Active Permission Identification for Android Malware Application Detection
Full text
Figure
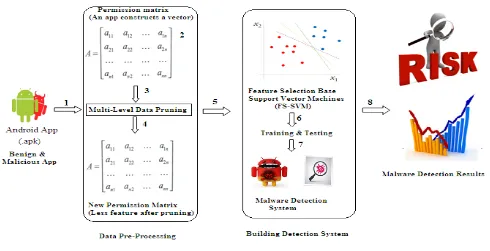
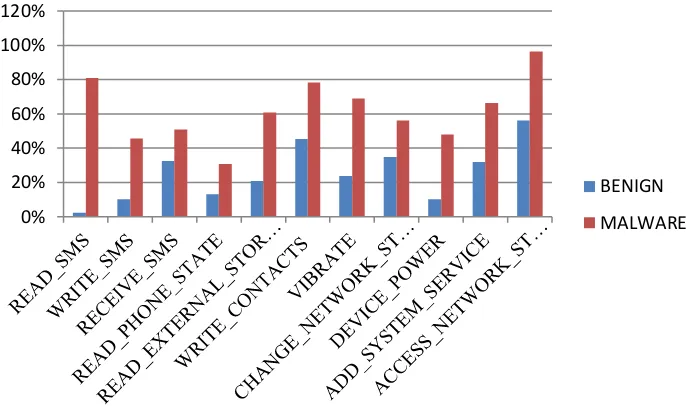
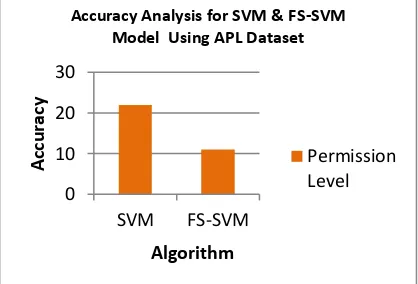
Related documents
From marine terminals to rail yards, from secure warehouses to the open road, CMI’s start-to-finish services are responsive, flexible and
Often, when I start working with a new client on a CMS analysis or selection effort, he or she proudly hands me a detailed spreadsheet or pages and pages of documentation that
These tax legislations had a direct impact on dividends decisions in South Africa, which further creates a need to investigate the relationship between dividend policy and
Figure 4.1: Comparison of running time of K-means algorithm on five different inds of platforms (including single core machine) with varying number of clusters k and number of
This role has an important capacity building function, which involves working closely with the Provincial and district partners, including the APEs, health
In most simulation models the supplementary force corresponding to the inertia of the different rotating components is taken into account by adding a fictive mass to the total
Average (period 1994–98) annual age-standardized incidence and mortality rates of invasive ovarian cancer for individual Canadian provinces, for Canada and for the United
Although they might live in the patrilocal family at the very beginning of their marriage, young couples consciously sought any opportunity to form their own nuclear families; most