Implementation and comparison of hybrid encryption model for secure network using AES and Elgamal
Full text
Figure
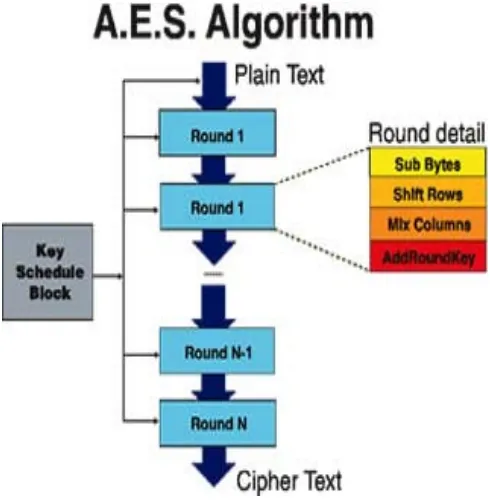
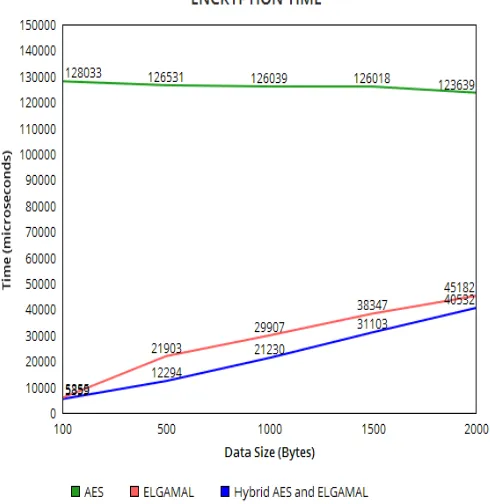
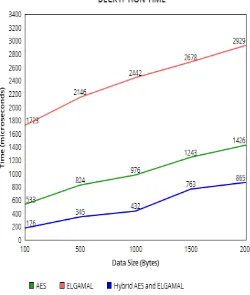
Related documents
It was found that the potential is independent (a) of the metabolite ratio employed, confirming the earlier observations of Lehmann, (b) of the hydrogen ion activ- ity, and (c)
However, when HMGR activity was reduced by the presence of lovastatin, nearly normal growth was restored at 16°C (Fig. 3B.) This result demonstrated that the increased
When Image is not corrupted, S sends the request to the ideal cloud to get the result, if the user is allowed to make such request (in one-time token mechanism) otherwise, sends
To break the chain of TB transmission and reactivation in the elderly, infection control, interventions of avoiding delay in diagnosis and containment are essential for
Keywords: Islam, Muslim society, women, affliction, privileges, restrictions, Vision, Educational status, Indian Muslims, women education, Issues and
And Film Star, Adler‟s psychological theory on inferiority complex is fit where he explains how a person suffering from inferiority complex tries to convert his inferiority
In the data mining technique, the data mining techniques used in this study are association rule, OLAP, decision tree and cluster analysis, which are broadly used for