Proxy Signcrypion Scheme Based on Hyper Elliptic Curves
Full text
Figure
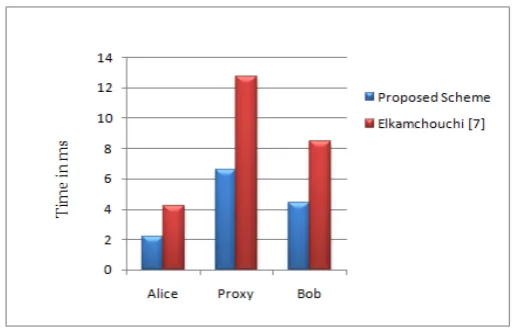
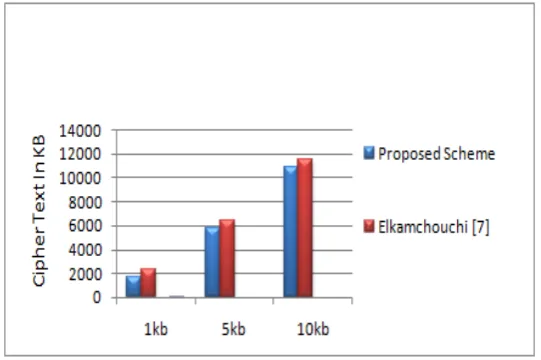
Related documents
the present study between utility score and patient age, clinical signs, results of serum biochemistry 263. and type of diarrhoea, hence it is not possible to make
In addition to these parameters, the second order statistical parameters from the Gray level co-occurrence matrix of the texture [20]: contrast, energy,
- Provide analysis of student’s performance in every semester - Provide learning path for student based on duration of completion - Provide an updated learning path diagram for
Therefore, poly(methyl methacrylate) (PMMA) grafted to the chitosan beads was proposed to overcome the limitation of chitosan beads by reducing the hydrophilic
• Make sure the telephone line cord is plugged firmly into the base unit and the telephone wall jack.. • Make sure the battery is
An encryption algorithm for EM is said to be passively secure if the protocol it induces realizes Ideal Disk securely against admissible passive adversaries, furthermore the ideal
Hence, in addition to the first stateless standard-model SU-CMA signature scheme from lattices in Section 4.1, we provide the first direct lattice-based constructions for
Abstract —The problem of electromagnetic waves radiation into a space outside a perfectly conducting sphere through a narrow slot, cut in an end-wall of a semi-infinite