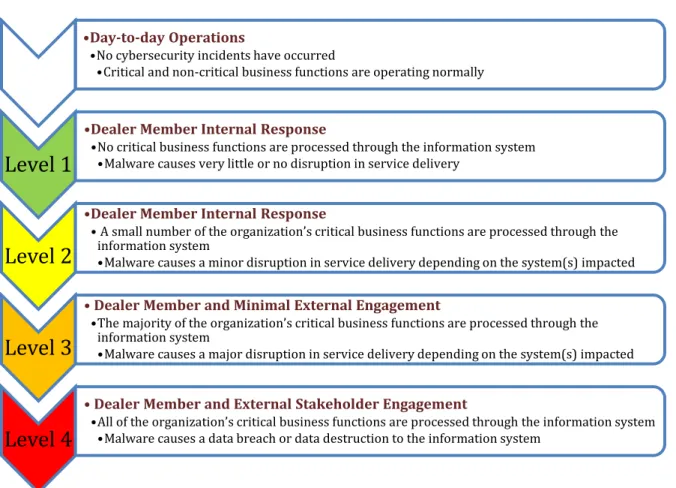
Cyber Incident Management Planning Guide. For IIROC Dealer Members
Full text
Figure




Related documents
Knowing that the cart is initially at rest and can roll freely, determine (a) the final velocity of the cart, (b) the impulse exerted by the cart on the package, and (c)
Request for information and invitation of tender Tender invitation Evaluation of tenders Due diligence and agreement proposals Negotiation Factors seen as motivational
The objective of this study was to evaluate whether time interval from handling multiple straws of semen to AI affects pregnancy outcome of lactating dairy cows housed in a
In their index framework, processing nodes are arranged in a BATON overlay network and each node builds a local B + -tree or hash index on its data.. To speed up query processing
This paper proposes a novel anomaly detection system based on the comparison of real traffic and DSNS (Digital Signature of Network Segment), generated by BLGBA model, within
Cloud Mgmt SW Enterprise Mgmt SW Other Mgmt SW Nova drivers Server Cinder drivers Storage Network AMQP DBMS Infrastructure Mgmt Capabilities Image Management. Virtual
It is the City Council’s policy that commitments of fund balance for a fiscal year must be adopted by resolution prior to fiscal year end. Amounts that have been
DHS decision makers should employ a comprehensive approach to understanding and managing risks so that they can enhance the quality of decisions throughout their organization 4 —