RFID and Face Recognition Based Security and Access Control System
Full text
Figure
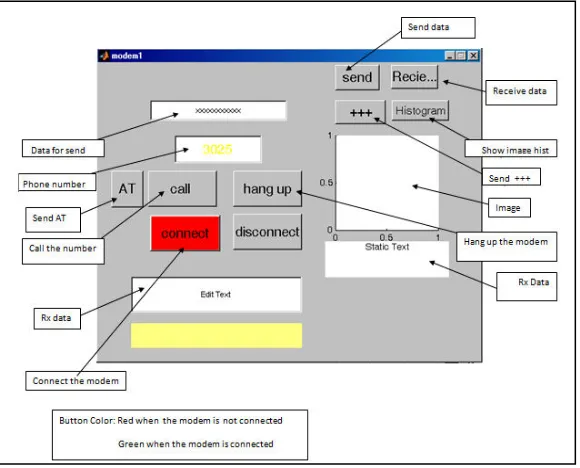

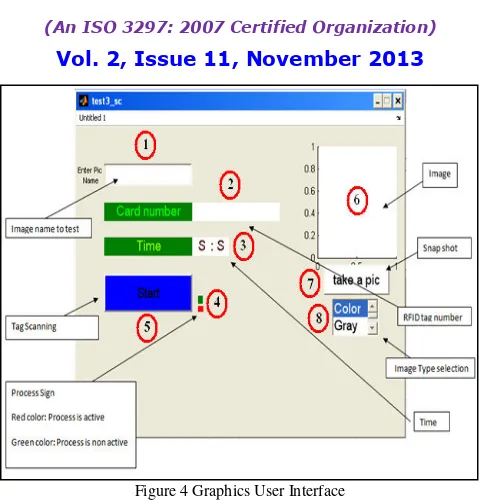
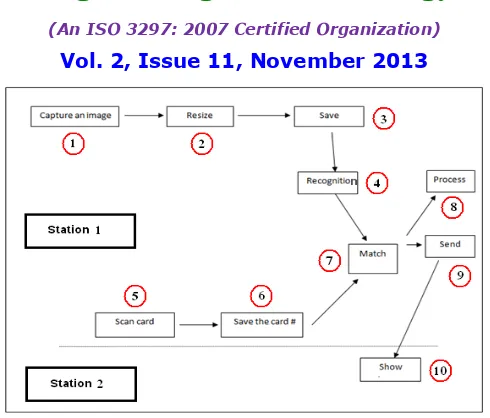
Related documents
of the most common Eimeria species known to infect domestic pigs were detected during 227. analysis of faecal samples collected from pigs in Punjab,
Objective: The aim of the research was to study the effect of font style and size on memory among the pre-clinical medical students in Universiti Kuala Lumpur Royal College of
However, the literature clearly frames recruitment activity as occurring across a pipeline that extends from secondary through to tertiary education contexts and in some
Abstract—The purpose of this paper is to extend to spinor electromagnetism the differential forms, based on the Cartan exterior derivative and originally developed for tensor fields,
The results reveal that on an average the illuminance levels by artificial lighting in the lectures halls in blocks (G), (F) (HCIM) is excellent as compared with
Aavishkar Comprehension Test was constructed for the measurement of dependant variable, which contained three main elements i.e., textual comprehension, comprehension of
breed of silkworm Bombyx mori MU53 with shorter larval duration for
A tap-coupled structure is utilized to feed the two resonators at lower passband and a coupling structure is used to feed the two resonators at the upper passband1. Two pairs