Survey on network security using cryptography by Both decryption encryptions
Full text
Figure
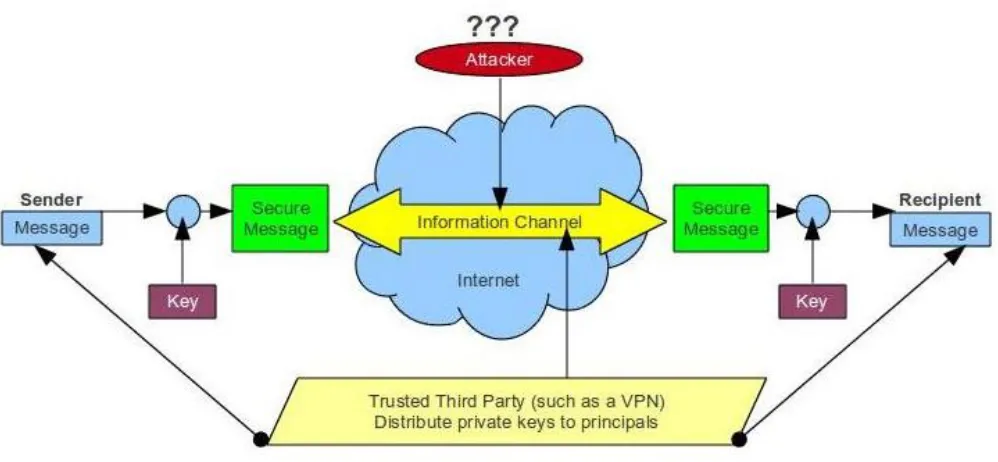
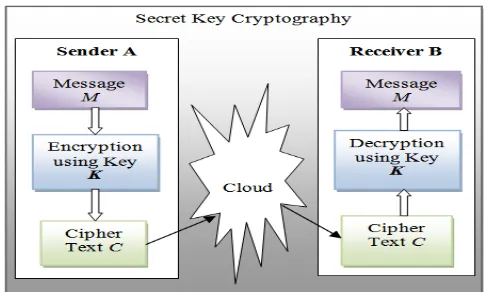
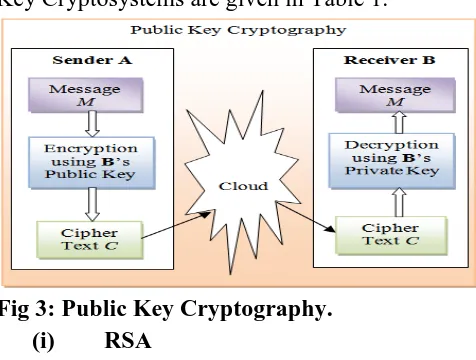
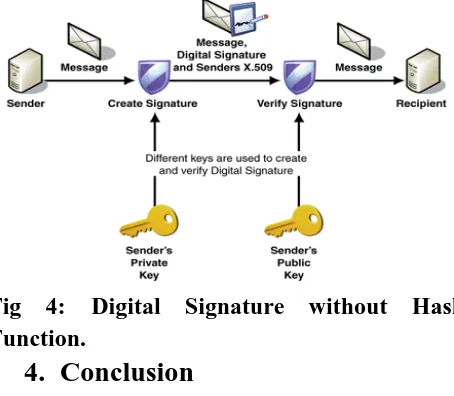
Related documents
Table 5 Association of maternal characteristics with total phytoestrogen intake among 6,441 mothers of control infants in the National Birth Defects Prevention Study.. Percent of
Future motion is predicted using dynamic and kinematic models linking some control inputs (e.g. steering, acceleration), car properties (e.g. weight) and external conditions
2006 Finishing Funds Grants Panelist for Experimental Television Center 2005 Visiting Instructor, Department of Cinema and Photography, Ithaca College 2005 Assistant,
Based on the “falling weight-soil”model, this study presented a methodology for the prediction of the combination of ground motion induced by earthquake and collapse-induced
Hepatotoxicity associated with antiretroviral therapy in adults infected with human immunodeficiency virus and the role of hepatitis C or B virus infection. Hepatitis
Abstract: In this paper we explored whether engaging in two inquiry skills associated with data collection, designing controlled experiments and testing stated hypotheses,
division of India, Pakistan won a poor share of the colonial government's financial. reserves - with 23 percent of the undivided land mass, it inherited only 17.5 percent
On the hand if the traffic is present on the road R2 then the control is sent to state S2 which switches on the signal on road R2 to green and rest of the signals are