DOI : https://doi.org/10.32628/CSEIT1953129
Security and Challenges for Wireless Sensor Network
T. Sri Nandini
M. Tech Scholar, Department of Information Technology, Sreenidhi Institute of Science and Technology, Hyderabad, Telangana, India
ABSTRACT
Wireless Sensor Network security challenges and defences techniques are presented for protection of authenticity integrity, confidentiality and availability of transmission against malicious wireless attacks. Wide range of Wireless attacks and security threats at different layers. Due to the sensitive nature of the data gathered by many wireless sensor network (WSNs)it is becoming more difficult to protect the data. This paper analyzes security requirements in wireless sensor network and it facing more attacks and threats, we also discuss the open challenges in the Software Defined Network.
Keywords : Wireless Sensor Network, SDN, Security challenges, Attacks, Security issues.
I. INTRODUCTION
Wireless Sensor Networks(WSNs) have a considerable of ideal conditions including movability, less proportion of configuration lines, simplicity of essentialness and versatile that has made flexible remote frameworks obvious the world. WSN needs to deal with the whole security centres from the legacy Internet, while contemplating the inadequacy of the remote resource compelled centre points additionally and including the usage cases specifically. WNS centre points are completely settled, limited source control and don't consider the business condition, including inertness, resolute quality and flexibility. The use of flexible centre points in mechanical structure have been growing the mobile phones, contraptions movability and versatility are improved. A tremendous of WSNs features are brought into IWSN, including some correspondence shows similarly as certain mechanical application .The present development improvement is Industry 4.0 ,it is use as the new modernized current advancement .This development is even more commonly associated and its specific help is a huge of
focal development advance, for example, cloud, Industrial Internet of Things, Cyber security ,Big data, and so forth. By and by a days, Industrie 4.0 has been attracting progressively more thought from educational systems to various associations in perspective on its central focuses which are that can decrease the imperativeness usage, raise fiscal focal points, and enables sharp creation. "Industrie 4.0" begins from an endeavour in the creative arrangement of the German government, which is the present example of computerization and data exchange gathering headways.
Programming Defined Network (SDN) is a framework perspective made to adjust to the trademark confinement and the nonattendance of versatility looked by the currentregular framework management. SDN is a framework development where orchestrate the board is made more straightforward and empowers it to be progressively controlled, changed and conduct oversaw through a strategy called organize programmability.
We as a whole work the appearance cautioning strategy to make case of the heterogeneous arrangement mixing small receptors just as actuators alongside normal execution processing components. Your Ask names with respect to Instantaneous Expression of alert Procedure are normally blended due to accommodation so as to smaller scale sensors just as low-control prompt interchanges. As opposed to the main receptors, from the separated cautioning strategy, huge accumulations with respect to are normally for the most part sent. These sorts of caution hubs may perhaps complete significant show handle, estimations, just as technique self-arrangement to attempt and do versatile, supportive just as seemingly perpetual systems [2]. Unmistakably more especially, cautioning hubs can perform confined handle to bring down deals and showcasing correspondences, and for that reason, quality expenses. We're feeling that numerous accommodating and adaptable bearing discovering items with respect to WSN is really frenzy concentrated arranged model. For any gathering concentrated cautioning strategy, a franticness development demonstrates a huge angle to the sum decrease, when request talks about the purchasing cost of therapeutic just as upkeep from the notice systems. Since archive, the vast majority ought to at present have an undeniably inside and out query with safeguard all through WSN and see family table measures.
II. LITERATURE REVIEW
[1] A.M.Abu-Mahfouz and G.P. Hancke,
WSNs are made of smaller scale sensors which are equipped for observing physical and ecological elements. The elements like temperature, humidity, vibrations, motions, seismics events,etc.
[2] A.M.Abu-Mahufouz, G. Hancke, S.Isacc The remote interfaces of WSNs permits the advancement of specially appointed systems without setting up physical foundation or focal administration heretofore.
[3]A. De Gante, M. Aslan, A. Matrawy
The localization of the hubs comprises key segments for a few WSNs application .The information of the hubs position makes it simple to expand progressively helpful and basic capacity, for example, the particular region detecting just as the improvement of system proficiency.
[4]S.Sharma, R.K. Bansal, and S. Bansal WSNs as a system innovation is utilized to facilitate the space between the physical world human and the virtual universe of electronic gadgets like PCs.
[5]M.J.Mudumbe andA.M.Abu-Mahfouz WSNs significance lies on the way that they have a great deal of potential to proffer practical answer for issue, for example, Smart city, Smart Grid and Smart Water System, military, restorative.
[6]S.Sezer, S.Scott-Hayward and P.Chouhan Programming Defined Network (SDN) is a system worldview created to adapt to the characteristic impediments and the absence of adaptability looked by the current traditional organize the board.
[7] K.Bakshi, Software Defined Network is a system innovation where organize the executives is made simpler and enables it to be progressively controlled, changed and conduct oversaw through a strategy called arrange programmability.
PC organize, when SDN worldview joins WSNs, it show to over again arrange worldview called programming Defined sensor Network.
[9] H.I.Kobo, A.M.Abu-Mahfouz and G.P.Hancke The significant utilization of WSNs, it is imperative that WSN is verified in WSN constitutes a difficult undertaking when looked at security in other system. [10]X.Du and H.Chen,
These assaults are not the same as assaults that are regular to specially appointed system on the premise that sensor hubs are neglected, paying little heed to these difficulties, security stays significant and imperative for a considerable lot of sensor arrange. [11] N.Ntuli and A.M.Abu-Mahfouz SDWSN isn't exempted from security challenges and has restricted its tasks and selection. WSNs are helpless against security dangers and are related with numerous security challenges.
[12] J. Stankovic
Extreme security dangers exists in WSN because of the way that sensor arrange communicate intimately with their physical condition and with individuals ,thecuuent security component are lacking to adapt to restrictions and complexities looked by WSNs
[13] Chiu, Hon Sun, and King-Shan Lui. "DelPHI: Openness picks regardless of whether any hub highlights the limit utilize these arrangements alongside in the occasion the procedure can be found to the gadgets so as to impart. Regardless, disappointment including underneath divide just as group pioneer's accommodation may step by step caution the total criminal alert system.
[14] C. Siva Ram Murthy and B.S. Manoj
It occurs by the unexpected disappointment of hubs or malignant activities. the least complex DoS assault endeavours to debilitate the assets accessible to the injured individual hub, by sending additional unessential parcels and in this way anticipates genuine system clients from getting to administrations or assets to which they're entitled. [15] IbrahimM .M. ElEmary S.Ramakrishhnan.
These sorts of assaults are exceptionally hard to shield against one class of conventions impervious to these assaults is geographic directing conventions. On interest, geographic conventions build a topology utilizing just restricted cooperation and without commencement from the base station.
[16]V. Nagarajan and D. Huang,
It empowers a few hubs to get to a typical shared medium utilizing a few access control instruments that incorporates CDMA, OFDMA, CSMA/CA, etc. Every hub has a one of a kind Macintosh address and a system interface card for client validation. Enemy may dispatch MAC ridiculing assault by changing the appointed MAC address
III. WIRELESS SENSOR NETWORK SECURITY
At the point when the specific caution framework sites additionally can lead in the impromptu methods the security objectives protect similarly as these sorts of on the regular sites and furthermore objectives perfect for the essential imperatives with specially appointed alert framework systems. The security objectives are arranged while essential and other [1]. The key objectives will be frequently called standard shields objectives like regarding precedent Privacy, Energy, Proof and furthermore Induction (CIAA). Additional objectives will be Information Flavour, Self Organization, Period Synchronization and furthermore Shielded Limitation. The key objectives will be:
A. Mindfulness Secrecy
It is really the ability to pay gadgets by a solid work out free foe to ensure that for all intents and purposes any this implies raised through the home security framework remains classified. That truly is one of fundamental damage in procedure safety.
B. Mindfulness Acceptance
Affirmation guarantees the implication in this implies through distinguishing their own starting point. Difficulties inside robber alert sites total not just required the customization including bargains; enemies maybe give included impersonation bargains [14]. A mindfulness capability agrees with this acknowledgment in the senders alongside collectors. An mindfulness capability is really accomplished by method for symmetric just as hilter kilter angles in which giving alongside gaining hubs show basic keys. Since the prompt distinction in the snap and furthermore the without treatment, singularity including thief alert sites, them is incredibly testing to be sure verification.
C. Learning Toughness
Mindfulness steadfastness inside criminal caution sites is required to guarantee the soundness including the information alongside finds the ability to make certain any this implies has not been hindered alongside, altered just as changed. In spite of the fact that the procedure highlights mystery forms, there might be in any case doable for the information steadfastness is affected by adjustments. The real life span of the machine may simply be inside monstrous problem at whatever point:
1) Any perilous hub from the procedure positions impersonation information.
2) Shaky conditions coming about because of prompt choice set off wounds just as nonattendance of information [4].
D. Mindfulness Accessibility
Availability picks regardless of whether any hub highlights the limit utilize these arrangements alongside in the occasion the procedure can be found to the gadgets so as to impart. In any case, disappointment including underneath divide just as group pioneer's comfort may steadily caution the total criminal alert system. Hence comfort is really including essential significance to get supporting a solid working.
E. Knowledge Taste
Despite the fact that mystery and information trustworthiness are more often than not persuaded, there might be a craving obviously to guarantee the evaluation of every message. Casually, mindfulness top quality [2] guarantees that the information is totally, yet it guarantees which sum past gadgets are really repeated. To end this specific test each nonce, just as once again related lounge area table, might just be included for the arrangement to be sure mindfulness freshness.
F. Self-Organization
A prompt home security framework is essentially a frequently a proposal hoc process, which thus necessities each thief caution hub frequently be unmistakable alongside differing bounty of acting naturally sorting out alongside self-recuperating preceding numerous circumstances. You will discover sum repaired structure out there the point of procedure activities inside an alarm arrange. Of which solid work gives an incredible issue so as to quick home security framework security. If self-association is really without the need of a caution process, the harm the after-effect of a solid hit together with the hazardous setting up may in all likelihood be dangerous.
G. Event Synchronization
A ton of house security framework relevance depends on a few type of minute synchronization. Significantly more in overabundance of, receiving devices should make sense of this start to finish resist of and give for the most part since it systems in the middle of a couple of pair shrewd sensors. A substantially more shared house security framework could read for sequence of events synchronization [4] to get directing relevance.
H. Protected Localization
delivered to find flaws needs appropriate territory records as an approach to decide this area of a deficiency. In any case, a rival can without much of a stretch rapidly changesno secured zone records through divulging impersonation connote points of interest, replaying signals.
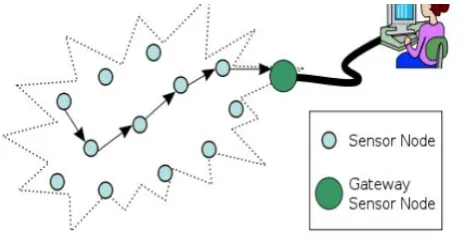
Fig 1: wireless sensor network
IV.ATTACKSIN SENSOR NETWORKS
WSNs will be inclined to different assault. As per the strength needs all through WSNs, these sorts of issues are regularly named seeing that [3]:
A. Strikes upon mystery in addition to affirmation Commonplace cryptographic methods can protect the real mystery in addition to authenticity with imparting stations out of outcast issues simply like spying, box replay issues, in addition to customization just as parodying with parcels.
B. Strikes upon network openness
Strikes upon network openness: issues upon availability will be otherwise called refusal of-administration (DoS) assaults. DoS issues may maybe objective any sort of layer of cell of your marker organizes.
C. Playing
Playing is a term attack that meddles utilizing the r/c wavelengths a system's hubs are applying [3, 5]. Any unit of data mention can end up solid a lot of so as to trouble the full network just as a lesser measure of solid also, just in the situation to trouble a diminished
zone of the organize. Regardless of having lesser-controlled blocking choices, for example a minimized seriously yielded part from the system's pointer hubs, an incredible foe offers the conceivable approaches to trouble the full network outfitted your blocking alternatives are for the most part with little considered gave while in the system. Standard rights by blocking involve variations including spread-range transmission like volume hopping alongside rule dissipating [4]. Recurrence jumping proliferate choice (FHSS) is generally a system for moving motivations essentially by expediently moving over your pack in the midst of a few volume programs using a pseudo subjective example perceived to either transmitter alongside beneficiary.
D. Tampering
An alternate real dimension attack is really altering [5]. Offered in essence utilization of another hub, a rival can surely make easily affected realities for example cryptographic vehicle keys or on the other hand some other data to the hub. The genuine hub are frequently overhauled or maybe contract out to build up a lost hub that this adversary controls. An individual defend to that ambush comprises of sealing the genuine hub's real offer [9]. All things being equal, as a rule speculated the way that sensor hubs generally are not sealed inside WSNs as an outcome of more expense. The accompanying focuses to a criminal program should consider the situation by which detecting unit hubs will in general be undermined.
E. Sinkhole
guests from your gigantic spot inside staggered is going to flow from the foe's hub.
F. Sybil
Your Sybil hurt is really a case where by only one hub uncovers a couple of id to your staggered [3]. Techniques and furthermore calculations which more often than not are normally exasperates join issue tolerant plans, designated extra room, and furthermore network topology upkeep. One model is, any allotted stockpiling space erected could retreat on the site turning into a few indistinguishable precisely the same realities so as to pick up an exhibited larger amount of repetition. In the event that a lost hub claims to get two or three a couple of the hubs, a calculations used could consider this excess have been cultivated while very are most certainly not.
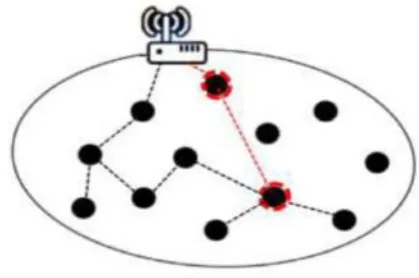
G. Wormhole
Your wormhole can be low-inaction after effects of two or three zones of your circle that an attacker replays circle mail messages [16]. That web association could be seen both by strategies for one explicit centre sending letters messages including a couple of adjacent in spite of the fact that if not non-neighbouring hubs or perhaps by methods for two or three hubs around your circle messaging every one other. Previously mentioned situation will be eagerly comparative for the sinkhole attack, as a conceivable moving toward hub alongside the base stop can positively give you a one-jump back connection to which beginning quit utilizing the elective moving toward hub in the distant territory of the arrange. Hu ainsi que al. offered any story notwithstanding fundamental gadget known as little fortune prompts get uncovering in expansion to securing towards wormhole issues [8].
Fig 2 : shows wormhole attack
V. CONCLUSION
This paper displays a few security difficulties of SDWSN that starts from the viewpoint of WSN and SDN. The paper likewise examines a few existing countermeasures and existing proposed arrangements that can be utilized to relieve those security challenges. The paper studied and performed security examination of the inheritable security challenges looked by the system worldview of SDWSN.
Accordingly, instruments to alleviate security assaults in SDWSN must be planned and actualized. Security model/system must be intended to secure the whole system, the controller plane, the sensors and the conventions utilized for correspondence inside the system. This is essential to guarantee that SDWSN is verified and reliable, increase across the board pertinence.
VI. REFERENCES
[1]. M. Abu-Mahfouz and G. P. Hancke, "Confined Information Fusion. Systems for Location Discovery in Wireless Sensor Networks," Int.J. Sens. Frameworks, 2017.
[3]. A. De Gante, M. Aslan, and A. Matrawy, "Splendid remote sensororganize the administrators reliant on programming portrayed arranging," (QBSC), 2014 27th Bienn. 2014.
[4]. A. M. Abu-Mahfouz and G. P. Hancke, "ALWadHA Localisation Calculation: Yet More Energy Efficient," IEEE Access, vol. 5, no. 5, pp. 6661– 6667, 2017.
[5]. S. Sharma, R. K. Bansal, and S. Bansal, "Issues and Challenges inWireless Sensor Networks," in International Conference on Machine Insight and Research Advancement, 2013, no. July, pp. 58– 6.
[6]. A. M. Abu-Mahfouz, T. Olwal, A. Kurien, J. L. Munda, and K. Djouani, "Toward structure up an appropriated self-decision imperativeness the board system (DAEMS)," in IEEE AFRICON 2015, 2015, pp. 1– 6.
[7]. A. M. Abu-Mahfouz, Y. Hamam, P. R. Page, and K. Djouani, "Realtime dynamic weight driven model for consumable water disaster decline," Procedia Eng., vol. 154, no. 7, pp. 99– 106, 2016.
[8]. M. J. Mudumbe and A. M. Abu-Mahfouz, "Splendid water meter frameworkfor customer driven usage estimation," in Proc. of the IEEE Worldwide Conference on Industrial Informatics, 2015, pp. 993– 998.
[9]. S. Sezer, S. Scott-Hayward, and P. Chouhan, "Would we say we are set up for SDN? Execution challenges for programming described frameworks," IEEE, 2013.
[10]. T. Grandison and M. Sloman, "A survey of trust in web applications," Commun. Surv. Instructional activities, 2000.
[11]. M. Ndiaye, G. P. Hancke, and A. M. Abu-Mahfouz, "Programming Defined Systems organization for Improved Wireless Sensor Network Management: A Review," Sensors, vol. 17, no. 5: 1031, pp. 1– 32, 2017.
[12]. K. Bakshi, "Thoughts for programming described arranging (SDN) Methodologies and use cases," IEEE Aerospace Conference, 2013, pp. 1– 9.
[13]. Chiu, Hon Sun, and King-Shan Lui. "DelPHI: wormhole area framework for extraordinarily named remote frameworks." Wireless inevitable enrolling, 2006 first overall symposium on. IEEE, 2006.
[14]. C. Siva Ram Murthy and B.S. Manoj "Building remote M2M and IoT sensor frameworks: issues and troubles".
[15]. Wireless Sensor Networks and Applications (Book) changed by Ibrahiem M. M. El Emary, S.Ramakrishhnan.
[16]. N. Ntuli and A. M. Abu-Mahfouz, "A Simple Security Architecture for Savvy Water Management System," Procedia Comput. Sci., vol. 83, no. 4, pp. 1164– 1169, 2016. "Evaluating ALWadHA for giving secure localisation to remote sensor frameworks," in IEEE AFRICON Conference, 2013, pp. 501– 505.
[19]. J. Stankovic, "Investigation challenges for remote sensor frameworks," ACM SIGBED Rev., 2004.
[20]. Y. Zhou, Y. Tooth, and Y. Zhang, "Checking remote sensor orchestrates: an audit," IEEE Commun. Surv. Instructional activities, vol. 10.3, no. APA, 2008.
[22]. D. De, O. Gonçalves, and D. G. Costa, "A Survey of Image Security in Wireless Sensor Networks," J. Imaging, vol. 1, pp. 4– 30, 2015. [23]. O. Cheikhrouhou, "Secure Group
Communication in Wireless Sensor Systems: An audit," J. Netw. Comput. Appl., vol. 61, pp. 115– 132, 2016.
[24]. M. Jacobsson and C. Orfanidis, "Using Software-described Networking Standards for Wireless Sensor Networks," in eleventh Swedish National PC Networking Workshop, 2015, no. Sncnw.
[25]. T. Luo, H. Tan, and T. Q. S. Quek, "Sensor OpenFlow: Enabling Programming Defined Wireless Sensor Networks," pp. 2– 5, 2012. [26]. C. Chaudet and Y. Haddad, "Remote
programming described frameworks: Difficulties and openings”, Commun. Recieving wires 2013.
[27]. H. Farhady, H. Lee, and A. Nakao, "Programming described sorting out: An audit," Comput. Frameworks, 2015.
[28]. M. Jammal, T. Singh, A. Shami, R. Asal, and Y. Li, "Programming described sorting out: State of the craftsmanship and research troubles," Comput. Frameworks, 2014.
[29]. J. Chen, X. Zheng, and C. Rong, "Survey on programming described arranging," Int. Conf. Cloud Comput., 2015.
Cite this article as :
T. Sri Nandini, "Security and Challenges for Wireless Sensor Network", International Journal of Scientific Research in Computer Science, Engineering and Information Technology (IJSRCSEIT), ISSN : 2456-3307, Volume 5 Issue 4, pp. 42-49, July-August 2019.
Available at doi :
https://doi.org/10.32628/CSEIT1953129