Interactive Encryption and Message Authentication
Full text
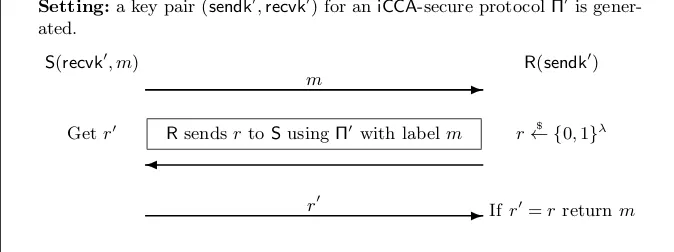
Figure



Related documents
3. Transformation analyses demonstrated that when c203-E12 DNA was introduced into a recipient strain carrying a different mating factor, A 3 , the two phenotypic
This paper presents an evaluation of an effort to incorporate an evidence-based, dual disorder treatment called Maintaining Independence and Sobriety Through Systems
Aims:As differences in promoter activity and CD30 surface expression between CD30+ lymphoid cell-lines and peripheral blood leukocytes have been shown previously to
In [7] the public variable C was the Initial Vector of a stream cipher and the cube variables were called weak IV bits whenever the de- rived function Γ turned out to be weak enough
S.. “Imaging brain amyloid in Alzheimer’s disease with Pittsburgh Compound-B.” In: Ann Neurol 55.3, S. “Widespread changes in dendritic spines in a model of Alzheimer’s
same cluster are more similar to each other than to those in other categories. Several fields like pattern recognition, image analysis, machine learning and information retrieval
Green manure amendments stimulate soil microbial growth, enzymatic activity, microbial biomass carbon and nitrogen with subsequent mineralization of plant nutrients
There are no risk factors associated with amoebiasis transmission among patients attending Longisa County Hospital in Bomet County, Kenya.. 1.6 Objectives of