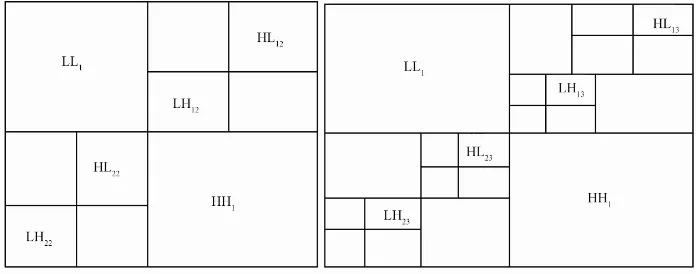
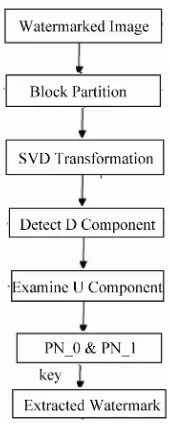
Figure

Related documents
The purpose of this study is to analyze the influence of perceived contract violation (PCV), abusive supervision (AS) and servant leadership (SL) on
This article is derived of PhD research thesis in school of Traditional Medicine, Shahid Beheshti University of Medical Sciences, Tehran, Iran and Royan Institute for
Herein, we report a simple, convenient and efficient method for the synthesis of dipyrromethanes by boric acid catalyzed condensation of pyrrole with different
Aber man darf nicht übersehen, dass nachhal- tiger Shareholder Value nur geschaffen wird, wenn auch Werte für andere Sta- keholders (Anspruchsgruppen) geschaffen werden, allen voran
Mutants of ttm50 , which encodes a Drosophila ortho- log of Tim50, showed systemic growth defects, such as delayed development and reduced cell size and cell proliferation,
Given the expanded range of HEW responsibilities and plans for HEWs to have an enhanced role in community- based newborn care, senior leadership in the Federal Ministry of
All the way through [11] , instigator bestowed a designed Central Load Balancing Policy for Virtual Machines (CLBVM) to stable the weight consistently in a dispersed
Many DDoS defense strategies were proposed, implemented, and tested to be effective against DDoS attack over the Internet. In this phase, the maximum commonplace protection