A Review on Techniques for Searching and Indexing over Encrypted Cloud Data
Full text
Figure

Related documents
Association between MTHFR gene 1298A>C polymorphism and breast cancer susceptibility a meta analysis based on 38 case control studies with 40,985 subjects RESEARCH Open Access
Intestinal intussusception in a young women unusual cause and specific management WORLD JOURNAL OF SURGICAL ONCOLOGY Elm?hadi et al World Journal of Surgical Oncology (2015) 13 252 DOI
different characters of the original parent plants A , a and B , b , four constant combinations are possible, and thus the hybrid produces the corresponding four forms of germ
Accessing information is an essential factor in decision making processes occurring in different domains. Therefore, broadening the coverage of available information for
10 Shows the waveforms of steady state three phase motor: (a) voltage and current of the grid, (b) dc-link voltage, (c) currents of rectifier A and circulating current, (d) currents
Resulting from the similarities in photophysical properties for synthetic and naturally occurring tetrapyrroles, synthetic porphyrins, chlorins, and bacteriochlorins
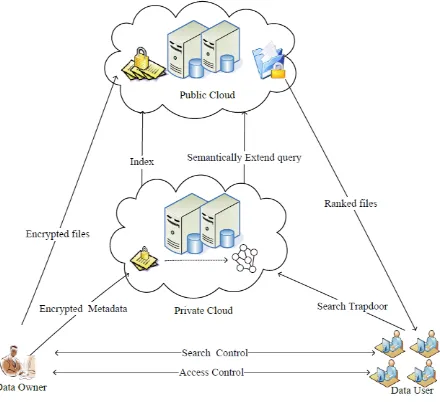
Primary Server: It is used as storage service provider which provides the hosting service for the outsourced data. Additionally, it implements the data storage, off sourcing
