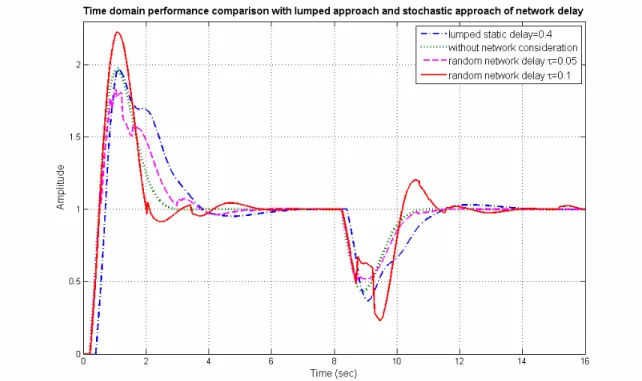
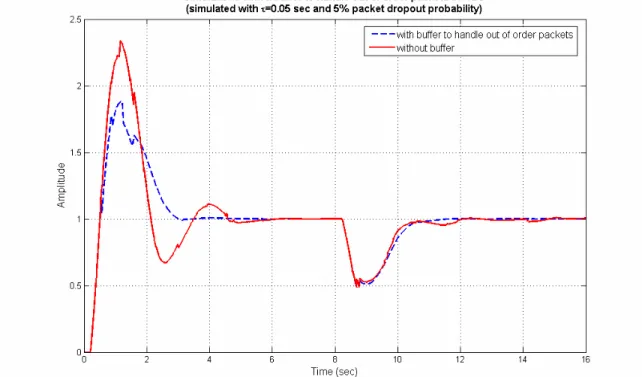
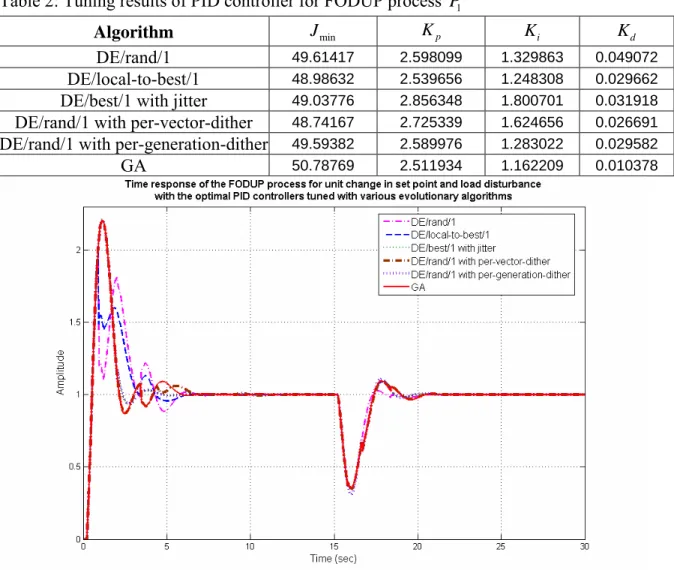
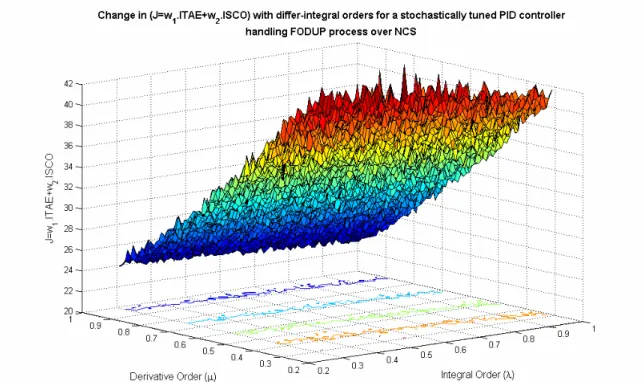
Handling packet dropouts and random delays for unstable delayed processes in NCS by optimal tuning of PIλDμ controllers with evolutionary algorithms
Full text
Figure

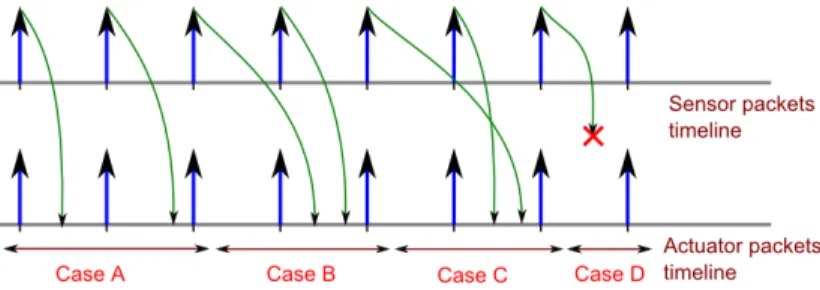

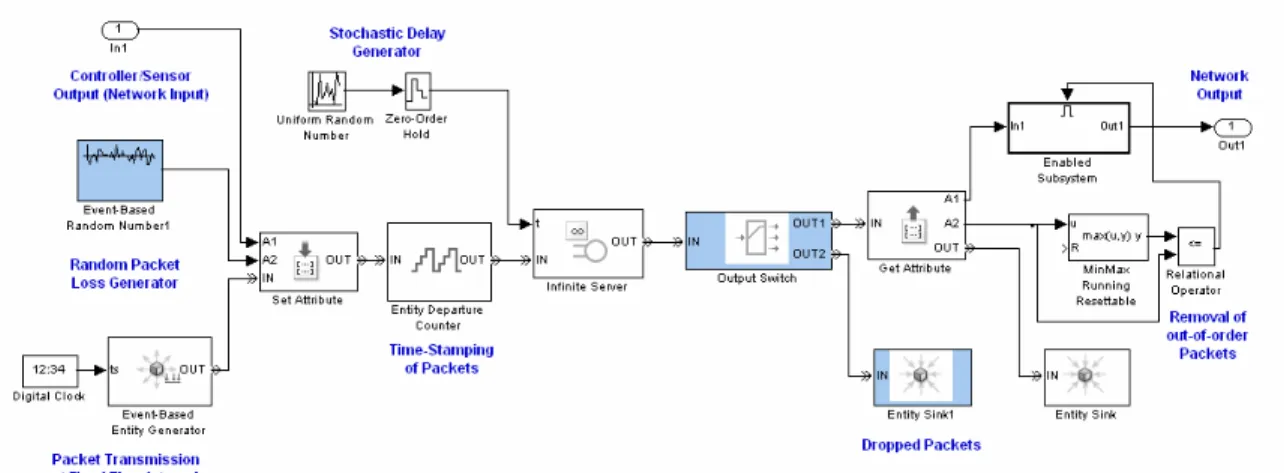
Related documents
I hereby give my unconditional permission to Emory University WOCNEC to use photographic or video images taken of me and release them for the purposes of promoting,
The authors concluded that the small number of studies addressing the relationship, plus problems with the designs of the primary studies (e.g. the time to follow-up in the
If the person is not distressed it may help to direct them to groups who share similar beliefs or experiences, since social isolation seems to accentuate distress (Read &
The need to attract new customers and the lack of readily available ties into supplier information systems force most new marketplaces to concentrate on the early sales
Following an application made to the Licensing Team for the grant of a Private Hire Drivers Licence, the Committee is requested to consider the report and determine if they consider
This data sheet provides detailed information regarding the MCP2515 product family.. MCP2561 Data Sheet – “High Speed CAN
The results indicate that the temperature, stiffness and ductility of the fire-damaged beams are significantly influenced by the load level, cross-sectional size and time exposed
This short article considers what surveillance and privacy mean to women experiencing violence and examines the extent to which such concepts have been overlaid with