Coffee and caffeine intake and risk of urinary incontinence: a meta-analysis of observational studies
Full text
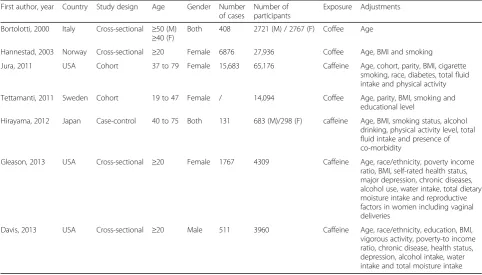
Figure



Related documents
In this study molecular docking and docking analysis was performed using molegro software which were used to predict and understand between alpha amylase
From the early 1970’s on the HAFC had acquired a variety of treatment grants to fund its services (Seymour & Smith, 1986). During the 80’s and 90’s the clinic broadened its
routes of the armies of general john sullivan and james clinton 1779 an expedition against the hostile indian nations which checked the aggressions of the english and indians on
photoluminescence properties, FT-IR, UV-vis absorption spectra, fluorescence lifetime and fluorescence quantum yield of TCPP were also reported in this paper. To gain deeper
The synthesis, characterization and antimicrobial activities of Cr2O3 NPs against Klebsiella pneumoniae had been studied and observed that the bacterial growth reduces
Around the world, initiatives are being taken to replace gasoline and diesel fuel due to the impact of the fossil fuel crisis, increase in oil price, and the adoption of
From (10), it can be observed that the torque dynamics depends on the variation of . Hence, fast torque control can be achieved by rapidly changing ‘ ’ in the required
Searching in the literature it is found that there have been applied a lot of methodologies to solve the NSLP but few of these methodologies were applied on real networks, such
