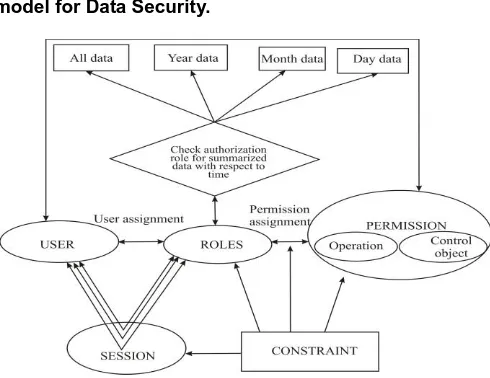
Modified Role Based Access Control Model For Data Security
Full text
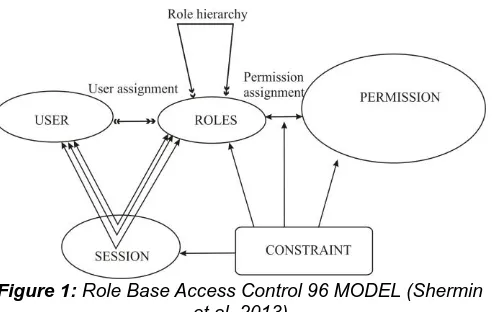
Figure
Related documents
Hypothesis 4b: Increased levels of organizational constraints aggregated to the unit-level (Level 2) will be associated with individual-level (Level 1) decreased supervisor-rated
VA mental health services are available in specialty clinics, primary care clinics, nursing homes, and residential care facilities where Veterans receive health care.. Specialized
In this document we proposed to build a Configuration Management Database and how to implement an ITIL Change Management process, including the development of a prototype to support
Box plots of mean right submandibular gland (a), left submandibular gland (b), right parotid gland (c), and left pa- rotid gland (d) shear wave velocity (SWV) values in
However, these points are not reliable enough to be used in ICP registration if the capture points are far from each other because two possible sources of errors exist: errors in
Semantic correspondence methods based on CNNs use different training sets. Following these approaches, we train a network on the.. training split in the PF-PASCAL dataset. We
As Nick envisages the moment of Gatsby’s death he is challenging a distinctly American definition of failure where Gatsby takes the outline of a new modern hero.. Here I would