A Hybrid Security Model for Distributed Cloud Management
Full text
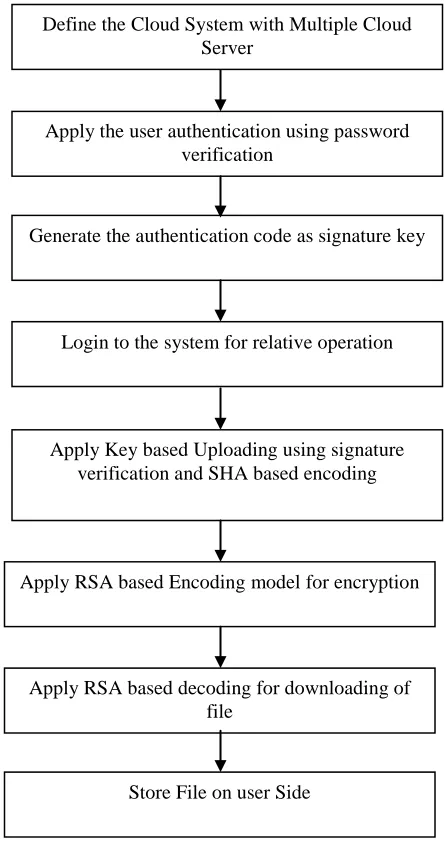
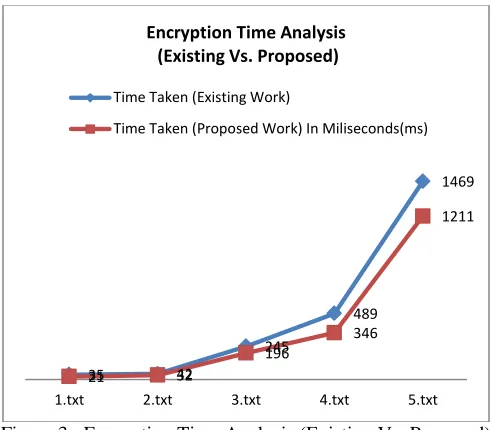
Figure

Related documents
Key words: Ahtna Athabascans, Community Subsistence Harvest, subsistence hunting, GMU 13 moose, Alaska Board o f Game, Copper River Basin, natural resource management,
All stationary perfect equilibria of the intertemporal game approach (as slight stochastic perturbations as in Nash (1953) tend to zero) the same division of surplus as the static
Comparisons with Binary Images: As the original spatial pooling algorithm (BSP) was unable to converge on the greyscale images, we ran a separate ex- periment using the same set
What this means is that a damage detection tool must factor out the impact of pitch and wind speed to make an inference on the presence of damage in a blade (Frost et al., 2012).
Video record from deaf people as model Malaysian Federation of the Deaf (Persekutuan Orang Pekak Malaysia) CD-ROM containing Guidelines to Sign Language (CD-ROM by
The proposed l 1 -POFR algorithm integrates (i) the model regressor selection based on minimizing the LOOMSE; (ii) regularization parameter optimization also based on minimizing
This study reveals some significant points: (1) The pattern of interaction between the family of former terrorists convict and surrounding communities can be
Day 20 PCR results (Figure 2) showed one faint positive band on one of the 2 yolk samples collected from that embryo at that time point, but no other positives were detected. Day 21