Data Encryption Key Sharing Using Image Pixel Color Value
Full text
Figure
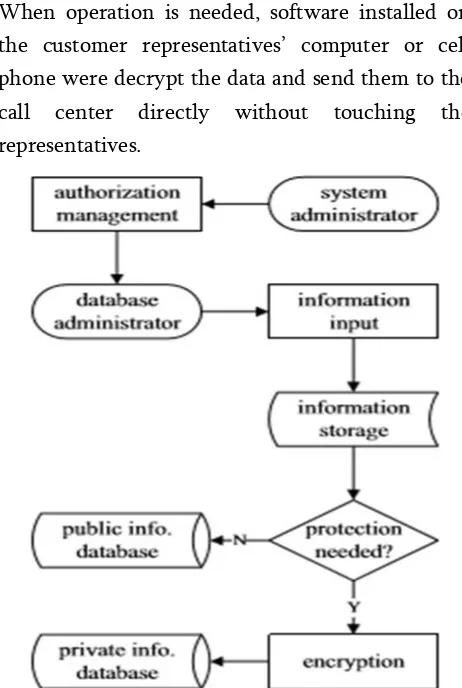
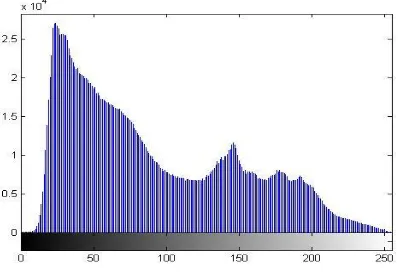
Related documents
The court noted that the Chasewood and Ake opinions omit the emphasized portion of the RESTATEMENT which is essential because "it constitutes the first hurdle of
When correlated with clinical data, the phenotypic variables within these groups showed similar directions and strengths of association, with “large” phenotypes, including
First, we find that levels of known Exo1 interaction partners, including the mismatch repair proteins MSH2, MSH3, and MLH1 (30) and subunits of the MRN complex (40), which recruits
According to the court, the insurer paying a loss under a policy becomes equitably subrogated to any cause of action the insured may have against a third-party
As shown by mass spectrometry, exposure of neutrophils to PPAD-proficient bacteria reduces the levels of neutrophil proteins involved in phagocytosis and the bactericidal histone
Generally, when a Texas general partnership is dissolved, the partners continue to have liability for the debts of the partnership that existed at the time
In Rooke v. Jenson 106 the court held that the statute of limitations would not serve as a defense to an executor who undertook her fiduciary position with
pylori SS1 strain to form a biofilm using the crystal violet biofilm assay, as well as bacteria grown under various growth conditions that included different growth media,