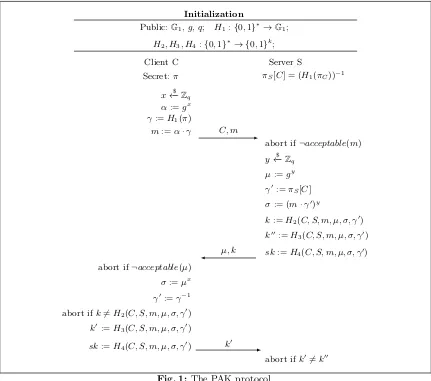
Tightly-Secure PAK(E)
Full text
Figure

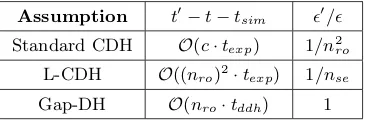
Related documents
One of the alternative measures of farm revenue that has been proposed as an insurance contract is milk revenue less feed purchases which better captures the impact of crop
The majority of the students said that the coursebook objective was relevant to their needs, the contents were complete, the topics were interesting and were relevant
Generic types: The challenges that can be categorized under general level are traditional security tools, and use of different technologies. TECHNICAL CHALLENGES IN
You are being invited to participate in this research study examining new graduate nurses’ transition to practice because you are newly graduated practicing registered nurse and
You may keep your notes in a spiral notebook – a 70 page one will be fine as we will be using it throughout the year for other reading assignments.. You may take notes however
5 See Article 6.1 of directive 2009/28/EC: “A statistical transfer shall not affect the achievement of the national target of the Member State making the transfer.” This clause
This project focuses on the impact of experimental parameters; laser energy and gate delay on the SA coefficient of emission lines which depends on two plasma parameter
For cyclic loading with positive load ratios (e.g. monotonic pipe fracture test with several un-loading), the compressive plasticity is insignificant and hence the calculation of