Security to wireless sensor networks against malicious attacks using Hamming residue method
Full text
Figure
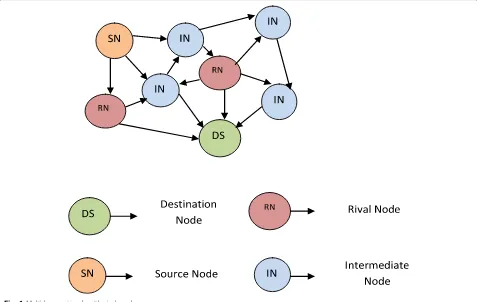


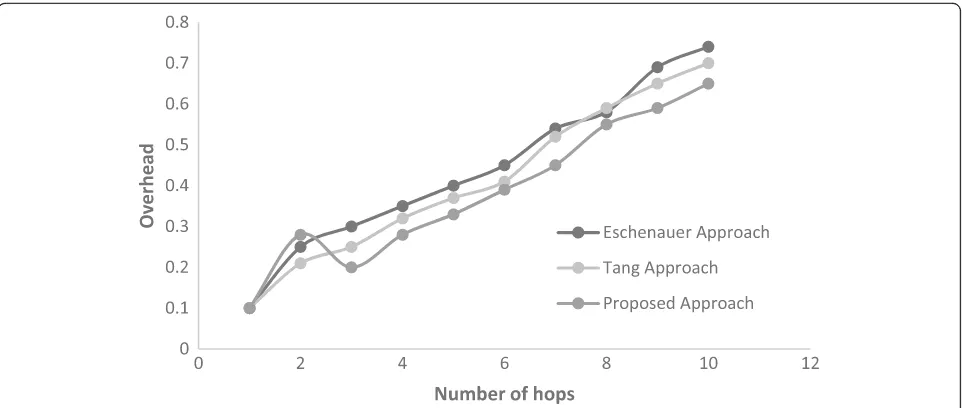
Related documents
As per Ravi Kumar [1] - higher concentration of sodium hydroxide in the solution results in lower compressive strength of GGBS based geopolymer concrete.. The compressive
The region where the transition from the axisymmetric state to the wave flow regime occurs shows qualitative agree- ment with the computed neutral linear stability curve (blue graph
Therefore, it can be concluded that the efficacy of cognitive behavioral therapy and transcranial magnetic stimulation therapy are effective in reducing depression in patients with
AF: annulus fibrosus; CM: control medium; FACS: fluorescence-activated cell sorting; FBS: fetal bovine serum; FSC: forward scatter; IVD: intervertebral disc; MSC: mesenchymal stem
Social support among HIV positive and HIV negative adolescents in Umlazi, South Africa changes in family and partner relationships during pregnancy and the postpartum period Hill et al
Macro and microscopic findings of ICG fluorescence in liver tumors WORLD JOURNAL OF SURGICAL ONCOLOGY Shimada et al World Journal of Surgical Oncology (2015) 13 198 DOI 10 1186/s12957
The main objective of the present paper is to characterize the scattered field from the transmitter to the receiver according to urban parameters (shape of buildings, density
Method: This paper examines the psychometric properties of the AMC Linear Disability Score (ALDS) project item bank using an item response theory model and full information