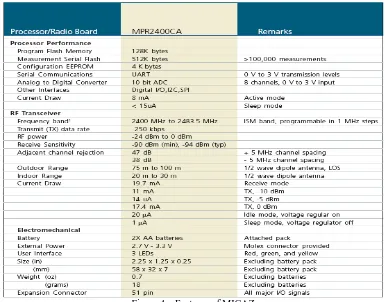
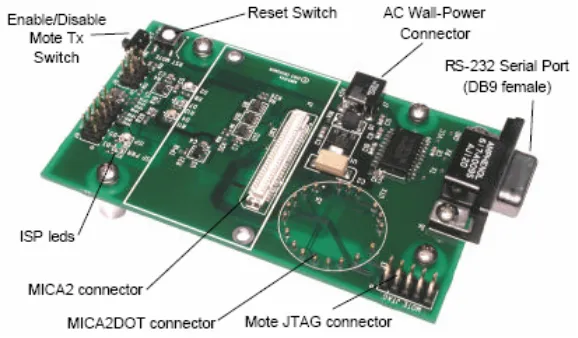
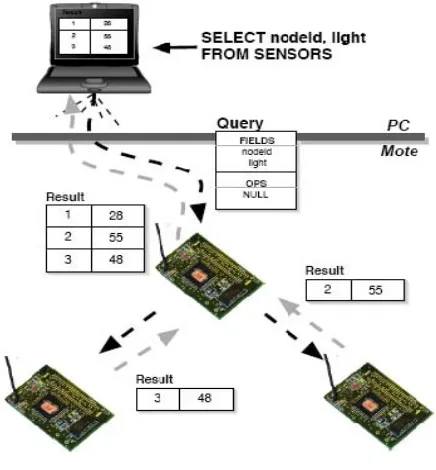
Implementation of Secure Key Management Techniques in Wireless Sensor Networks
Full text
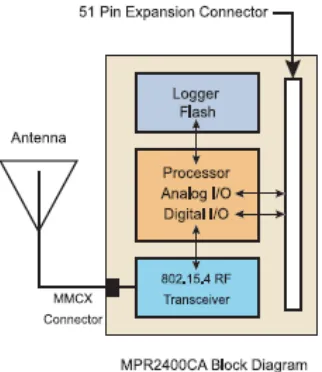
Figure
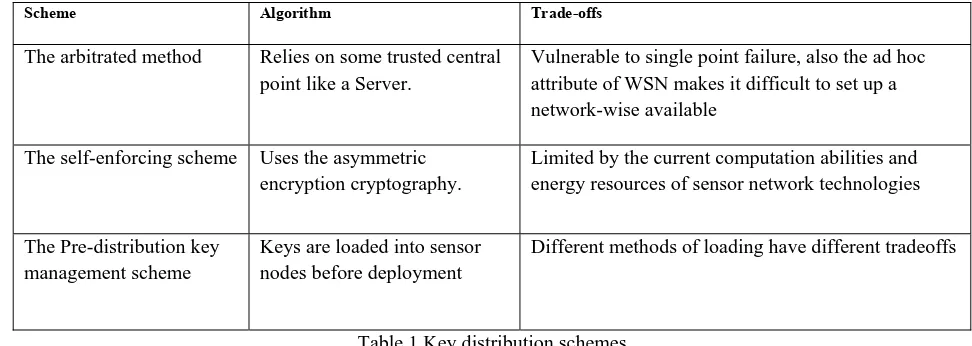
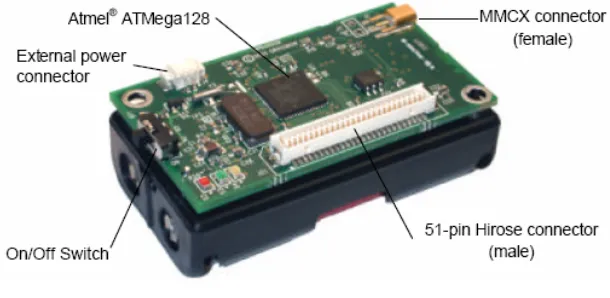
Outline
Related documents
Keywords : genetic algorithms, Java, kurtosis, particle swarm optimization, projection index, Tribes, projection matrix, unsupervised data analysis...
Genotype X Environment Interactions Over Seven Years for Yield, Yield Components, Fiber Quality, and Gossypol Traits in the Regional High Quality Tests.. Gannaway, Kathy Glass,
The research method is fundamental in terms of purpose and in terms of data collection it is descriptive- casual comparative and it is in terms of method of study is
2010 "Structuring Islamic Identity in Europe and Israel: Outlines for a Comparative Discussion," Conference on Muslim Minorities in Non- Muslim Countries: The Islamic
In the present study, we determined the major phen- olic compounds of exGrape® grape seed extract by an improved HPLC method and analyzed the effect of con- sumption of this product
One indicator of development success can be seen from the rate of economic growth, economic growth is defined as an increase in Gross Regional Domestic Product
WEIGHT-BASED DEROGATORY MEDIA: PREDICTORS OF MEDIA WEIGHT-BASED DEROGATORY MEDIA: PREDICTORS OF MEDIA SELECTION, IMPACT OF EXPOSURE, AND THE MODERATING SELECTION, IMPACT OF