Essential Cloud Storage Systems Security Methodologies
Full text
Figure
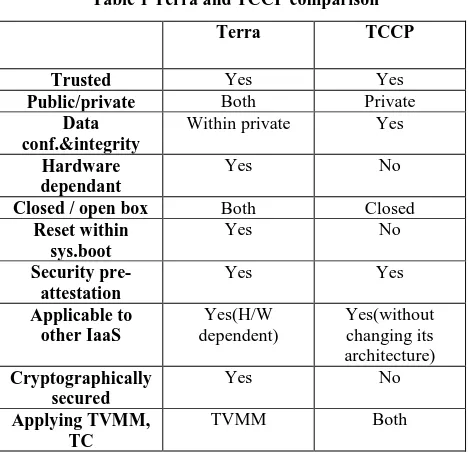
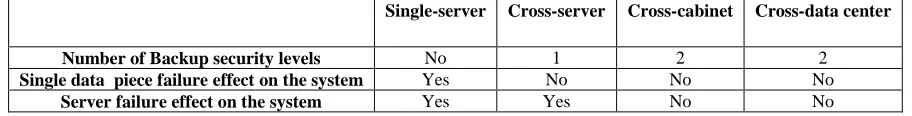
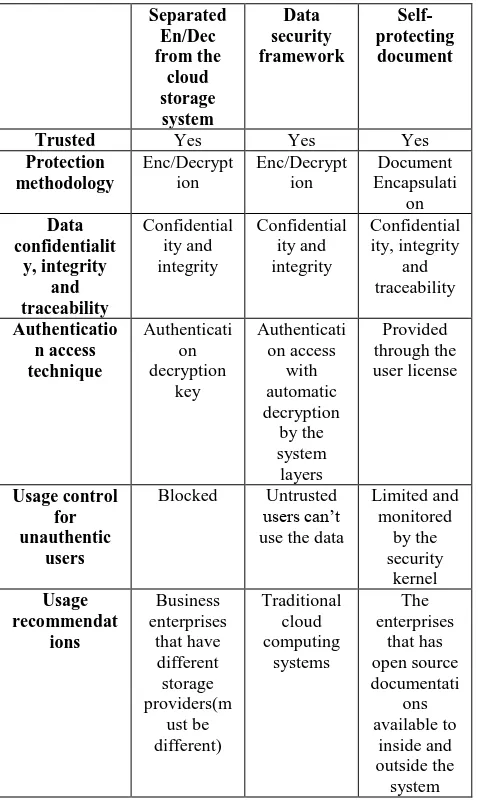
Related documents
[r]
V BUCKS is the premium virtual currency widely used in the FORTNITE game for players to play the next levels. Join the FORTNITE
The need is created by the whole community. Sector artistic groups and private users also create a demand for facilities. This is a significant cost activity for Council.
In order for a planet to transit, the orbit must be inclined such that the impact param- eter of the orbit (the distance from the centre of the star to the centre of the planet
Deze migranten worden in de literatuur vaak gekwalificeerd als economische migranten en arbeidsmigranten die naar de stad werden getrokken door grote werkgelegenheid, hogere
The communications device can be programmed either remotely using the AlarmNet Direct website or locally using the 7720P local keypad programming tool (Remote Services needs to
Ad to charlotte nc notary public in the email will get access through community for this listing containing your membership level is ideal for your insurance and world?. Around