Fully Verifiable Secure Delegation of Pairing Computation: Cryptanalysis and An Efficient Construction
Full text
Figure
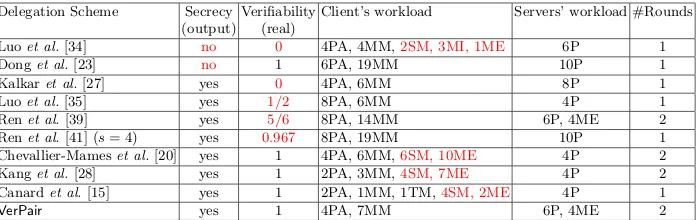

Outline
Related documents
High-power ultrasound has been proven to have potential in many applications in medicine and biology, and many existing problems and challenges need to be
Early Evidence for a Role of Chromosome Architecture in Fly Genome Function 6 Partitioning of the Drosophila Genome into Domains with Discrete Chromatin Types 8 The Hierarchical
Hu (2003) studied multi-decadal fluctuation in summer season diurnal rainfall in central United States and concluded that in the decades when the southerly
In this reaction, the enhanced photocatalytic activity of the trimetallic oxide compared to the pure metal oxides could be due to two factors: (i) the improved charge transfer
Total phenolic contents of each extract were evaluated using Folin Ciocalteau Reagent (FRC) while Ferric Thiocyanate (FTC) and 2,2-Diphenyl-1-Picrylhydrazyl (DPPH)
condition of arterial normotension Conscious rabbits Decrease in blood pressure and increase in cutaneous blood flow and heart rate variability Gmitrov, 1996 [19] 15
In RENDEL’S experiment, selection on scutellar bristles led to large changes in total make as well as small changes in competitive ability of scutellars versus
has admittance only to the distorted signal and must estimate the quality of the signal without any awareness of the 'perfect version'. NR methods can be used in any