Perceptions About Data Security For Portable Storage Devices
Full text
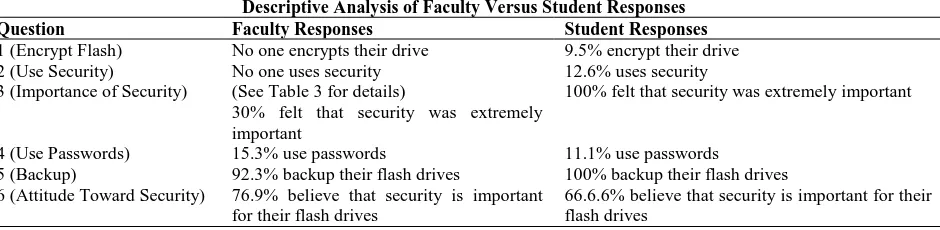
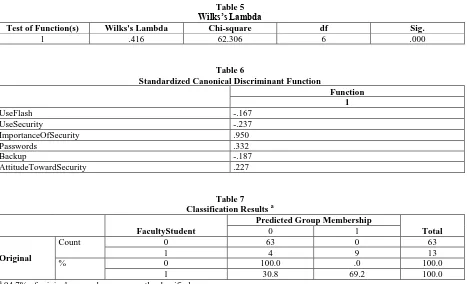
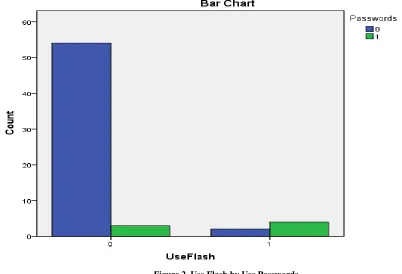
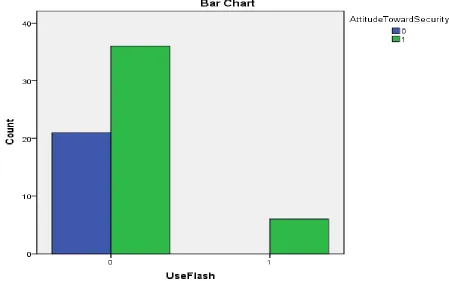
Figure
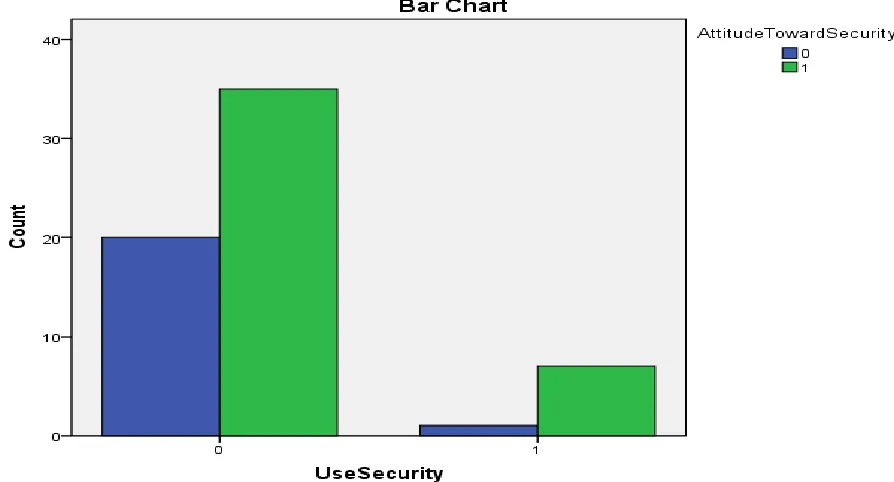
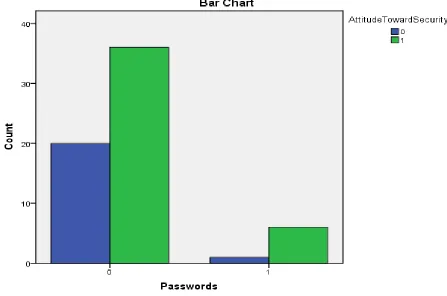
Related documents
Traveler Mode is now complete and if you check the Pen Drive in Windows Explorer you will find a folder named TrueCrypt containing the files required to run Traveler Mode.
With Verbatim Secure Data USB Drive and your portable storage device you can simply copy data on your Verbatim Secure Flash Drive and it will be automatically encrypted
The Data Encryption Policy (the Policy) defines the security operational requirements of the CCG to secure all data held upon portable computing devices, portable storage devices and
The Central Processing Unit (CPU) performs program control and data processing Storage devices include memory and secondary storage (e.g., a USB Flash Drive).
government and to meet the needs of those who transport secret corporate data, an IronKey flash drive (aka/ ‘USB drive,’ or ‘thumb drive’) is the most secure portable data
Stealth MXP Passport is ideally suited for organizations that prefer a password-based secure encrypted USB flash drive to satisfy the need for secure portable storage, identity,
NUIT recommend that the storage of sensitive and confidential data on portable storage devices is risk assessed and authorised by the relevant manager such as the data
USB-based portable flash memory drives, also known as “thumb drives” or “USB sticks” provide quick storage and transport of files. They connect to a USB port on most laptop