Security measures for VoIP application: a state of the art review
Full text
Figure

Related documents
Participants from the 14 Southern African Development Community (SADC) countries, representing governments, industry, non-governmental organizations (NGOs), civil
In conclusion, this study showed that in a patient group with mainly moderate and severe COPD experience a loss of peripheral muscle strength and endurance, exercise capacity
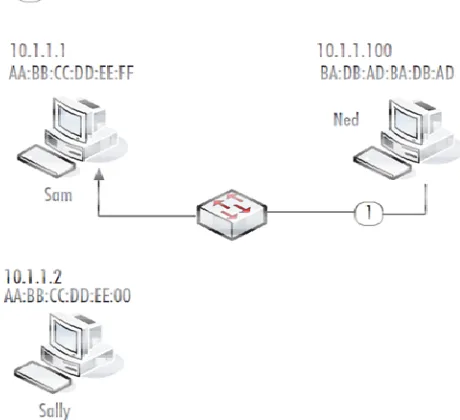
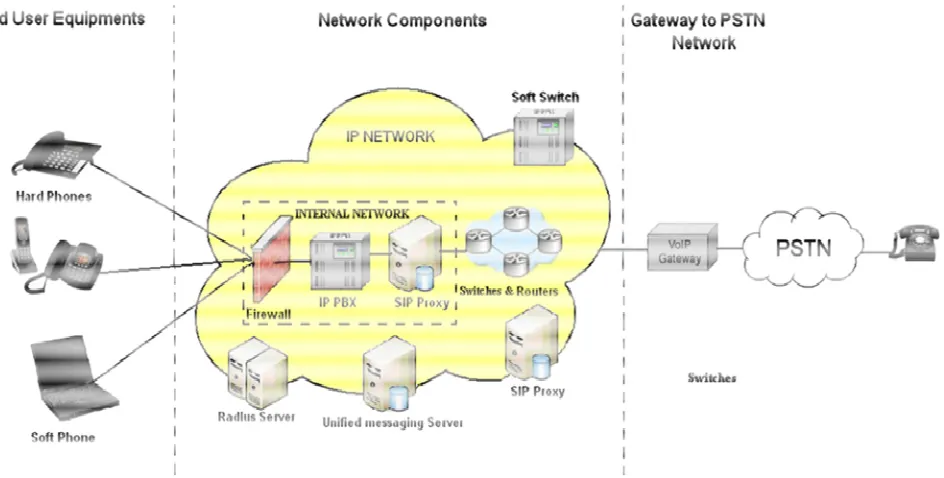
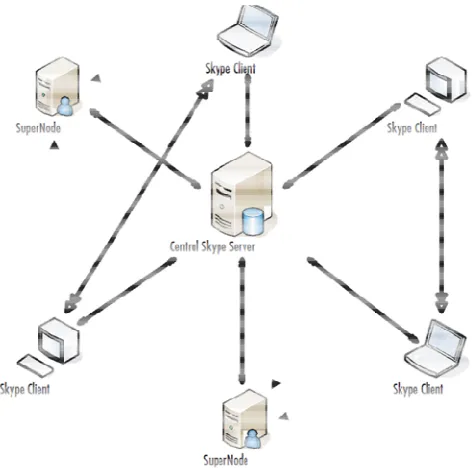
Because it offers service to the public but blocks audio media and does not allow the user to run any application, is it in violation of the FCC's rules or policies.. I am a
This research study is designed to develop forecasting models for acreage and production of wheat crop for Chakwal district of Rawalpindi region keeping in view the assumptions of OLS
Spoken samples of language from a group of ten hearing impaired children were analysed with respect to development of occurrence of verb tenses and verb inflections,
Fig. Location of the study area showing where soils were sampled [17] degradation; organic matter. Soil degradation, caused by salinization is a environmental issue that has
New policies and contractual agreements emerging from the United States and Mexico (2018-2019) have made it nearly impossible for Central American refugees to receive asylum status
It also aims at re-wording the peace education curriculum suitable and relevant for pluralistic religious society and cultural diversity like the Nigerian nation..
