Network Security Analysis by Using Business Intelligence
Full text
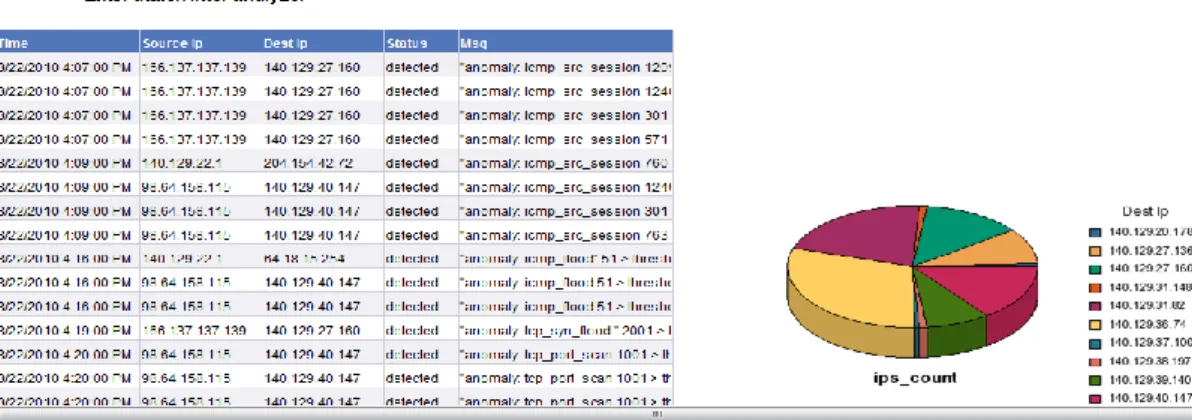
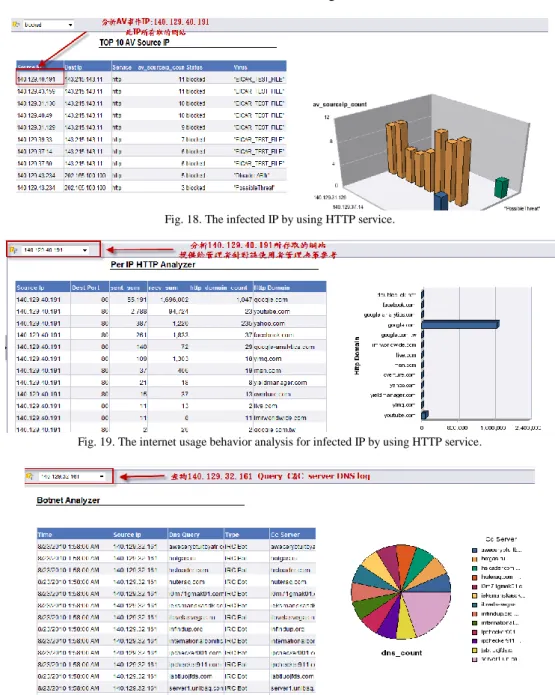
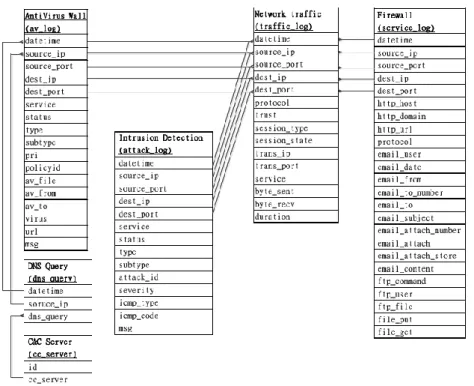
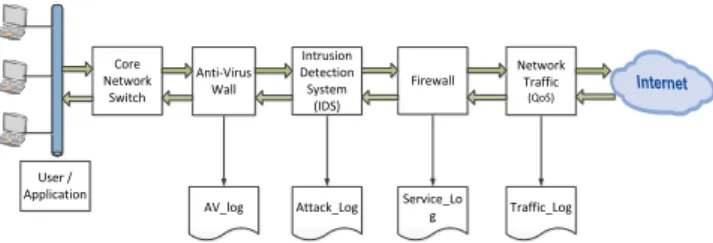
Figure
Related documents
“THE SAFETY OF PEOPLE TAKES PRECEDENCE” Science 2 SCIENCE ROAD YOU ARE HERE Carbon Dioxide Extinguisher Emergency Assembly Area EXIT. Break Glass Alarm
Clinical outcome parameters by BIA include total and regional SMM for diagnosis of sarcopenia (Chien et al. 2010); and bioelectrical impedance vector analysis (BIVA),
Compared to the same period of the previous year, net provisioning for impairment losses fell by a total of 59 per cent, or € 155 million, to € 106 million.. This was due to a €
The in vitro whole blood incubation of self assembled monolayers enabled to study the effects of surface wettability and charge on hemocompatibility parameters like protein
Arguably the most critical role that parties can potentially play in peacebuilding is to aggregate and represent the interests of different groups in bargaining processes
For each non-prescribed exception account held by the account-holder and included in the FCS balance use a separate record line and repeat all other data items Account title
The diversity and the advanced level of the used technologies in IT projects with increasing com- plexity leads to an exponential diversification of risk factors.The purpose of
Before joining these laboratory activities, students took a pre-test to rate their own concepts on renewable energy. At the end of these laboratory activities, they took a