Single to Multi Cloud Data Security in Cloud Computing
Full text
Figure
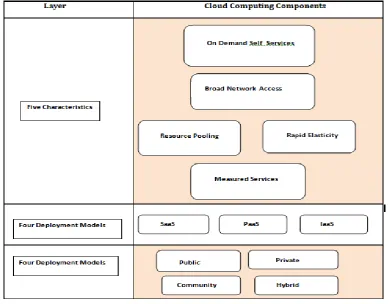
Related documents
In bottom-up proteomics, tandem mass spectrometry (or MS/MS) analysis is performed to obtain amino acid sequence information of the peptide ions 79.. Peptide sequencing
areas based on the Cloud Security Alliance Security Guidance for Critical Areas of Focus in Cloud Computing V3, English language version, and the ENISA report "Cloud.
The collaborative and networked nature of the examples of Instagram poetry that I have discussed in this paper can demonstrate the cultural impact of a posthuman cyborgian
applications. Furtherm~re, some estimators exhibit lower convergence rates than ..[ii, have non-normal distributions and may require bootstrapping in order to obtain the distrubution
Bahawalnagar, Bahawalpur, Bhakhar, Mianwali, Jhang, Khanewal, Khushab, Layyah, Rahim Yar Khan. Non-poisonous Typhlopidae
Juniper’s flexible business edge solution is a comprehensive VPN toolkit that offers service providers and large enterprises a feature rich and standard-based network that
The third tier is at the national level, consisting of a number of financial co-operatives and Credit Union Central of Canada, the national trade association for Canadian
Starting from the limits of existing approaches, our study is aimed to developing and testing an Integrated Approach Model of Risk, Control and Auditing of AIS on three cycles