Towards Understanding of Medical Randomized Controlled Trials by Conclusion Generation
Full text
Figure
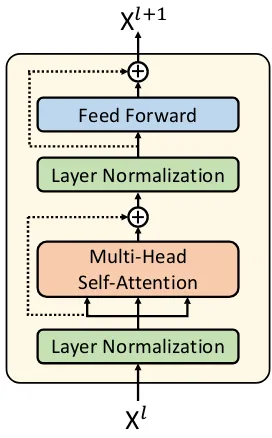
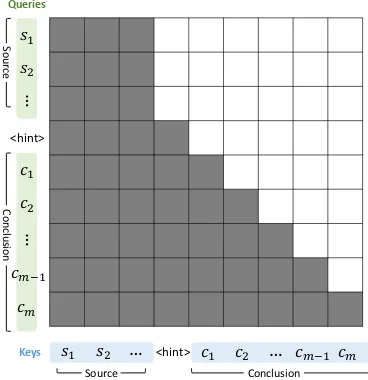
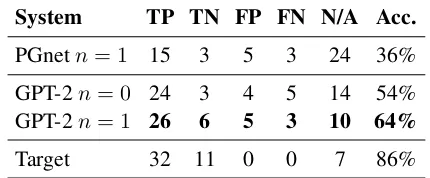
Related documents
Female mice either resolve acute cystitis or develop chronic bacterial cystitis, while very few develop lasting kidney infection or renal abscess (29, 30).. While chronic cystitis
18 Studenti sestrinstva navode da je najčešći zdravstveni razlog korištenja ljekovitog bilja bila bolest dišnog sustava (50% , 44%), dok je najčešći odgovor
In order to find out what kind of mutual relationships would reveal samples of gunshot residues collected from various types of ammunition as well as from the same type of
Third, it has been proposed that lead users might be relevant to the diffusion of new products, as their leading-edge status might empower them to serve as a field’s opinion
The primary purpose of the present study was to analyze whether the implementation of an automated appointment reminder system was associated with subsequent increased attendance
In Germany, these include subsidies to the hard coal industry; “eco-taxes” that are to increase energy taxes 10% during 2001–2004 (although, in late 2001, the chancellor’s
On June 9, 2003, the Tax Discovery Bureau (Bureau) of the Idaho State Tax Commission issued a Notice of Deficiency Determination (NODD) to [Redacted] (taxpayers), proposing income
This means that two hon- eypots which reside in two different logical networks get the packets destined for the other honeypot on the same inter- nal network which can be exploited