Study of Dual Watermarking Technique for
Image Security
Prof. Darshana R. Patil 1, Surabhi Tupe 2, Sonali Walke 3 , Resham Pawar 4 , Diksha Pujari 5
Assistant Professor, Dept. of Computer Engineering, JSCOE, Hadapsar, Pune, India1.
UG Student, Dept. of Computer Engineering , JSCOE, Hadapsar, Pune, India2, 3, 4, 5.
ABSTRACT:- In different applications, pictures are touchy and inclined to assaults such that any change in it could prompt significant issues. For instance, modifying any area of a medicinal picture could prompt wrong medications. In this way, distinguishing fraud/fake in pictures are an obligatory and recuperation of tempered areas is important. The principle offer of this paper is to propose another Dual Watermarking (DW) plan, which goes for identifying any change, fabrication/fake, or unlawful control of pictures regardless of the possibility that it is small. Our proposed plan is a protected, delicate, and a reversible watermarking plan. This plan progressively creates the watermark utilizing chaotic models. A Chaotic model is iteratively connected to create the riotous arrangements taking into account the combining so as to star qualities, which are dictated the estimations of pixels of picture, position data and key. It is inserted inside the picture by growing intra plane distinction between any two shading planes of picture. It is known as intra-plane distinction growing. At the beneficiary, an identifier extricates the watermark and limits the altered locales without access to the host picture or the first watermark. The tempered areas are recouped picture is a grayscale picture. The proposed plan is extremely delicate to adjustments anyplace in the picture regardless of the fact that it is too little.
KEYWORDS:- chaotic system, digital Image, Digital watermarking, Image authentication, integer transform, reversible, fragile.
I. INTRODUCTION
Improvement of the Internet as well as advanced interactive media gives us extraordinary points of interest, for example, amazing lossless computerized media, simple altering, and high devotion duplicating. This simplicity, by which advanced data can be controlled as well as copied, has made distributers, creators, restorative pictures, specialists, and picture takers apprehensive that their developments and items going to be changed illicitly or asserted by others. So, we require a procedure for checking content's trustworthiness of the computerized media and recuperate tempered locales. Copyright security and Authentication assumes a vital part here. Duplicate right insurance ensures proprietor's licensed innovation and follows the unlawful duplicates of the substance. Verification watches that the got picture has been changed or not and limit the altered areas. All in all, watermarking procedures utilized for uprightness validation have the accompanying properties.
1) Tamper detection is the fundamental feature to a tamper proofing system, in this detector in the system should determine whether an image is veritable.
2) In Localization of modification, the verification result after extraction should be able to reflect and locate the modified regions.
3) Perceptual transparency: An embedded watermark should be perceptually invisible under normal observation. 4) Blind detection: An authentication process of Image does not require host image. Image is verified using embedded watermark.
5) Robust or fragile property: Most fragile and semi-fragile algorithms aim to detect the malicious tamper operations. So, robust schemes can also serve this purpose.
II. RELATED WORK
• A Messy Watermarking for Medical Image Authentication
S.Poonkuntran proposed watermarking scheme in this paper works in four stages. The first stage selects the reference color plane for generating watermark. The second stage generates the watermark using the reference color plane through messy system. The embedding process is carried out using integer transform in the third stage. The fourth stage performs the extraction and verification process. The proposed scheme is very sensitive to the jittering, geometrical and various filtering attacks; thereby it modifies around 40% of the watermark for jittering geometrical attacks and around 45% of the watermark for filtering attacks at an average.
• Pinpoint authentication watermarking based on a chaotic system
A very high-capacity algorithm based on the differenceexpansion of vectors of an arbitrary size has been developed by Yao Zhao for embedding a reversible watermark with low image distortion. Test results of the spatial, triplet-based and spatial, quad-based algorithms indicate that the amount of data one can embed into an image depends highly on the nature of the image. The test results also indicate that the performance of the spatial, quad-based algorithm is superior to that of the spatial, tripletbased algorithm at higher PSNR.
• Information Hiding-A Survey
Fabien A. P. Petitcolas gave an overview of information hiding in general and steganography in particular. We looked at a range of applications and tried to place the various techniques in historical context in order to elucidate the relationships between them, as many recently proposed systems have failed to learn from historical experience.
• Reliable Detection of LSB Steganography in Color and Grayscale Images
Steganography is a tool using which the very act of communication can be concealed. In combination with cryptography, it provides a very secure mode of communication. While privacy is an important aspect of our lives, steganography can be and has already been misused.A reliable and accurate method for detecting least significant bit (LSB) nonsequential embedding in digital images.
III. SCOPE OF RESEARCH
This system is used to avoid Abuse or duplication of data. In the digital world the piracies of images will detected by using this technique.
It can used to avoid Social violence.
In our project the security requirement of image and authentication also achieved.ng any region of medical images could lead to wrong treatment.
Copyright protection and authentication use for security of images.
This motivates us to propose a Digital watermarking for copyright on Android platform.
IV. PROPOSED METHODOLOGY AND DISCUSSION
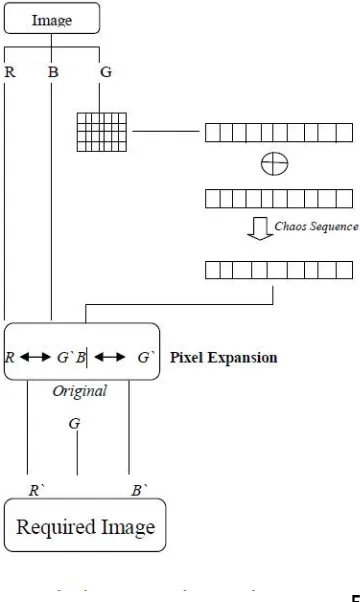
Fig.System Architecture
• Identification of Reference Color Plane:
At that point we split the given computerized picture into its three bit planes. Since, every pixel of thepicture is of 24-bit, we isolate it into 3 unique bytes of RGB planes. At that point we select a reference plane whose slightest huge bit of each pixel in the advanced picture would be utilized to produce the watermark that is required amid implanting stage. That is we store the minimum critical bit values for each pixel for a reference plane and utilization it for delivering watermark.
• Generating Watermark Using Messy System:
Untidy framework is a dynamic framework whose conduct changes as per time. These progressions are exceptionally touchy to the beginning conditions. In this way, the conduct of untidy framework gives off an impression of being arbitrary, however they are deterministic. The dynamic changes of this framework are totally characterized by their beginning conditions with no arbitrary components. Hence, the watermark is created through chaotic framework utilizing the reference shading plane as beginning condition. Subsequently, the watermark is created powerfully.
• Embedding By Intra Plane Difference Expanding:
The pixel pairs are formed from red and blue color plane's pixel values. This is known as intra plane difference expanding. Thus, the difference between the pixels from different (Red and Blue) color planes is expanded for embedding watermark in the proposed scheme. Thereby, the watermarked image (W_img) is generated for the given Original image (Img).
• Generation Of Second Watermark Using (α-Channel):
Subsequent to installing the first progressively created watermark with the assistance of pixel distinction development in the picture, the watermarked picture (W_img) in this stage is again part into RGB planes. We here utilize the idea of
the α–channel. This watermark is again alterable and is one of a kind, as it is produced from the picture's pixels once
more. Here, what we do is, we create α-channel with the red's assistance, green and blue estimations of all pixels. The normal of the RGB values for each pixel in the picture is discovered for the era of the α-channel. The α-channel
• Extraction And Verification:
In the extraction prepare, the watermarked picture W_Img is handled in the same route as unique picture handled for implanting. The extraction procedure is finished visually impaired. Both unique picture and unique watermarks are not utilized for the extraction process.In this stage we check if the picture has been harmed or not with the help the two
watermarks that we have installed as proposed in the paper.As the α-divert is inserted second in the first period of
extraction we check the picture has been harmed or not with the assistance of the α-channel implanted. The pixel's
normal estimations of the given picture will be contrasted with α-channel. On the off chance that the normal for pixel
qualities has been harmed it would essentially recognize that the picture has been harmed. We will be separating the α -channel and contrasting it and the present normal pixel values in order to figure out the harmed pixels of the image. Implemented algorithms are:-
1] Messy Algorithm
2]Chaos encryption algorithm
Messy Algorithm:- In Messy Watermarking the framework progressively create the watermark utilizing chaotic framework which is remarkable for each picture.The produced watermark is then implanted in the _rst picture by growing the pixel's distinctions pair shaped in intra shading planes of the pictures.
Chaos encryption Algorithm:-
It will be developed to improve the robustness and protection along with security.Two watermarks are embedded in the host image. The secondary is embedded into primary watermark.This provides an e_cient and secure way for image transmission. The reliable watermark extraction scheme is developed for the extraction of the primary as well as secondary watermark from the distorted image.
Fig. Messy System
V. EXPERIMENTAL RESULTS
Image get secured successfully by implementing Dual watermark technique.Messy algorithm provides primary security to image. Secondary watermark by creating alpha channel provides extra protection to the image.So that chances of image alteration after attack get reduced.
Extraction and verification process detects the altered part of the image if there is any.This process uses Messy algorithm in reversed manner to remove the watermark by means of comparison with original values.
VI. CONCLUSION AND FUTURE WORK
The proposed strategy utilizes double watermarking plan for copyright security of picture as well as recuperation of picture. It produces both the watermarks progressively. The watermarks produced are interesting for each picture. We are implanting the First watermark with the assistance of pixel contrast development of different planes. The second watermark would be containing the pixel's normal estimations of picture. On the off chance that it is distinguished that picture is tempered than it is recouped utilizing alpha channel, however recuperated picture will be a grayscale picture. The framework would have the capacity to deliver preferred results over the frameworks proposed before as it uses double watermarking and consequently, help us to shield the picture from its unapproved utilization. No one can changes the original images which are uploaded on internet. Watermark can be extracted without any type of loss of original image. Embedded watermark in the system would not be removed by commonly used image processing techniques. Original image is going through many embedding process, so it is hard to edit or making changes to it. The platform for this image is android because lot of people used this phone so anyone can load image for security purpose.
VII. ACKNOWLEDGEMENT
We would like to thank Prof. Darshana R. Patil for their helpful discussion and feedback. This study was supported by Computer Department of Jayawantrao Sawant College Of Engineering ,Hadapsar ,Pune ,India.
REFERENCES
[1] S.Poonkuntranl and R.S.Rajesh‖ A Messy Watermarking for Medical Image Authentication‖. IEEE, 2011.
[2] Rongrong Ni, QiuqiRuan, Yao Zhao, "Pinpoint authentication Watermarking based on a chaotic system", Forensic Science International Journal,VoI.No: 179.
[3] J. Tian. ‖reversible watermarking by difference expansion‖.IEEE, 2002.
[4] R. S. Poonkuntran and P. Eswaran.‖analysis of difference expanding method for medical image watermarking‖. IEEE Explore, 1, 2011.
[5] A. M. Alattar. ‖reversible watermark using the difference expansion of a generalized integer transform,‖ IEEE, 2003.
[6] Jun Tain . ―Reversible Watermark by Difference Expansion‖
[7] H. Maitre B. S. Y. R. R. C. G. Coatrieux. ‖relevance of watermarking in medical imaging, in information technology applications in
biomedicine,‖ IEEE, 2000.
[8] R. Dhanalakshmi and K.Thaiyalnayaki,‖ Dual Watermarking Scheme with Encryption,‖ (IJCSIS) International Journal of Computer Science
and Information Security,Vol. 7, No. 1, 2010.
[9] Che-Wei Lee and Wen-Hsiang Tsai.‖ A New Lossless Visible Watermarking Method via The use of The PNG Image,‖.