Fuzzy Rule based Enhanced Homomorphic Encryption in Cloud Computing
Full text
Figure
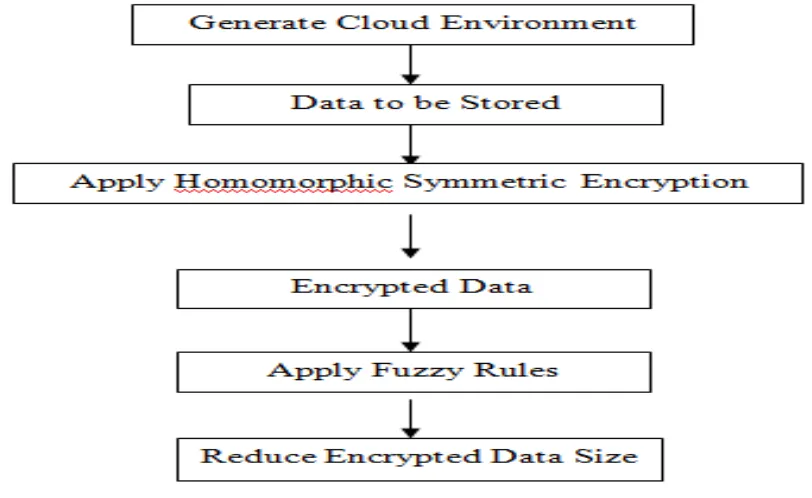
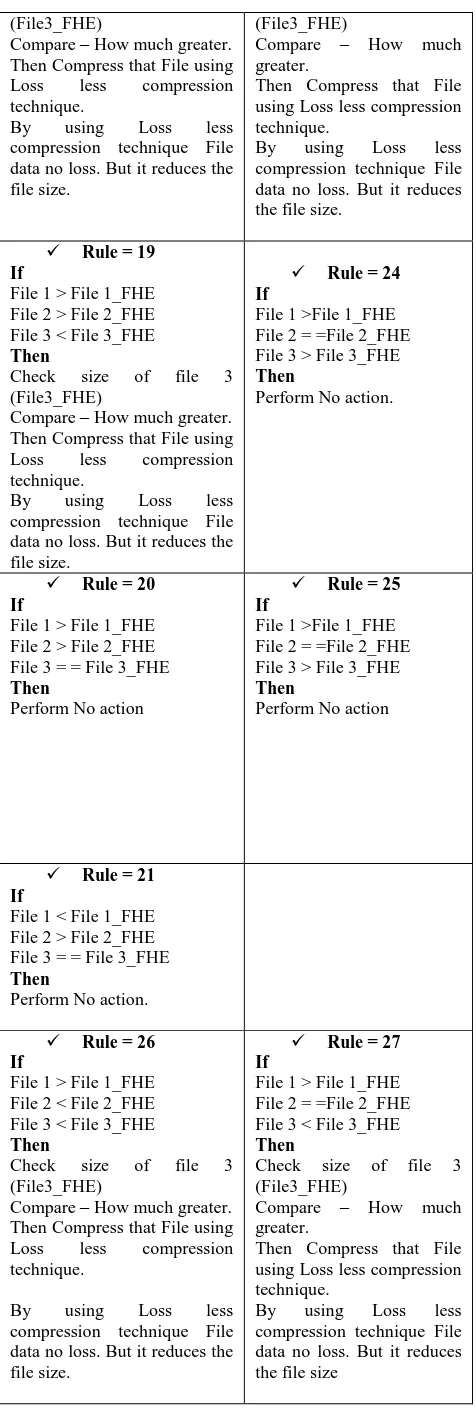
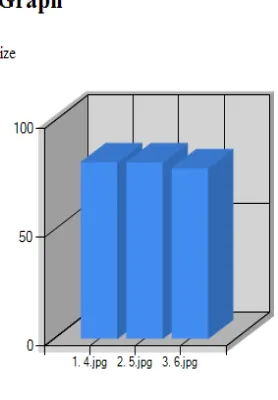
Related documents
You will hear the music twice, with a pause of 10 seconds between playings and 20 seconds before the next question starts.. There are beats in
"See here," he would say, in the middle of an argument, "I've got a fellow right here in my place who's worked there and seen every bit of it!" And then Jurgis would drop his
Second, a plethora of historiography, research articles, documentaries, Hollywood films, scale models and war memorabilia…all related to the Wehrmacht, has helped advance the notion
Some of the more innovative features some tools presented included recovering deleted messages from a logical extraction, file signature analysis on mobile devices to detect
The current study was undertaken to evaluate the pre- valence of NPM1 mutations in childhood AML in asso- ciation with cytogenetic analysis, molecular screening of common gene
Fur- thermore, our results also show that the elderly with an education beyond secondary school are more likely to accept this free influenza vaccination, while other individ- uals
“The Future of Human Resources,” Master’s Program, National Pest Management Association, Las Vegas, Nevada, October 18, 2000.. “The Difficult Employee; Disciplining and Coaching
• The largest fleet by number is the light single category - mainly utility helicopters • The medium and heavy helicopters fleet is. small in comparison but is growing faster