Ensuring Security in Cloud Computing Cryptography using Cryptography
Full text
Figure
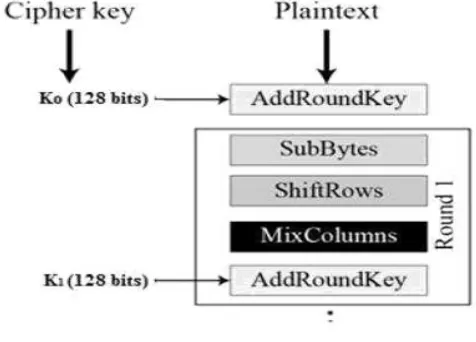
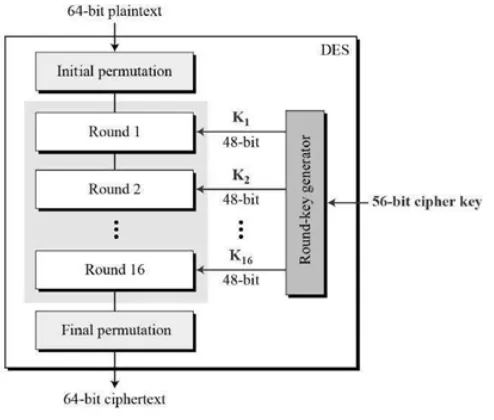

Related documents
Here we have determined that adhesion receptors in the integrin family play a role in promoting adhesion of human hematopoietic stem cells to cultured human marrow stromal
In the data mining technique, the data mining techniques used in this study are association rule, OLAP, decision tree and cluster analysis, which are broadly used for
division of India, Pakistan won a poor share of the colonial government's financial. reserves - with 23 percent of the undivided land mass, it inherited only 17.5 percent
In this review, we will introduce point-of-care ultrasound (POCUS) applications regarding the soft tissue and musculoskeletal systems: soft tissue infections, joint effusions,
The solid curves show the expected total numbers of (a) outpatients, (b) hospitalizations, and (c) deaths, respectively, during a pandemic wave in a population of 100,000
PROCEEDINGS Open Access Considering interactive effects in the identification of influential regions with extremely rare variants via fixed bin approach Michael Agne1*, Chien Hsun
pengurusan pembelajaran di Universiti Tun Hussein Onn Malaysia dengan meninjau aspek dernografi responden, kekerapan penggunaan papan perbincangan di kalangan yelsjar, faktor-faktor
This new algorithm of Sage filtering considering the model systematic errors adopts Sage filtering established to estimate the kinematic model systematic error as well as the