A Novel Approach for Hiding Encrypted Data in Image, Audio and Video using Steganography
Full text
Figure

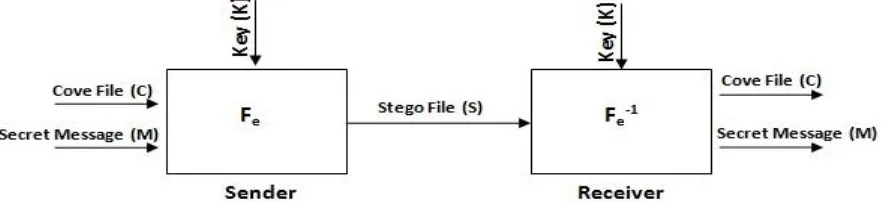


Related documents
Management of acutely decompensated chronic thromboembolic pulmonary hypertension in late pregnancy a case report CASE REPORT Open Access Management of acutely decompensated
REVIEW Open Access A brief review on molecular, genetic and imaging techniques for HCV fibrosis evaluation Waqar Ahmad, Bushra Ijaz, Sana Gull, Sultan Asad, Saba Khaliq, Shah
Turan et al BMC Pregnancy and Childbirth 2014, 14 400 http //www biomedcentral com/1471 2393/14/400 RESEARCH ARTICLE Open Access Linkage to HIV care, postpartum depression, and HIV
Similarly, the formulation presented here can equivalently be viewed as a gauge re-scaling together with a length re-scaling to ensure that for weak distortion of space-time
The configurations of complexes are realized by coordination of tertiary nitrogen of imidazole ring and it is confirmed from the 1 H NMR spectra of complexes that
The main advantage of the project is to guide the student to achieve more in their career by connecting them with the former students who are currently working
The factors were taken as Salary, job Security, Status/ recognition in public, relationship with colleagues, relationship with authority, cooperation from
The ancient duplication of the Saccharomyces cerevisiae genome and subsequent massive loss of duplicated genes is apparent when it is compared to the genomes of related species


