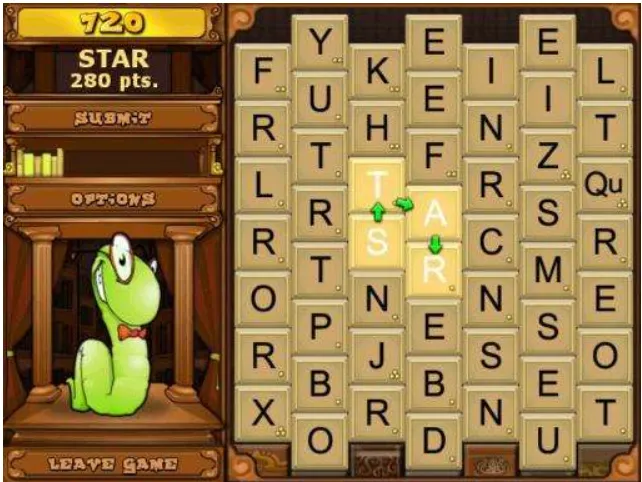
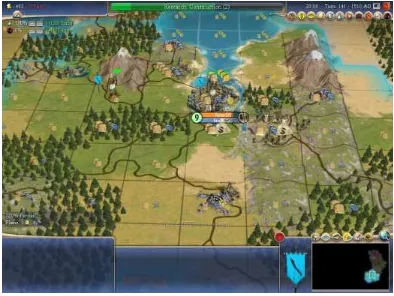
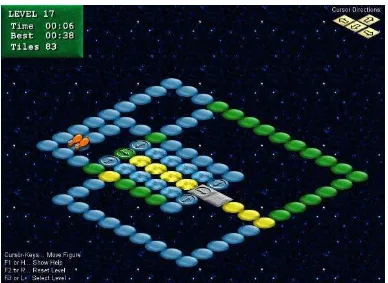
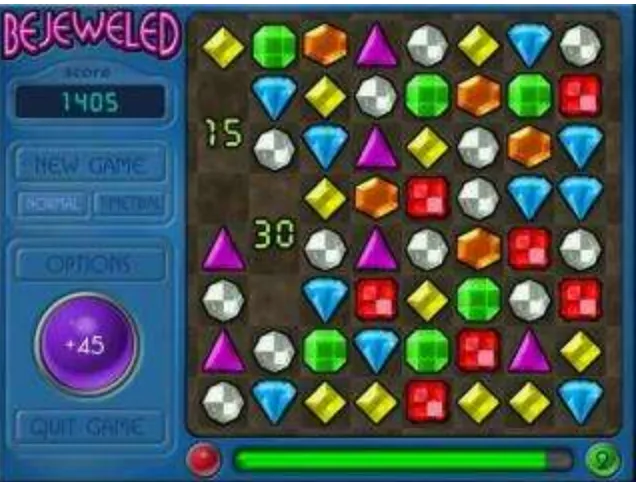
An Investigation of Cognitive Implications in the Design of Computer Games
Full text
Figure



Related documents
There are previous studies about blood stream infection and the agents com- monly caused the infection in community and hospital setting reported worldwide (Hasso et
Recently, hydrophilic rosuvastatin has been shown to be superior to lipophilic simvastatin in increasing plasma adiponectin and reducing HbA1c levels in patients with
Glass Palaces and Glass Cages: Organizations in Times of Flexible Work, Fragmented Consumption and Fragile Selves* Yiannis Gabriel.. Max Weber’s metaphor of ‘the iron cage’ has
A quick inspection of the residual images resulting from the Lena image filtering (a hard thresholding and soft thresholding has been applied with both transforms)
For example, after reviewing the laboratory notes in a Philadelphia rape case, one of the authors noticed some clues (later confirmed by additional test- ing) that the
Furthermore, while symbolic execution systems often avoid reasoning precisely about symbolic memory accesses (e.g., access- ing a symbolic offset in an array), C OMMUTER ’s test
In The Matter of Foreclosure – Panico – State Of North Carolina, Iredell County, General Court of Justice, Superior Court Division - Case
Endpoint agents with Bitdefender Endpoint Security Tools Relay role serve as communication proxy and update servers for other endpoints in the network.. Endpoint agents with relay