Highly secure cryptographic computations against side-channel attacks
Full text
Figure
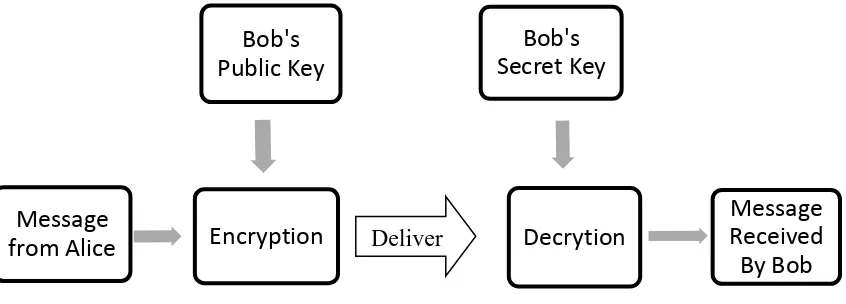

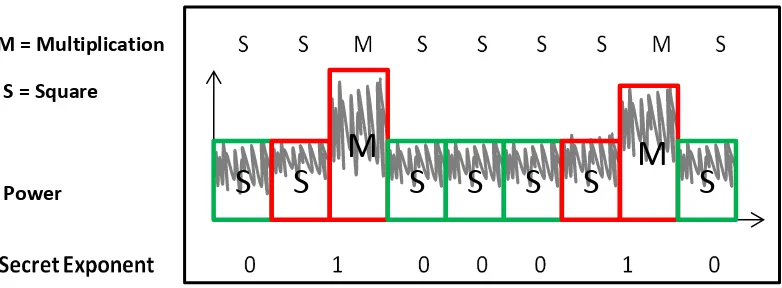

Related documents
Survey was performed involving all identified profes- sionals responsible for the PKU management in the countries from South-Eastern region of Europe (Albania, Bulgaria, Bosnia
Considering the complete panel, the stained-glass win- dow in the Dining room showed a similar surface tem- perature during the night, independently of the glass color (Fig. 4 a,
RL-29018F Ravenol Outboardoel 2T Teilsynth Ravensberger Schmierstoffvertrieb GmbH RL-29019G Ravenol Watercraft Fullsynth 2-Takt Ravensberger Schmierstoffvertrieb GmbH
This Section extends to indemnify You for liability arising out of any operation usually undertaken in the ordinary course of Business as a Hairdresser in the Business Portion of
As shown in Figure 6–Figure 8, the incoherent power angle distribution has complicated relationship with the rain environment parameters (such as rain rate, rain height) and
• Paphos: signing of St Paul’s trails, info kiosk at old harbour, promotion of Aphrodite Festival. The innovative characteristics of this project are reinforced by the use
Franchise system growth increases franchisor terminations of franchisees, but growth relying on governance, royalty rate, and clustering decrease it. Greater number of
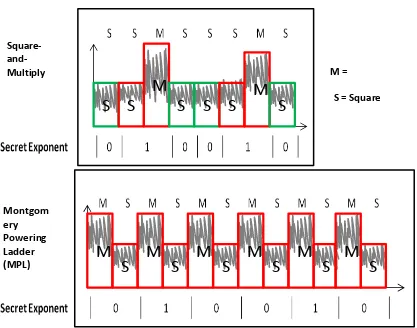
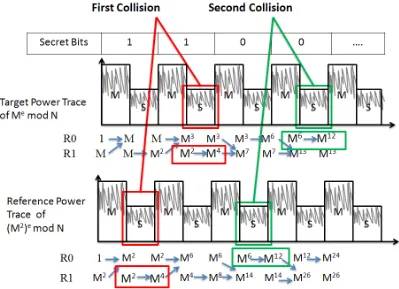
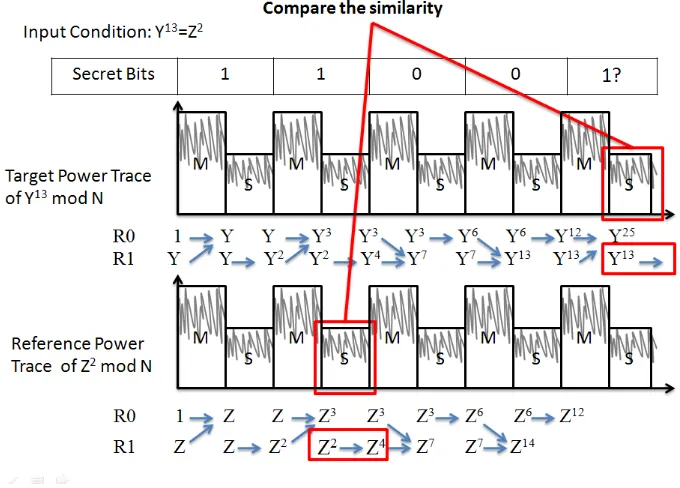
![Figure 3.1 A. Shamir's Patten for Exponent Masking [22]](https://thumb-us.123doks.com/thumbv2/123dok_us/1419715.1174514/37.612.119.531.185.405/figure-shamir-s-patten-exponent-masking.webp)

![Table 3.2 Imbalance probability for Exponent Splitting [27]](https://thumb-us.123doks.com/thumbv2/123dok_us/1419715.1174514/43.612.118.542.125.212/table-imbalance-probability-exponent-splitting.webp)