A Survey of Data Encryption & Data Decryption Methods
Full text
Figure
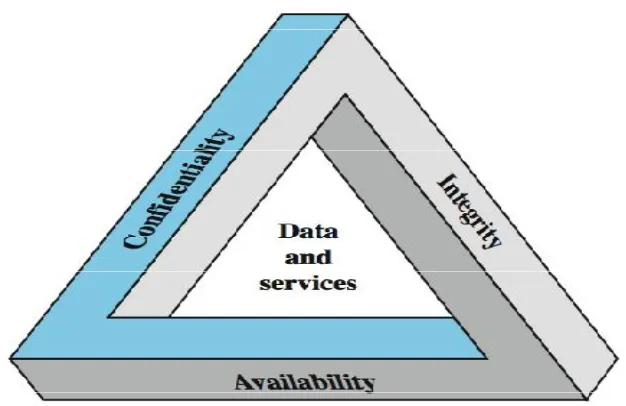
Related documents
CUAJ ? January February 2016 ? Volume 10, Issues 1 2 ? 2016 Canadian Urological Association E1 ORIGINAL RESEARCH Cite as Can Urol Assoc J 2016;10(1 2) E1 6 http //dx doi org/10 5489/cuaj
The inorganically grown samples of the rice crops showed significantly higher values for moisture content (14.48 %)as compared to that by organic samples (11.77 %), thus
We found that NT-G could significantly inhibit bacterial adhesion and biofilm formation compared to FlatTi or NT, and the NT-G with 160 nm and 200 nm diameters had
The effect of different DADMAC concentrations, and plasma conditions including the RF power (400-800 W) and the time of plasma exposure (0-120 sec) were studied and the
In our retrospective study, a total of seven patients with refractory/relapsed NKTCL were treated with pembrolizumab at our lymphoma diagnosis and treat- ment center.. Herein, we
The graphics memory used for the temporal shadow map relies on the number of visible time ranges stored at each pixel.. Figure 8 illustrates that using the coverage
Compliance with national recommendations for exercise during early pregnancy in a Danish cohort RESEARCH ARTICLE Open Access Compliance with national recommendations for exercise during
Predictive power of splenic thickness for post hepatectomy liver failure in HBV associated hepatocellular carcinoma patients RESEARCH Open Access Predictive power of splenic thickness