Network Traffic Monitoring with IDS
Full text
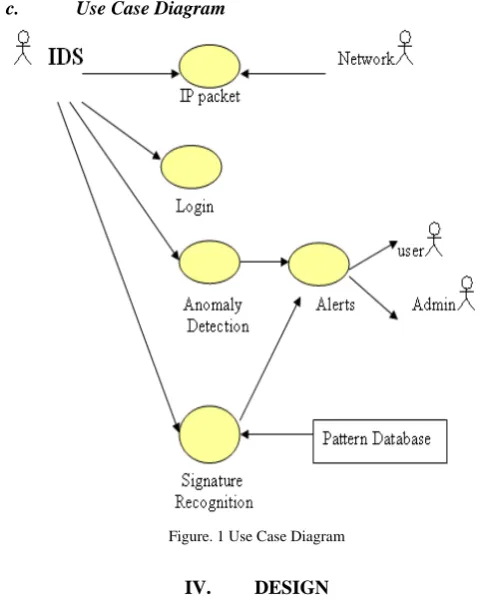
Figure
Related documents
• Greedy Algorithm (second variant): If m denotes the number of VMs to be placed, then processing time for sorting the VMs z times according to their total sink demands is O(zm log
The report is based on a dialogical examination of secondary literature on youth and civic literacy, government policy that shapes school civics and a case study in Ottawa
For graduation, students must earn a minimum of 22 credits, complete a program option, pass the High School Assessments, and earn the required number of
Thanks to the employment of at least some of these procedures, a film can be said to be ‘neorealist.’ In mapping out semantically the world of neorealism, Shiel
The goal of the test was to validate that the solution architecture can provide the required application QoS for the targeted 1000 Windows 7 virtual desktop users based on VMware
We estab- lish that, in our setting the complete and efficient network can be obtained in subgame perfect equilibrium with various dynamic network formation games: (1) We show that
o demand in the market for better quality fresh/chilled beef from Australia and New Zealand continued to grow in 2009 because the slow down
Internal insulation retrofit with ventilated wall and circulation of dry air - Focus on airflow distribution and mitigation of noise... Internal insulation retrofit with ventilated