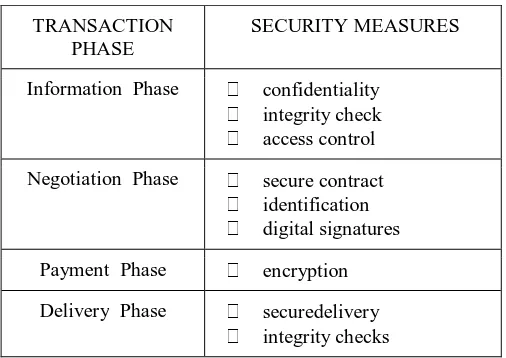
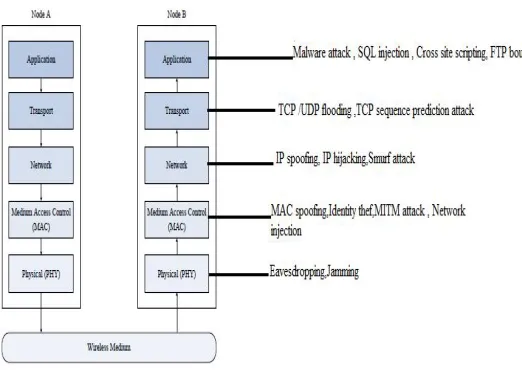
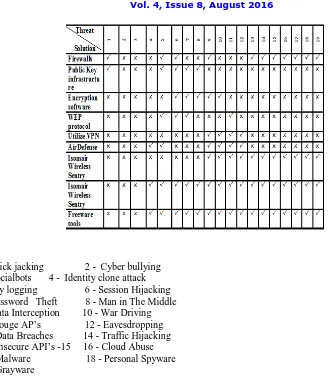
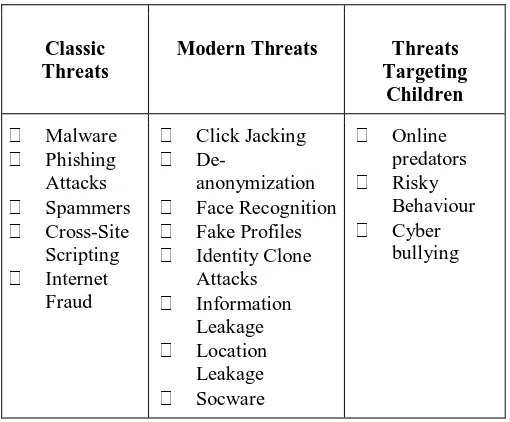
[NORMAL] A Survey on Current Cyber Threats, Their Issues and Solutions
Full text
Figure



Related documents
This includes careful operation and maintenance, development of a replacement strategy (particularly when lack of spare parts is a reality), and mitigation of ageing
However, the LMSR also suffers from several drawbacks, some serious: (1) Although it is bounded, the market maker does typically run at a loss, which can be large, (2) A
Many scholars and teachers are interested in and writing on multimodality and the importance of utilizing digital technologies to produce multimedia texts, but far too often are
In collaboration with concerned stakeholders, the role of WCAT is to provide marketable skill training including life skills on the identified value chain that can
Quality Requirements Quality Attributes Selection Monitoring Model Generation Model2Text Transformation in SaaS Quality Model guides Selected Attributes in Service Level
As River North office occupancies have strengthened, tech startups and creative firms have swung their attention to the other traditional CBD submarkets (e.g. West Loop, Central
High-flow oxygen therapy for neonates, defined as continuous flow of greater than 2 L/min delivered by nasal cannula, gen- erates continuous positive airway pressure when the can-
Modeling using Discrete Event Simulation: A Report of the ISPOR-SMDM Modeling Good Research Practices Task Force-4.. Jonathan Karnon, PhD 1, *, James Stahl, MDCM, MPH 2 , Alan