International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
831
Analysis of Attacks and Challenges in VANET
Megha Nema
1, Prof. Shalini Stalin
2, Prof. Vijay Lokhande
3 Department of Computer Science Engineering, BIST, Bhopal- (M.P.), IndiaAbstract— Vehicular Ad hoc Networks (VANET) is a subgroup of (Mobile Ad Hoc Networks) MANET which is using for improves traffic safety system. Since the movements of Vehicles are restricted by roads, traffic regulations we can deploy fixed infrastructure at critical locations. We focus our study on the different kind of attacks and its behaviour or impact in safety system and how many challenges; we have to accept for high security. In this paper we classify different attacks based on different layers like MAC layer, network, transport, application and multi layer and different challenges
which included authentication, availability Privacy,
anonymity etc. After surveying we found that attacks in multilayer like denial of services (DOS) and DDOS are very harmful for security system as well as authentication and Privacy are big challenges. Simulation can be performed either on NS2 which is specially designed for network simulation or CAN network at VANET tool box in MATLAB.
Keywords— VANET, DOS, DDOS, MAC, CAN.
I. INTRODUCTION
Safety of human lives in the road is the major concern nowadays, because every year thousands of peoples died in road accidents over the world. Vehicular Ad hoc Network (VANET) is special kind of network that aims to reduce death rate and improves traffic safety system. Where nodes refer to vehicles.
Vehicular Ad hoc Networks (VANET) is part of Mobile Ad Hoc Networks (MANET), this means that every node can move freely within the network coverage and stay connected. In VANET, moving vehicles as nodes can send and receive safety messages to each other on the road to ensure safety of human life [1]. VANET turns every participating vehicle into a wireless router or node, allowing vehicles approximately 100 to 300 meters of each other to connect and, in turn, create a network with a wide range. As vehicles fall out of the signal range and drop out of the network, other vehicles can join in, connecting vehicles to one another so that a mobile Internet is created.
The primary goal of VANET is to provide road safety measures where information about vehicle’s current speed, location coordinates are passed with or without the deployment of Infrastructure.
Apart from safety measures, VANET also provides value added services like email, audio/video sharing etc.
Dedicated Short Range Communication (DSRC) is the frequency band that is used as a DSRC delivers safety and non safety messages in entire network by using its safety and non safety channels. Non safety applications are related to comfort of the passengers and to improve the traffic system. Parking availability and toll collection services are examples of these applications.
Security is an important issue especially in this kind of network where one altered message can creates problem for the users in many ways. Attackers create problem directly and indirectly by launching different kind of attacks.
II. VANETOVERVIEW
A. VANET Architecture
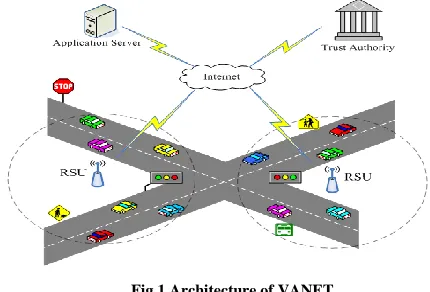
[image:1.612.335.550.430.576.2]A vehicular communications system comprises a number of interacting entities that we classify broadly as: Users, Network nodes, and Authorities.
Fig 1 Architecture of VANET
Communication pattern of vehicles are following-
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
[image:2.612.62.277.129.278.2]832
Fig 2 Communication pattern of vehicles
B. VANET Characteristics
In addition to the similarities to ad hoc networks, VANETs possess unique network characteristics that distinguish it from other kinds of ad hoc networks and
influence research in this area. Few important
characteristics of VANETs are as following:
(i)High Mobility
(ii)Rapidly changing network topology (iii)Unbounded network size
(iv)Frequent exchange of information (v)Wireless Communication
(vi)Time Critical (vii) Sufficient Energy
(viii)Better Physical Protection
C. VANET Applications
Major applications of VANET include providing safety information, traffic management, toll services, location based services and infotainment
III. VANETSECURITY CONCEPT.
VANET suffer from various attacks; these attacks are discussed in the following subsections:
A. ATTACKERS
Greedy Drivers: Selfish drivers trying to maximize their gain by making believe a congested path to their destinations, and consequently suppress traffic by attacking the routing mechanisms.
Snoops: Drivers attempting to profile drivers and extract their identifying information. Malicious Snoops can even track vehicle locations and determine the identities of drivers by corresponding them to the house or work sites. Pranksters: Drivers trying to disable applications or prevent information from reaching others vehicles. Such attacks are denoted by Denial of service attacks (DoS).
Malicious Attackers: Drivers deliberately attempting to make harm via the available applications within the network. Several attacks focus on damaging exchanged data between vehicles such as message fabrication, suppression or alteration. Sybil attack (Masquerade) [5]) belongs also to this category.
Industrial Insiders: If vehicle manufacturers are responsible for securing communications within VANETs, employees can reveal confidential data to malicious entities.
B. ATTACKER’S Properties
Attacker create problem in the network by getting full access of communication medium DSRC. Here we are discussing some properties and capability of the attackers which has been mentioned in studies.
Coverage Area: Attacker could cover the main area of road, and it depends on the nature of the attacks. Basic level attacker has controlled one DSRC channels and covers the range of at most 1000 meters but the extended level attackers are more organized and cover more area using of hundred DSRC channels.
Technical Expertise: Technical expertise of the attacker makes them stronger for creating attacks in the network. Attacker having ability to extracts the program code and secret keys of the computing platform of OBU and RSU by launching physical attacks.
Resources: Budget, manpower and tools are the three main key resources and attackers depend on it to achieve their goals.
C. Types of Attacks
Jamming: The jammer deliberately generates interfering transmissions that prevent communication within their reception range. In the VANET scenario, an attacker can
relatively easily partition the network, without
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
833
Fig3 Classification of attacks based on Layers
Node Impersonation Attack: Each vehicle has a unique identifier in VANET and it is used to verify the message whenever an accident happens by sending wrong messages to other vehicles [4, 9, and 10]. Fig explains this scenario in which vehicle A involves in the accident at location Z. When police identify the driver as it is associated with driver’s identity, attacker changes his/her identity and simply refuses it.
Fig4 Node Impersonation Attack
Sybil Attack:Sybil attack [10] so belongs to the first class. In Sybil attack, the attacker sends multiple messages to other vehicles and each message contains different fabricated source identity (ID). It provides illusion to other vehicle by sending some wrong messages like traffic jam message [3, 4]. Fig 5 explains Sybil attack in which the attacker creates multiple vehicles on the road with same identity. The objective is to enforce other vehicles on the road to leave the road for the benefits of the attacker.
Fig5 Sybil Attack
Routing attack: Routing attacks re the attacks which exploits the vulnerability of network layer routing protocols. In this type of attack the attacker either drops the packet or disturbs the routing process of the network. Following are the most common routing attacks in the VANET:
(i) Black Hole attack: In this type of attack, the attacker firstly attracts the nodes to transmit the packet through itself. It can be done by continuous sending the malicious route reply with fresh route and low hop count. After attracting the node, when the packet is forwarded through this node, it silently drops the packet.
(ii) Worm Hole attack: In this attack, an adversary receives packets at one point in the network, tunnels them to another point in the network, and then replays them into the network from that point []. This tunnel between two adversaries are called wormhole. It can be established through a single long-range wireless link or a wired link between the two adversaries. Hence it is simple for the adversary to make the tunneled packet arrive sooner than other packets transmitted over a normal multi-hop route.
(iii) Gray Hole attack: This is the extension of black hole attack. In this type of attack the malicious node behaves like the black node attack but it drops the packet selectively. This selection can be of two types-one is malicious node can drop the packet of UDP whereas the TCP packet will be forwarded. Another is malicious node can drop the packet on the basis of probabilistic distribution.
Session Hijacking: Most authentication process is done at the start of the session. Hence it is easy to hijack the session after connection establishment. In this attack attackers take control of session between nodes.
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
834 Denial of Service: DoS attacks are most prominent attack in this category. In this attack attacker prevents the legitimate user to use the service from the victim node. DoS attacks can be carried out in many ways [8].
(i) Jamming: In this technique the attacker senses the physical channel and gets the information about the frequency at which the receiver receives the signal. Then he transmits the signal on the channel so that channel is jam.
(ii) SYN Flooding: In this mechanism large no of SYN request is sent to the victim node, spoofing the sender address. The victim node send back the SYN-ACK to the spoofed address but victim node does not get any ACK packet in return. This result too half opens connection to handle by a victim node’s buffer. As a consequence the legitimate request is discarded.
(iii) Distributed DoS attack: This is another form Dos attack. In this attack, multiple attackers attack the victim node and prevents legitimate user from accessing the service.
IV. VANETNETWORK CHALLENGES
VANET security ought to satisfy the following needs:-
Message Authentication and Integrity: Message should be protected against any alteration and therefore the receiver of a message should corroborate the sender of the message. However integrity doesn't essentially imply identification of the sender of the message.
Message Non-Repudiation: The sender cannot deny of sent an information message.
Entity Authentication: The receiver isn't solely ensured that the sender generated a message, however additionally has evidence of the liveness of the sender.
Access Control: Access to specific services provided by the infrastructure nodes, or different nodes, is decided locally by police. As a part of access management, authorization establishes what every node is allowed to try and do in VANET.
Message Confidentiality: The information of a message is kept secret from unauthorized to access it.
Availability: The network and applications ought to stay operational even within the presence of faults or malicious conditions. This means not solely secure however additionally fault-tolerant styles, resilience to resource depletion attacks, further as survivable protocols, that resume their traditional operations when the removal of the faulty participants.
Privacy and Anonymity: Conditional privacy should be achieved within the sense that the user connected info, as well as the driver’s name, the license plate, speed, position, and traveling routes at the side of their relationships, has got to be
Protected: whereas the authorities ought to be ready to reveal the identities of message senders within the case of a dispute like a crime/car accident scene investigation, which may be accustomed hunt for witnesses.
Liability Identification: Users of vehicles are liable for their deliberate or accidental actions that disrupt the operation of other nodes, or the transportation system. Several attacks are known which will be classified depending on the layer the attacker uses. At the physical layer and link layers the attacker will disturb the system either by jamming or overloading the channel with messages. Flooding false messages or rebroadcasting a recent message is also an attainable attack.
Message fabrication, alteration, and replay can all be used towards impersonation.
Mobility: The basic idea from Ad Hoc Networks is that each node in the network is mobile, and can move from one place to another within the coverage area, but still the mobility is limited, in Vehicular Ad Hoc Networks nodes moving in high mobility, vehicles make connection throw their way with another vehicles that maybe never faced before, and this connection lasts for only few seconds as each vehicle goes in its direction, and these two vehicles may never meet again. So securing mobility challenge is hard problem. There is many researchers have addressed this challenge [5], [9], but still this problem unresolved. Volatility: The connectivity among nodes can be highly ephemeral, and maybe will not happen again, vehicles travelling throw coverage area and making connection with other vehicles, these connections will be lost as each car has a high mobility, and maybe will travel in opposite direction[1],[5]. Vehicular networks lacks the relatively long life context, so personal contact of user’s device to a hot spot will require long life password and this will be
impractical for securing VC.
A. Privacy VS Authentication:
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
835 B. Privacy VS Liability
Liability will give a good opportunity for legal investigation and this data can’t be denied (in case of accidents)[1], in other hand the privacy mustn’t be violated and each driver must have the ability to keep his personal information from others (Identity, Driving Path, Account Number for toll Collector etc.).
C. Network Scalability
The scale of this network in the world approximately exceeding the 750 million nodes [4], and this number is growing, another problem arise when we must know that there is no a global authority govern the standards for this network [1], [5], [7], for example: the standards for DSRC in North America is deferent from the DSRC standards in Europe, the standards for the GM Vehicles is deferent from the BMW one.
D. Bootstrap
At this moment only few number of cars will be have the equipment required for the DSRC radios, so if we make a communication we have to assume that there is a limited number of cars that will receive the communication, in the future we must concentrate on getting the number higher, to get a financial benefit that will courage the commercial
firms to invest in this technology [5].
[image:5.612.52.294.449.684.2]V. VANETSECURITY REQUIREMENTS
Fig 6 VANET Security requirement
(i) Privacy (ii)Authentication (iii)Non-repudiation (iv)Availability
(v) Real-time constraints (vi)Integrity
(vii)Confidentiality
VI. CONCLUSION
In this paper various aspect of VANET like its architecture, application, attacks and challenges have been discussed; furthermore various characteristics of VANET have been listed which distinguished it from other networks like MANET. This paper includes various attacks in VANET have been classified depending on the different layers. It has been observed that the classification helps to deal with different types of attack in VANET. We have
been discussed security challenge and security
requirements. We have found after survey that attacks in multilayer like denial of services (DOS) and DDOS are very harmful for security system as well as authentication and Privacy are big challenges. In future we analyze vehicular network using hybrid prevention method.
REFERENCES
[1] Y.Qian, N.Moayeri,”Design of Secure and Application Oriented Vanets”Vehicular Technology Conference, 2008. VTC Spring 2008. IEEE,11-14 May 2008, Singapore.
[2] J. Jakubiak, Y. Koucheryavy,”State of the Art and Research Challenges for VANETs” Consumer Communications and Networking Conference, 2008, 5th IEEE, date: 10-12 Jan. 2008, pp: 912-916.
[3] M. Raya, J. Pierre, Hubaux,”Securing vehicular ad hoc Networks” Journal of Computer Security,vol.15, january 2007, pp: 39-68. [4] A.Weimerskirch,J.J Haas,Y.C.Hu,K.P.Laberteaux,”Data security in
vehicular communication networks”, chapter no.09, pp309-310. [5] J. Cheambe, J. J. Tchouto, M. Gerlach “Security in Active Safety
Applications” 2nd International workshop on Intelligent Transportation (WIT) 2005, Germany.
[6] B. Parno and A. Perrig, “Challenges in Securing Vehicular Networks,”, Hot Topics in Networks (HotNets-IV), 2005.
[7] I.Ahmed Soomro, H.B.Hasbullah,J.lb.Ab Manan,”Denial of Service (DOS) Attack and Its Possible Solutions in VANET”,WASET issue 65, april 2010 ISSN 2070-3724.
[8] D.Jiang,V.Taliwal, A.Meier, W.Holfelder and R.Herrtwich,"Design of 5.9GHz DSRC based vehicular safety communication", IEEE Wireless Communication Magazine,Vol.13, No.05, Nov 2006, pp:36-43.
[9] SU. Rahman, H. Falaki, ”Security & Privacy for DSRC-based
automotive Collision Reporting,
www.cs.ucla.edu/falaki/courses/securityproject.pdf.